iOS App Camera Permissions
Your iPhone is packed with features, and many apps rely on your camera to enhance your experience. From taking selfies to scanning documents, the camera is a powerful tool. But before an app can access your camera, it needs your permission. Understanding how camera permissions work is crucial for protecting your privacy and ensuring you’re in control of your data.
Types of Camera Permissions
iOS apps can request different levels of camera access.
- While Using the App: This is the most common permission level. It allows the app to access your camera only when you’re actively using the app. For example, a photo editing app would need this permission to let you take pictures within the app.
- Always: This permission grants the app continuous access to your camera, even when you’re not using the app. This level of access is usually reserved for apps that require constant monitoring or background recording. For example, a security camera app might need this permission to record footage even when you’re not actively using the app.
Granting and Revoking Camera Permissions
You have complete control over which apps can access your camera.
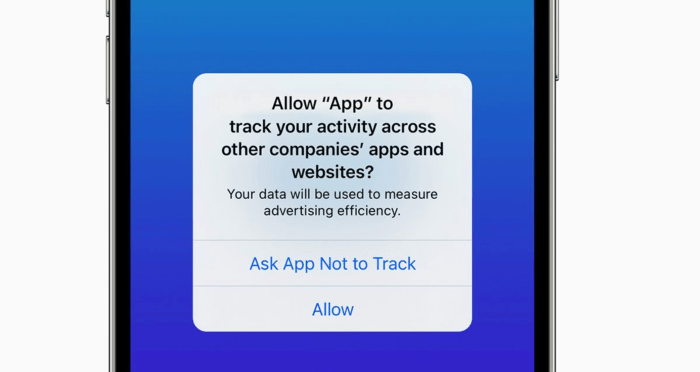
- Granting Permission: When an app requests camera access, you’ll see a prompt on your screen. You can choose to “Allow” or “Don’t Allow” the app’s request. If you choose “Allow,” the app will have access to your camera.
- Revoking Permission: You can revoke camera access for an app at any time. To do this, go to your iPhone’s Settings app, tap on “Privacy,” and then select “Camera.” Here, you’ll see a list of apps that have access to your camera. You can toggle the switch next to an app to revoke its access.
Implications of Granting Camera Permissions
While camera permissions can enhance your app experience, it’s important to be aware of the implications of granting access.
- Privacy Concerns: Apps with camera access can potentially record and store your videos and photos. If you’re not comfortable with an app having access to your camera, it’s best to deny the request or revoke permission later.
- Data Security: Some apps might share your camera data with third-party services or advertisers. Always read the app’s privacy policy to understand how your data will be used.
- Malware Risks: Malicious apps could use your camera for unauthorized recording or even spying. It’s essential to download apps only from trusted sources like the App Store.
Best Practices for Camera Permissions
Here are some tips to protect your privacy and use camera permissions responsibly:
- Be Mindful of App Requests: Before granting camera access, think about whether the app genuinely needs it. If the app’s functionality doesn’t require camera access, it’s best to deny the request.
- Read Privacy Policies: Take the time to read the app’s privacy policy to understand how your camera data will be used.
- Revoke Permissions When Not Needed: If an app no longer requires access to your camera, revoke the permission to protect your privacy.
- Use Trusted Sources: Download apps only from trusted sources like the App Store to minimize the risk of malware.
Secret Recording Capabilities
The possibility of apps secretly recording users without their knowledge or consent is a significant privacy concern. This practice can be used for malicious purposes, such as surveillance, data collection, and blackmail. While iOS has implemented measures to protect user privacy, there are still potential methods that apps might use to secretly record.
Methods of Secret Recording
Apps can employ various techniques to secretly record users without their knowledge. These methods can include:
- Background Audio Recording: Apps can use background audio recording capabilities to capture audio even when the app is not actively in use. This could be done through the use of the microphone, even if the user has not explicitly granted permission to access it.
- Screen Recording: Some apps might use screen recording capabilities to capture video of the user’s screen, including any sensitive information displayed. This could be done without the user’s knowledge or consent, potentially compromising their privacy.
- Third-Party Libraries: Apps might use third-party libraries that have hidden recording functionalities. These libraries could be used to secretly record audio or video without the user’s awareness.
- Exploiting System Vulnerabilities: In some cases, apps might exploit system vulnerabilities to gain access to the microphone or camera without explicit user permission.
Legal Implications of Secret Recording
Secretly recording individuals without their consent has significant legal implications. Depending on the jurisdiction, this practice can be considered a violation of privacy laws, such as:
- Wiretapping Laws: These laws prohibit the interception of private communications without a warrant. Secret recording of audio conversations could fall under this category.
- Data Protection Regulations: Laws like the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States require companies to obtain explicit consent before collecting and processing personal data. Secret recording could be considered a violation of these regulations.
Examples of Apps Caught Secretly Recording
Several apps have been caught secretly recording users in the past. These include:
- Facebook: In 2019, Facebook was accused of secretly recording users’ audio conversations through its Messenger app. The company later clarified that this was due to a bug and not intentional malicious behavior.
- TikTok: The popular video-sharing app TikTok was accused of secretly recording users’ screen activity, including their keystrokes. This was done to analyze user behavior and provide personalized recommendations.
- Google Assistant: Google Assistant was also accused of secretly recording users’ conversations even when the “Ok Google” command was not used. This was attributed to a bug in the system, which Google later addressed.
Challenges in Detecting Secret Recording
Detecting secret recording can be challenging due to the following reasons:
- Sophisticated Techniques: App developers can use increasingly sophisticated techniques to hide recording activities, making them difficult to detect.
- Limited User Access: Users have limited access to the underlying system functionalities and code, making it difficult to identify and analyze suspicious behavior.
- Dynamic Nature of Apps: Apps can constantly update and change their behavior, making it difficult to keep up with potential recording methods.
Privacy Concerns and User Education
The potential for apps to secretly record users raises serious privacy concerns. Imagine your private conversations, personal moments, or even sensitive data being captured without your knowledge. This breach of trust can have severe consequences, ranging from identity theft to blackmail.
Understanding the Risks
The ability of apps to access and record data from your device’s camera, microphone, and other sensors without your explicit consent poses a significant threat to your privacy.
- Unwanted Surveillance: Apps can secretly record your activities, capturing everything from your conversations to your movements, potentially without your awareness. This data can be used for malicious purposes, such as monitoring your behavior, tracking your location, or even blackmail.
- Data Breaches: If an app is compromised, your recorded data can be stolen by hackers, exposing your private information to unauthorized access. This can lead to identity theft, financial loss, or other serious consequences.
- Privacy Violations: Secret recording violates your fundamental right to privacy, allowing apps to intrude on your personal space and activities without your consent. This can have a chilling effect on your freedom of expression and your ability to engage in private activities without fear of being monitored.
Raising Awareness
Educating users about the risks of secret recording is crucial in protecting their privacy. Here’s a user education campaign to raise awareness:
- Public Service Announcements: Create engaging videos and social media campaigns highlighting the dangers of apps secretly recording users. Use real-life scenarios to illustrate the potential consequences of privacy breaches.
- Educational Resources: Develop online resources and guides explaining how apps can secretly record data, the potential risks involved, and steps users can take to protect themselves. These resources should be accessible and easy to understand.
- Community Outreach: Partner with community organizations, schools, and libraries to conduct workshops and presentations on privacy and security best practices. These events can help raise awareness and empower individuals to take control of their privacy.
Identifying and Avoiding Risky Apps
To avoid apps that secretly record your data, follow these steps:
- Read App Permissions: Carefully review the permissions requested by an app before downloading and installing it. Pay close attention to permissions related to camera, microphone, and other sensitive data access. If an app requests excessive or unnecessary permissions, it might be suspicious.
- Check App Reviews: Read user reviews and ratings for an app to see if others have reported any privacy concerns or issues with the app. Negative reviews mentioning data breaches, secret recording, or other privacy violations should raise red flags.
- Research App Developers: Look into the app developer’s reputation and track record. Reputable developers prioritize user privacy and security, while less trustworthy developers might be more likely to engage in unethical practices.
- Limit App Permissions: After installing an app, adjust its permissions to limit its access to your camera, microphone, and other sensitive data. Only grant permissions that are absolutely necessary for the app to function properly.
Privacy and Security Resources
To learn more about privacy and security, explore these resources:
- Electronic Frontier Foundation (EFF): EFF is a non-profit organization dedicated to defending civil liberties in the digital world. Their website offers valuable information on privacy, security, and digital rights.
- Privacy International: Privacy International is a global non-profit organization that works to protect the right to privacy. Their website provides resources on privacy issues, legislation, and best practices.
- National Cyber Security Alliance (NCSA): NCSA is a non-profit organization that works to promote cybersecurity awareness and best practices. Their website offers resources on protecting your online privacy and security.
App Store Policies and Enforcement
Apple’s App Store policies are designed to ensure the safety, security, and privacy of users. These policies extend to camera permissions and secret recording, with the goal of preventing malicious apps from exploiting user data. However, the effectiveness of these policies and their potential for improvement remain subject to ongoing scrutiny.
Apple’s Policies Regarding Camera Permissions and Secret Recording
Apple’s App Store policies explicitly state that apps must obtain user consent before accessing the camera. This consent must be clear, unambiguous, and informed. Additionally, apps cannot secretly record users without their knowledge or consent. Apps that violate these policies are subject to removal from the App Store.
Effectiveness of Enforcement
While Apple strives to enforce its policies, challenges remain in detecting and preventing apps from circumventing these regulations. Some apps may use deceptive tactics to gain user consent or may attempt to access the camera in the background without explicit permission. Apple’s review process, while rigorous, is not foolproof.
Potential Areas for Improvement
One potential area for improvement is the clarity and comprehensiveness of Apple’s policies. Some users may not fully understand the implications of granting camera permissions, leading to unintentional data leaks. Apple could consider enhancing its policies to provide more detailed guidance on best practices for camera access.
Comparison with Other App Stores
Other app stores, such as Google Play, also have policies regarding camera permissions and secret recording. However, the specifics of these policies and their enforcement mechanisms may vary. It’s important to note that each app store has its own unique approach to managing privacy concerns.
Technological Solutions and Mitigation: Ios Apps Camera Permission Secretly Record
The threat of secret recording through iOS apps demands proactive solutions. This section explores technological approaches to detect and prevent such activities, highlighting the role of security researchers and ethical hackers in identifying vulnerabilities. Additionally, we’ll provide guidance for users to protect their privacy while using apps.
Security Software and App Analysis
Security software plays a crucial role in detecting and preventing secret recording. These applications utilize various techniques to analyze app behavior and identify potential threats.
- Real-time Monitoring: Security software can monitor app activity in real-time, detecting suspicious behavior like camera access without user consent or unusual data transfer patterns.
- Static Analysis: This involves analyzing app code to identify potential vulnerabilities that could be exploited for secret recording. Static analysis tools can detect hidden code or suspicious API calls.
- Dynamic Analysis: This method involves running the app in a controlled environment to observe its behavior. Dynamic analysis tools can monitor network traffic, file access, and other activities to identify potential recording attempts.
Role of Security Researchers and Ethical Hackers
Security researchers and ethical hackers play a vital role in uncovering vulnerabilities that could be exploited for secret recording. Their efforts involve:
- Vulnerability Discovery: Security researchers meticulously analyze app code and infrastructure to identify weaknesses that could be exploited for unauthorized access to the camera or other sensitive data.
- Ethical Hacking: Ethical hackers simulate real-world attacks to test the security of apps and systems. This helps developers identify and fix vulnerabilities before they can be exploited by malicious actors.
- Public Disclosure: Security researchers and ethical hackers often disclose their findings to app developers and the public to raise awareness and encourage remediation. This helps protect users from potential threats.
User Privacy Protection, Ios apps camera permission secretly record
Users can take proactive steps to protect their privacy while using apps. These steps include:
- App Permissions: Carefully review app permissions before installing and using them. Be cautious about granting access to the camera unless it is absolutely necessary for the app’s functionality.
- Security Software: Install and use reputable security software on your iOS device. These applications can provide real-time protection against malicious apps and unauthorized access to sensitive data.
- App Reviews: Read reviews from other users to gain insights into an app’s security and privacy practices. Look for reviews that mention concerns about camera access or suspicious behavior.
- Regular Updates: Keep your iOS device and apps updated with the latest security patches. Updates often include fixes for vulnerabilities that could be exploited for secret recording.
Security Software Features
| Software Type | Features |
|—|—|
| Antivirus | Detects and removes malware, including apps that might secretly record. |
| Firewall | Blocks unauthorized access to your device, preventing apps from connecting to suspicious servers. |
| Privacy Scanner | Analyzes app permissions and identifies potential privacy risks. |
| App Permissions Manager | Allows you to control which apps have access to your camera, microphone, and other sensitive data. |
| VPN | Encrypts your internet traffic, making it harder for apps to track your online activity. |
Ios apps camera permission secretly record – While technology continues to evolve, it’s crucial to be vigilant about our privacy. Understanding how apps can access our devices and how to manage our permissions is essential. By being informed and taking proactive steps, we can navigate the digital landscape with greater confidence, ensuring our privacy remains intact.
While we’re all worried about iOS apps secretly recording us through our cameras, it’s worth remembering that the Acer Liquid M220, a Windows Phone 8.1 device coming to the US in June , is a solid option for those seeking a more secure mobile experience. Perhaps focusing on privacy concerns across all platforms, rather than just one, will lead to better protection for everyone.
 Standi Techno News
Standi Techno News