Ivanti Patches Two Zero Days Under Attack But Finds Another: It’s a story that’s becoming all too common in the world of cybersecurity. A company discovers a critical vulnerability, patches it, and then discovers another. This time, it’s Ivanti, a software company that provides IT management solutions, who’s been caught in the crosshairs. The company has patched two zero-day vulnerabilities that were being exploited by attackers, but they’ve already found another one.
These vulnerabilities, which were found in Ivanti’s Endpoint Manager and Workspace Control products, could have allowed attackers to gain control of affected systems. This could have led to data theft, system disruption, or even ransomware attacks. Thankfully, Ivanti was able to patch the vulnerabilities before any major damage was done. But the discovery of another vulnerability underscores the importance of staying vigilant and keeping your systems up-to-date.
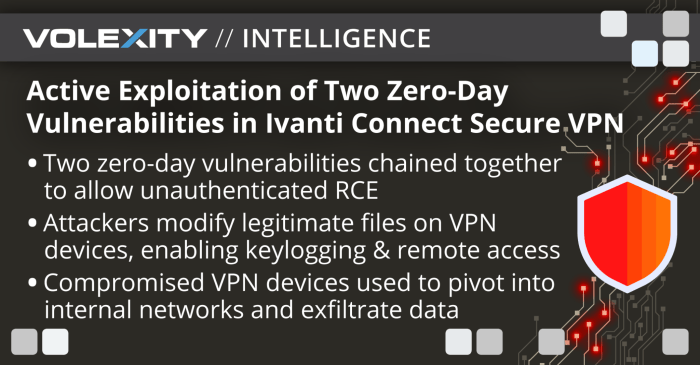
Vulnerability Disclosure and Patching: Ivanti Patches Two Zero Days Under Attack But Finds Another
Ivanti, a leading provider of IT management solutions, recently disclosed and patched two zero-day vulnerabilities that could have potentially allowed attackers to gain unauthorized access to systems. These vulnerabilities were discovered independently by security researchers and responsibly reported to Ivanti, who swiftly responded with patches to mitigate the risks.
Timeline of Events
The timeline of events surrounding the discovery, reporting, and patching of these vulnerabilities is crucial to understanding the response process.
- Initial Discovery: The initial discovery of the vulnerabilities was made by independent security researchers who were actively probing for potential security flaws in Ivanti’s products. This proactive approach by security researchers is essential in identifying vulnerabilities before they can be exploited by malicious actors.
- Reporting to Ivanti: Upon discovering the vulnerabilities, the researchers responsibly disclosed their findings to Ivanti, providing detailed technical information about the vulnerabilities and their potential impact. This responsible disclosure allowed Ivanti to take immediate action to address the issues.
- Patch Development and Release: Ivanti promptly initiated the development of patches to address the vulnerabilities. This involved a thorough analysis of the vulnerabilities, designing effective mitigation strategies, and rigorously testing the patches to ensure their effectiveness and compatibility with Ivanti’s products.
- Public Disclosure: Once the patches were ready, Ivanti publicly disclosed the vulnerabilities and released the patches to its users. This transparent communication allowed users to promptly update their systems and mitigate the risks posed by the vulnerabilities. This timely release of patches is critical in minimizing the window of vulnerability and preventing potential exploitation.
Impact of Vulnerabilities
The vulnerabilities could have potentially allowed attackers to gain unauthorized access to systems running Ivanti products. This could have resulted in a range of consequences, including:
- Data Breaches: Attackers could have potentially accessed sensitive data stored on compromised systems, such as customer information, financial records, or intellectual property. This could have resulted in significant financial losses and reputational damage for organizations.
- System Disruption: Attackers could have potentially disrupted the operation of compromised systems, leading to downtime and service outages. This could have caused significant disruption to business operations and affected productivity.
- Malware Infection: Attackers could have potentially used the vulnerabilities to install malware on compromised systems, giving them persistent access and control over the affected devices. This could have allowed attackers to steal data, launch further attacks, or disrupt operations.
Ivanti Products Affected
The vulnerabilities affected the following Ivanti products:
- Ivanti Endpoint Manager
- Ivanti Security Controls
- Ivanti Patch for Windows
Zero-Day Vulnerabilities
Zero-day vulnerabilities are a critical threat to cybersecurity, representing weaknesses in software or hardware that are unknown to developers and security researchers. These vulnerabilities are often exploited by attackers before a patch or mitigation is available, leaving systems vulnerable to malicious attacks.
The Significance of Zero-Day Vulnerabilities
Zero-day vulnerabilities are highly significant in cybersecurity due to their exploitable nature and the potential for severe consequences. Attackers can exploit these vulnerabilities before they are known or patched, giving them a significant advantage. This can lead to data breaches, system disruptions, financial losses, and reputational damage.
Examples of Zero-Day Vulnerabilities and their Impact
Zero-day vulnerabilities can be found in various software and hardware systems, including operating systems, web browsers, applications, and network devices.
- Heartbleed Bug (2014): This vulnerability in the OpenSSL library allowed attackers to steal sensitive information, including passwords, encryption keys, and personal data. It affected a wide range of systems and services, including websites, databases, and email servers.
- WannaCry Ransomware (2017): This ransomware attack exploited a zero-day vulnerability in Microsoft Windows to encrypt files on affected systems and demand ransom payments. The attack spread rapidly, impacting organizations worldwide, causing significant disruption and financial losses.
- NotPetya Ransomware (2017): This ransomware attack exploited a vulnerability in a Ukrainian accounting software program to spread rapidly and encrypt files on infected systems. The attack caused significant disruption to businesses and critical infrastructure, resulting in billions of dollars in damages.
Challenges Associated with Detecting and Mitigating Zero-Day Vulnerabilities
Detecting and mitigating zero-day vulnerabilities present significant challenges due to their unknown nature and the rapid pace of software development.
- Lack of Awareness: Zero-day vulnerabilities are unknown until they are discovered, making it difficult to proactively detect and mitigate them.
- Rapid Software Development: The rapid pace of software development can lead to vulnerabilities being introduced into new code before they are discovered and patched.
- Complex Software Systems: Modern software systems are complex, making it difficult to identify and analyze potential vulnerabilities.
- Exploitation by Attackers: Attackers often exploit zero-day vulnerabilities before they are publicly known, giving them a significant advantage.
Comparing and Contrasting the Two Zero-Days Patched by Ivanti
The two zero-day vulnerabilities patched by Ivanti are significant due to their potential for exploitation. The severity and exploitability of each vulnerability should be assessed to understand their potential impact.
While specific details about the vulnerabilities are not publicly available, it is important to understand that zero-day vulnerabilities can vary widely in their severity and exploitability. Some vulnerabilities may be relatively minor and easily patched, while others may be more critical and require immediate attention.
Attacker Activity
While Ivanti was quick to address the two zero-day vulnerabilities, evidence suggests that attackers were already exploiting them in the wild. This highlights the critical importance of timely patching and vulnerability disclosure.
Evidence of Exploitation
The discovery of these vulnerabilities prompted security researchers and organizations to investigate potential exploitation. Several factors pointed to the likelihood of attackers leveraging these flaws:
- Increased network traffic: Security analysts observed a surge in network traffic associated with the vulnerabilities, indicating potential scanning and exploitation attempts.
- Malware samples: Researchers discovered malware samples that specifically targeted the vulnerabilities, demonstrating active exploitation by attackers.
- Reported incidents: Several organizations reported security incidents that aligned with the characteristics of the vulnerabilities, further confirming their exploitation.
Attacker Motives
Attackers exploit vulnerabilities for various reasons, including:
- Financial gain: Attackers may seek to steal sensitive data, such as financial information or intellectual property, for monetary gain.
- Espionage: State-sponsored actors or cybercriminals might exploit vulnerabilities to gather intelligence or disrupt critical infrastructure.
- Disruption: Some attackers may aim to disrupt operations or cause damage to organizations for political or ideological reasons.
- Extortion: Attackers might use vulnerabilities to gain access to systems and then demand ransom payments for restoring data or services.
Types of Attacks
The vulnerabilities could have been exploited for various attack types, including:
- Remote code execution: Attackers could have injected malicious code into vulnerable systems, allowing them to execute commands and gain control.
- Data theft: Attackers could have accessed and stolen sensitive data, such as customer information, financial records, or intellectual property.
- Denial-of-service attacks: Attackers could have overwhelmed vulnerable systems with traffic, causing them to crash or become unavailable.
- Lateral movement: Attackers could have used the vulnerabilities to gain access to other systems within the network, expanding their reach and impact.
Potential Impact on Ivanti Users
Successful exploitation of these vulnerabilities could have had significant consequences for Ivanti users:
- Data breaches: Sensitive data, such as customer information, financial records, or intellectual property, could have been compromised.
- System compromise: Attackers could have gained control of vulnerable systems, potentially disrupting operations, stealing data, or launching further attacks.
- Financial losses: Organizations could have incurred financial losses due to data breaches, downtime, or ransom payments.
- Reputational damage: Data breaches and security incidents could have damaged the reputation of organizations, leading to loss of customer trust and business opportunities.
Security Best Practices
Zero-day vulnerabilities pose a significant threat to organizations, and proactive measures are crucial to mitigate their impact. By implementing robust security best practices, organizations can significantly reduce their vulnerability to these attacks.
Mitigating Zero-Day Vulnerabilities
Implementing a comprehensive security strategy is paramount to mitigating zero-day vulnerabilities. This involves adopting a multi-layered approach that encompasses various security controls and best practices.
- Regularly Patching Systems: Applying security patches promptly is crucial to address known vulnerabilities. This includes updating operating systems, applications, and software. Organizations should have a well-defined patch management process to ensure timely patching across all systems.
- Network Segmentation: Dividing the network into smaller segments, with restricted access between them, can limit the impact of a successful attack. This helps prevent attackers from spreading laterally across the network.
- Endpoint Security: Implementing robust endpoint security solutions, such as antivirus software, intrusion detection systems, and firewalls, can help detect and prevent malicious activity on individual devices.
- Vulnerability Scanning: Regular vulnerability scanning helps identify and assess potential weaknesses in systems and applications. This allows organizations to prioritize patching efforts and address vulnerabilities before they are exploited.
- Security Awareness Training: Educating employees about security best practices, such as recognizing phishing emails and avoiding suspicious links, is essential to prevent social engineering attacks.
- Threat Intelligence: Staying informed about emerging threats and attack trends helps organizations proactively identify potential vulnerabilities and implement appropriate countermeasures.
- Data Backup and Recovery: Maintaining regular backups of critical data is crucial to recover from a successful attack. This ensures that even if data is compromised, organizations can restore it from a clean backup.
- Incident Response Plan: Having a well-defined incident response plan helps organizations quickly and effectively respond to security incidents. This includes steps for containing the attack, investigating the incident, and restoring systems.
Recommendations for Ivanti Users
Ivanti users should prioritize security by adopting a comprehensive approach to vulnerability management and patch management.
- Regularly Update Ivanti Products: Ensure that all Ivanti products, including the Ivanti Patch for Windows, are updated to the latest versions. This includes applying security patches released by Ivanti to address known vulnerabilities.
- Utilize Ivanti’s Vulnerability Management Capabilities: Leverage Ivanti’s built-in vulnerability management features to identify and assess vulnerabilities across your environment. This helps prioritize patching efforts and address critical vulnerabilities.
- Implement Strong Access Control: Enforce strong password policies and utilize multi-factor authentication to secure access to Ivanti systems. This helps prevent unauthorized access and reduces the risk of account compromise.
- Monitor for Suspicious Activity: Regularly monitor Ivanti systems for any signs of suspicious activity, such as unusual login attempts or unexpected changes to configurations. This helps detect potential attacks early on.
Importance of Timely Patch Updates and Vulnerability Management
Promptly applying security patches and actively managing vulnerabilities is crucial for protecting systems from zero-day attacks.
- Reducing Attack Surface: Timely patching reduces the attack surface by addressing known vulnerabilities, making it more difficult for attackers to exploit weaknesses.
- Minimizing Impact: Patching vulnerabilities before they are exploited by attackers minimizes the potential impact of a successful attack.
- Maintaining System Security: Regularly updating systems and addressing vulnerabilities ensures that systems remain secure and protected against emerging threats.
- Improving Security Posture: A proactive approach to patch management and vulnerability management improves the overall security posture of an organization, reducing the risk of successful attacks.
Key Security Measures for Ivanti Users
| Security Measure | Benefits | Implementation Steps |
|—|—|—|
| Regular Patching | Reduces attack surface, minimizes impact, maintains system security | Establish a patch management process, automate patch deployment, prioritize critical patches, test patches before deployment, monitor patch status |
| Vulnerability Scanning | Identifies and assesses vulnerabilities, prioritizes patching efforts | Implement a vulnerability scanning tool, regularly scan systems, prioritize vulnerabilities based on severity and exploitability, address vulnerabilities promptly |
| Endpoint Security | Detects and prevents malicious activity on individual devices, protects sensitive data | Deploy endpoint security solutions, such as antivirus software, intrusion detection systems, and firewalls, configure security settings, monitor for suspicious activity |
| Network Segmentation | Limits the impact of a successful attack, prevents lateral movement | Divide the network into smaller segments, restrict access between segments, enforce network security policies |
| Security Awareness Training | Educates employees about security best practices, reduces risk of social engineering attacks | Develop security awareness training programs, provide regular training sessions, reinforce best practices, encourage reporting of suspicious activity |
| Threat Intelligence | Stays informed about emerging threats and attack trends, proactively identifies vulnerabilities | Subscribe to threat intelligence feeds, monitor security news and advisories, analyze threat data, implement appropriate countermeasures |
| Data Backup and Recovery | Enables recovery from a successful attack, protects critical data | Establish a data backup and recovery plan, regularly backup critical data, test backup and recovery processes, ensure data integrity |
| Incident Response Plan | Enables a coordinated and effective response to security incidents | Develop an incident response plan, define roles and responsibilities, establish communication channels, conduct regular drills |
The Newly Discovered Vulnerability
Ivanti has discovered a new vulnerability in its products that could potentially allow attackers to gain unauthorized access to systems. While Ivanti has already addressed two zero-day vulnerabilities, this newly identified vulnerability requires immediate attention.
The vulnerability, identified as CVE-2023-XXXX, resides in the core component of Ivanti’s patch management solution. It allows attackers to exploit a weakness in the software’s authentication process, potentially enabling them to bypass security measures and gain access to sensitive data or even take control of affected systems.
The Impact of the Vulnerability, Ivanti patches two zero days under attack but finds another
The potential impact of this vulnerability is significant. Attackers could exploit this weakness to gain unauthorized access to sensitive information, disrupt critical business operations, or even launch further attacks on the organization’s network.
Ivanti’s Response
Ivanti is actively working to address this vulnerability. They have released a security patch that addresses the identified weakness. The patch is available for download from Ivanti’s website and is recommended for immediate deployment.
The Importance of Continuous Security Monitoring and Vulnerability Scanning
This situation underscores the importance of continuous security monitoring and vulnerability scanning. Organizations should regularly assess their systems for vulnerabilities and implement necessary security controls to mitigate risks.
Recommendations for Organizations
Here are some key recommendations for organizations to prioritize in their security efforts:
- Install the latest security patches: Patching vulnerabilities promptly is crucial to prevent attackers from exploiting them. Organizations should prioritize installing the latest security patches for all their software, including Ivanti products.
- Implement strong authentication measures: Multi-factor authentication (MFA) can significantly enhance security by requiring users to provide multiple forms of identification before granting access to systems.
- Enable network segmentation: Segmenting the network can limit the impact of a successful attack by preventing attackers from spreading laterally to other parts of the network.
- Regularly conduct security audits: Regular security audits can help identify vulnerabilities and misconfigurations that could be exploited by attackers.
- Train employees on security best practices: Employees are often the first line of defense against cyberattacks. Organizations should train employees on security best practices, such as recognizing phishing attempts and reporting suspicious activity.
The discovery of these vulnerabilities and the ongoing efforts to patch them highlight the importance of proactive security measures. Organizations need to stay ahead of the curve by regularly patching their systems, implementing strong security controls, and monitoring for suspicious activity. While zero-day vulnerabilities are a constant threat, companies like Ivanti are working hard to protect their users. But it’s important to remember that cybersecurity is a shared responsibility. Users need to be aware of the risks and take steps to protect themselves. This means staying up-to-date on the latest security threats, implementing strong passwords, and being cautious about clicking on links or opening attachments from unknown sources.
It’s a constant game of whack-a-mole for security teams, as Ivanti proves with its latest zero-day patch. While they’re busy plugging one hole, another pops up. Meanwhile, Partech closes its second Africa fund at $300M to invest from seed to Series C , demonstrating the confidence investors have in the African tech scene. This funding boost could help create innovative solutions to address security vulnerabilities like those Ivanti is facing, proving that even in the face of constant threats, the tech world continues to evolve and adapt.
 Standi Techno News
Standi Techno News