Impact on Users
The unauthorized installation of cryptocurrency miners in uTorrent can have severe consequences for users, affecting their privacy, security, and financial well-being. It’s crucial to understand the potential harm caused by this type of malware and take steps to protect yourself.
Unauthorized cryptocurrency mining can significantly impact user experience and system performance. These miners, running in the background, consume substantial computing power and resources, leading to:
- Slowed down system performance: The intensive processing required for mining can significantly slow down your computer, making it sluggish and unresponsive. This can be particularly frustrating when performing everyday tasks like browsing the web or running applications.
- Increased energy consumption: Cryptocurrency mining is energy-intensive, leading to higher electricity bills. Your computer’s CPU and GPU will be working overtime, consuming more power than usual.
- Hardware damage: The constant strain on your computer’s hardware, particularly the CPU and GPU, can lead to overheating and potential damage. This can shorten the lifespan of your components and lead to costly repairs.
Impact on User Privacy and Security, Users say utorrent installed cryptocurrency miner without their knowledge
The unauthorized installation of cryptocurrency miners often involves the installation of malicious software that can compromise user privacy and security. These miners can:
- Steal sensitive information: Some miners might be designed to steal personal information, such as login credentials, credit card details, or other sensitive data. This information can then be used for identity theft or other malicious purposes.
- Track user activity: Cryptocurrency miners can track your online activity, collecting information about the websites you visit, the files you download, and other sensitive data. This information can be sold to third parties or used for targeted advertising.
- Create security vulnerabilities: The presence of malware on your system can create security vulnerabilities, making your computer susceptible to other threats, such as ransomware or viruses.
Financial Implications for Users
Unauthorized cryptocurrency mining can have significant financial implications for users. The miners can:
- Increase electricity bills: As mentioned earlier, cryptocurrency mining consumes a lot of energy, leading to increased electricity bills. This can be a significant financial burden, especially for users who are unaware of the mining activity taking place on their computers.
- Reduce computer lifespan: The constant strain on your computer’s hardware can shorten its lifespan, leading to premature failure and costly repairs or replacements.
- Lead to data loss: In some cases, malware associated with cryptocurrency miners can corrupt or delete user data, leading to significant financial losses if the data is irreplaceable.
Legal and Ethical Considerations: Users Say Utorrent Installed Cryptocurrency Miner Without Their Knowledge
The revelation that uTorrent was secretly installing cryptocurrency miners on user computers without their knowledge raises serious legal and ethical concerns. This practice not only violates user trust but also raises questions about potential legal liabilities for the company.
Legal Ramifications of Installing Cryptocurrency Miners Without User Consent
The legal ramifications of installing cryptocurrency miners without user consent are complex and depend on various factors, including the specific jurisdiction and the terms of service of the software.
Here are some potential legal issues:
* Privacy Violations: The act of installing a cryptocurrency miner without user consent can be considered a violation of privacy, as it allows access to the user’s computer resources and potentially personal data.
* Unauthorized Access: The installation of the miner without explicit permission from the user can be construed as unauthorized access to the user’s computer system.
* Misrepresentation: If uTorrent did not disclose the installation of the miner in its terms of service or during the installation process, it could be considered misrepresentation.
* Computer Fraud and Abuse Act (CFAA): In the United States, the CFAA could potentially be invoked in cases where unauthorized access to a computer system is used for malicious purposes, such as cryptocurrency mining.
Ethical Implications of Installing Cryptocurrency Miners Without User Consent
The ethical implications of this practice are equally significant.
* Breach of Trust: Installing a cryptocurrency miner without user consent represents a significant breach of trust between the software provider and its users.
* Exploitation of Resources: The use of user computer resources without their knowledge or consent for cryptocurrency mining is exploitative, as it consumes the user’s processing power and electricity without their permission.
* Lack of Transparency: The lack of transparency regarding the installation and operation of the miner is unethical, as it deprives users of the right to informed consent.
Potential Legal Actions Users Could Take Against uTorrent
Users who have been affected by this practice may have grounds to take legal action against uTorrent.
* Class Action Lawsuits: Users could potentially file class action lawsuits alleging violations of privacy, unauthorized access, misrepresentation, and other legal claims.
* Individual Lawsuits: Individual users could also pursue individual lawsuits seeking damages for the unauthorized use of their computer resources.
* Regulatory Investigations: Government agencies, such as the Federal Trade Commission (FTC) in the United States, could investigate the practice and potentially take enforcement action.
User Recommendations and Prevention
The recent discovery of cryptocurrency miners bundled with uTorrent highlights the importance of user vigilance and proactive security measures. It’s crucial to understand the risks associated with downloading and installing software from untrusted sources and to implement strategies that protect your computer from malicious activities.
Safeguarding Your Computer
It’s essential to implement robust security measures to protect your computer from unauthorized access and malicious software. These steps can significantly reduce the risk of encountering hidden cryptocurrency miners or other threats.
- Install a reputable antivirus software: A robust antivirus program can detect and remove malware, including cryptocurrency miners. Regularly update your antivirus software to ensure it’s equipped to handle the latest threats.
- Keep your operating system and software up-to-date: Software updates often include security patches that address vulnerabilities exploited by malware. Regularly updating your operating system and applications ensures you have the latest security protections.
- Use a firewall: A firewall acts as a barrier between your computer and the internet, blocking unauthorized access and potential threats. Enable your firewall and ensure it’s configured to provide maximum protection.
- Be cautious about downloading software from untrusted sources: Only download software from reputable websites and developers. Avoid downloading software from suspicious links or websites that may contain malware.
- Avoid clicking on suspicious links or attachments in emails: Phishing emails often contain malicious links or attachments that can install malware on your computer. Be wary of unsolicited emails, and avoid clicking on any links or opening attachments unless you are certain of their origin.
Monitoring Software Installations
Staying informed about the software installed on your computer is essential to identify any unauthorized or suspicious applications. Here are some steps you can take to monitor your software installations:
- Regularly check your installed programs: Periodically review the list of programs installed on your computer to identify any unknown or suspicious applications. If you find any unfamiliar programs, research them to determine their legitimacy.
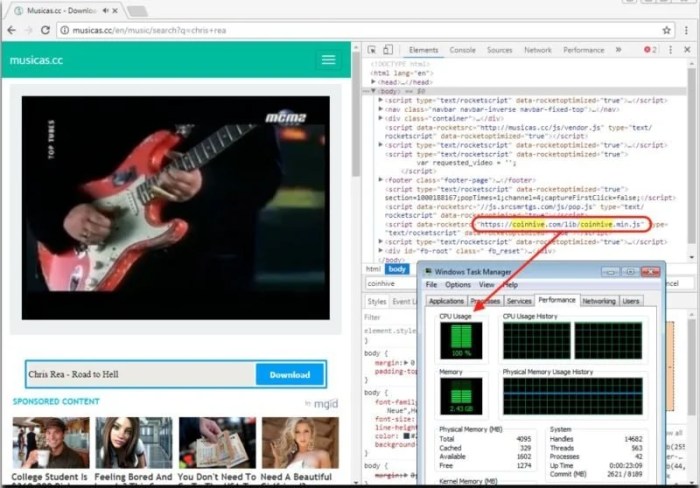
- Monitor your system resources: Cryptocurrency miners can consume significant system resources, including CPU and GPU power. Monitor your system performance for any unusual spikes in resource usage, which could indicate a hidden miner is running.
- Use a process monitor: Process monitors provide detailed information about the programs running on your computer, including their resource consumption. Use a process monitor to identify any suspicious processes that may be related to cryptocurrency mining.
Using Reputable Software Sources
Choosing reputable software sources is a crucial step in protecting your computer from malware. Here are some tips for identifying reliable sources:
- Download software from official websites: Always download software from the official website of the developer. This ensures you’re getting the legitimate version of the software, free from any malicious modifications.
- Check user reviews and ratings: Before downloading software, read user reviews and ratings to get an idea of its reputation and any potential issues. Negative reviews or reports of malware can be a red flag.
- Avoid freeware and cracked software: Freeware and cracked software often contain malware or other threats. Stick to paid software from reputable developers, or explore free and open-source alternatives.
Users say utorrent installed cryptocurrency miner without their knowledge – The uTorrent cryptocurrency mining controversy highlights the importance of being vigilant about the software we install on our devices. It serves as a stark reminder that even seemingly trusted applications can contain hidden agendas. While the allegations remain under investigation, the incident underscores the need for transparency and user consent in software development. As technology evolves, it’s crucial to stay informed about the potential risks and to take proactive steps to protect our digital lives.
It’s a wild world out there! While users are freaking out about uTorrent allegedly installing cryptocurrency miners without their knowledge, Verizon is rolling out HD Voice for prepaid customers. This means clearer calls, even if you’re on a budget, which is pretty cool considering the uTorrent drama. So, while you’re checking your downloads for sneaky miners, maybe give Verizon’s new feature a shot – you might be surprised by the difference in call quality.
verizon hd voice arrives for prepaid customers It’s like a breath of fresh air in the midst of all this tech chaos, right?
 Standi Techno News
Standi Techno News