Leaky database two factor codes – Leaky databases: two-factor codes under threat. It’s a scary thought, isn’t it? Imagine your most secure logins, the ones you thought were safe behind two-factor authentication, suddenly vulnerable. But this isn’t a far-fetched sci-fi scenario; it’s a very real danger lurking in the digital shadows. Think about it – your two-factor codes, those precious keys to your online kingdom, are stored somewhere. And what if that storage isn’t as secure as you thought?
The truth is, leaky databases are a growing threat. Hackers are constantly finding new ways to exploit vulnerabilities, and two-factor codes are becoming an increasingly attractive target. From malicious insiders to sophisticated phishing attacks, the methods are varied, but the outcome is the same: your accounts, your data, and your privacy are at risk.
Understanding the Threat
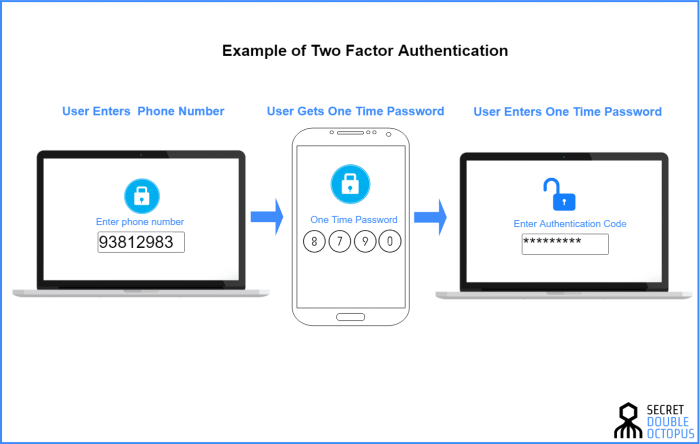
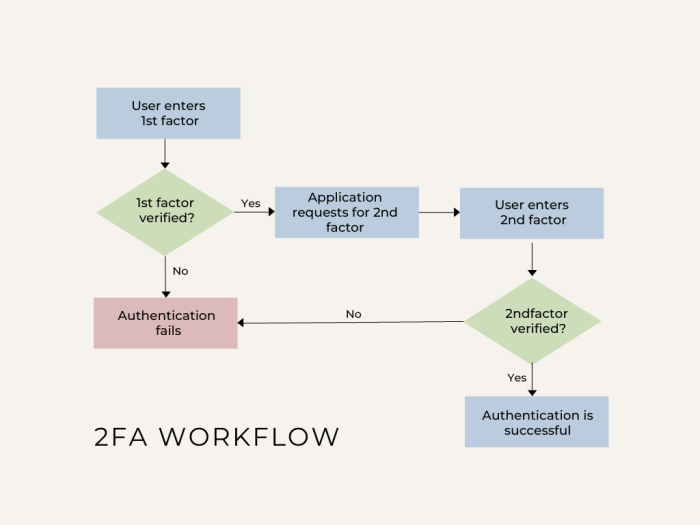
Two-factor authentication (2FA) is a vital security measure that adds an extra layer of protection to your online accounts. It requires you to provide not only your password but also a unique code generated by an authenticator app or sent to your phone. However, even with 2FA in place, your accounts can be vulnerable if the database containing your 2FA codes is compromised.
This is because hackers can use stolen codes to bypass 2FA and gain access to your accounts, even if they don’t know your password.
Real-World Examples of Data Breaches Involving Two-Factor Codes
Data breaches involving two-factor codes have become increasingly common in recent years. Here are a few notable examples:
- 2022: LastPass – LastPass, a popular password manager, experienced a data breach in which hackers gained access to a database containing encrypted passwords and 2FA codes. While LastPass claims that the 2FA codes were encrypted, the breach highlights the vulnerability of storing 2FA codes in a centralized database.
- 2021: Clubhouse – The audio-based social media platform Clubhouse suffered a data breach that exposed user data, including phone numbers and email addresses. This information could have been used to target users with phishing attacks or to bypass 2FA by obtaining access to their phones.
- 2020: Twitter – Twitter experienced a security breach in which hackers gained access to accounts belonging to high-profile individuals, including politicians and celebrities. The hackers used stolen 2FA codes to gain control of these accounts, demonstrating the potential for serious damage if 2FA codes are compromised.
Impact on Individuals and Organizations
If your two-factor codes are compromised, the consequences can be severe, including:
- Account Takeover: Hackers can gain access to your online accounts, such as your email, banking, or social media accounts, and use them for malicious purposes.
- Financial Loss: Hackers can steal your money from your bank accounts, credit cards, or other financial services.
- Identity Theft: Hackers can use your stolen information to open new accounts in your name, apply for loans, or commit other forms of identity theft.
- Data Leaks: Hackers can access sensitive information stored in your accounts, such as your personal data, financial records, or confidential business information.
- Reputational Damage: Organizations that experience a data breach involving 2FA codes can suffer reputational damage, leading to a loss of trust from customers and partners.
Causes of Leaky Databases: Leaky Database Two Factor Codes
Leaky databases are a serious security threat that can expose sensitive information, including two-factor authentication codes. These codes are crucial for securing accounts, and their leakage can lead to unauthorized access and identity theft. Understanding the causes of leaky databases is essential for preventing such breaches.
Vulnerabilities Leading to Data Leaks
Common vulnerabilities that can lead to databases leaking two-factor codes include:
- Weak or Default Credentials: Using default passwords or weak credentials for database access can make it easy for attackers to gain unauthorized access.
- Insecure Configurations: Misconfigured databases, such as those with open ports or permissive access controls, can expose data to unauthorized users.
- Unpatched Software: Outdated database software may contain vulnerabilities that attackers can exploit to gain access to sensitive data.
- SQL Injection: Attackers can use SQL injection techniques to bypass security measures and access sensitive data.
- Cross-Site Scripting (XSS): XSS attacks allow attackers to inject malicious scripts into websites, which can then be used to steal user data, including two-factor codes.
Types of Attacks Exploiting Vulnerabilities
Various types of attacks can exploit these vulnerabilities to gain access to databases and steal two-factor codes:
- Brute-Force Attacks: Attackers can use automated tools to try different combinations of passwords until they gain access to a database.
- Credential Stuffing: Attackers use stolen credentials from other data breaches to try to access databases.
- Man-in-the-Middle (MitM) Attacks: Attackers intercept communication between users and websites to steal sensitive information, including two-factor codes.
- Social Engineering: Attackers use deception and manipulation to trick users into revealing sensitive information, such as their two-factor codes.
Best Practices for Securing Databases
Implementing robust security measures is crucial to prevent database leaks and protect two-factor codes:
- Strong Passwords and Access Control: Use strong, unique passwords for all database accounts and implement strict access control measures.
- Regular Security Audits: Conduct regular security audits to identify and address vulnerabilities.
- Database Encryption: Encrypt sensitive data, including two-factor codes, to protect it from unauthorized access.
- Regular Software Updates: Keep database software up to date with the latest security patches.
- Two-Factor Authentication (2FA): Implement 2FA for all database access to add an extra layer of security.
Impact of Leaky Databases
A leaky database containing two-factor authentication (2FA) codes can have severe consequences, leading to account takeovers, identity theft, and reputational damage. Imagine a scenario where a hacker gains access to a database holding 2FA codes, they can easily bypass the security measures and gain unauthorized access to sensitive accounts.
Account Takeovers
A leaky database containing 2FA codes poses a significant threat to user accounts. Hackers can exploit this vulnerability to bypass 2FA security and gain unauthorized access to user accounts. Imagine a hacker obtaining a list of 2FA codes from a leaked database. They can then use these codes to log into user accounts, potentially gaining access to sensitive information such as financial data, personal emails, and social media profiles.
Identity Theft
The theft of 2FA codes from a leaky database can have serious repercussions for users, potentially leading to identity theft. Once hackers gain access to user accounts, they can use the stolen information to commit identity theft. This can involve accessing personal information, such as credit card details, social security numbers, and addresses, which can be used for fraudulent activities, such as opening new credit accounts or making unauthorized purchases.
Impact on User Trust and Reputation
Leaky databases can severely impact user trust and the reputation of the organization responsible for the data breach. When users discover that their 2FA codes have been compromised, they may lose trust in the organization’s ability to protect their data. This can lead to a decline in user engagement and loyalty, potentially damaging the organization’s brand image and customer relationships.
Mitigation Strategies
Preventing database leaks is crucial for safeguarding sensitive information and maintaining user trust. This section Artikels various mitigation strategies that can be implemented to protect databases from unauthorized access and data breaches.
Data Encryption
Data encryption plays a vital role in securing databases by transforming sensitive information into an unreadable format. Even if a database is compromised, encrypted data remains protected.
- Strengths:
- Provides a robust layer of security, making it difficult for attackers to access sensitive data.
- Compliant with data privacy regulations like GDPR and HIPAA.
- Weaknesses:
- Encryption keys must be securely stored and managed, as their compromise can negate the effectiveness of encryption.
- Encryption can add computational overhead, potentially impacting database performance.
Access Control
Implementing strict access control measures ensures that only authorized individuals can access specific data within the database. This involves assigning different levels of permissions based on roles and responsibilities.
- Strengths:
- Minimizes the risk of unauthorized data access by restricting user permissions.
- Enhances accountability by tracking user activities and access logs.
- Weaknesses:
- Requires careful planning and configuration to ensure proper permissions are assigned.
- Overly restrictive access control can hinder legitimate users from accessing necessary data.
Database Auditing
Regular database auditing helps identify potential vulnerabilities and suspicious activities. It involves analyzing database logs and configurations to detect any anomalies or unauthorized access attempts.
- Strengths:
- Provides insights into database usage patterns and potential security risks.
- Helps identify and address vulnerabilities before they can be exploited.
- Weaknesses:
- Requires specialized skills and tools for effective auditing.
- Large volumes of audit data can be challenging to analyze and interpret.
Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code generated by a mobile app.
- Strengths:
- Significantly reduces the risk of unauthorized access, even if passwords are compromised.
- Enhances account security and protects against brute-force attacks.
- Weaknesses:
- Can be inconvenient for users, especially if they frequently access the database.
- Requires robust infrastructure and secure communication channels for generating and verifying authentication codes.
Strong Password Policies
Implementing strong password policies is essential for protecting database accounts. This includes requiring users to choose complex passwords that meet specific criteria, such as length, character types, and complexity.
- Strengths:
- Makes it harder for attackers to guess or crack passwords.
- Reduces the risk of unauthorized access through brute-force attacks.
- Weaknesses:
- Users may find it difficult to remember complex passwords.
- Password complexity can hinder usability and increase the likelihood of users choosing weak passwords.
Regular Security Updates, Leaky database two factor codes
Keeping databases and related software up-to-date is crucial for patching vulnerabilities and mitigating security risks. Regular security updates address known security flaws and improve overall database security.
- Strengths:
- Fixes security vulnerabilities that could be exploited by attackers.
- Improves database stability and performance by addressing known bugs.
- Weaknesses:
- Updates may require downtime for database maintenance.
- Compatibility issues can arise if updates are not properly tested before deployment.
Database Monitoring
Continuous database monitoring is essential for detecting and responding to security threats in real time. This involves monitoring database activity, identifying suspicious patterns, and triggering alerts when anomalies are detected.
- Strengths:
- Provides real-time visibility into database activity, enabling early detection of threats.
- Helps identify and address security incidents before they cause significant damage.
- Weaknesses:
- Requires sophisticated monitoring tools and expertise to effectively analyze and interpret data.
- False positives can occur, requiring manual investigation and potentially leading to unnecessary alerts.
Data Loss Prevention (DLP)
Data loss prevention (DLP) solutions are designed to prevent sensitive data from leaving the organization’s network. They monitor data flows and identify potential leaks, blocking unauthorized data transfers.
- Strengths:
- Provides a robust layer of protection against data exfiltration attempts.
- Helps comply with data privacy regulations by preventing sensitive data from leaving the organization’s control.
- Weaknesses:
- Can be complex to configure and manage, requiring specialized expertise.
- False positives can occur, potentially blocking legitimate data transfers.
In the end, it’s about taking control. While leaky databases are a real threat, they’re not insurmountable. By understanding the risks, implementing strong security measures, and staying vigilant, you can protect yourself and your data from falling into the wrong hands. It’s not about living in fear, but about being smart and informed. So, buckle up, learn the ropes, and make sure your digital castle is impenetrable. The future of your online security depends on it.
Leaky databases exposing two-factor authentication codes are a nightmare for security, leaving users vulnerable. It’s a reminder that even with extra layers of protection, our data can be at risk. This situation highlights the importance of staying informed about security threats, just like the recent news about the techcrunch space good night odysseus project, which explored the potential dangers of space debris.
While different in scope, both scenarios demonstrate the need for proactive measures to safeguard our information in the digital age.
 Standi Techno News
Standi Techno News