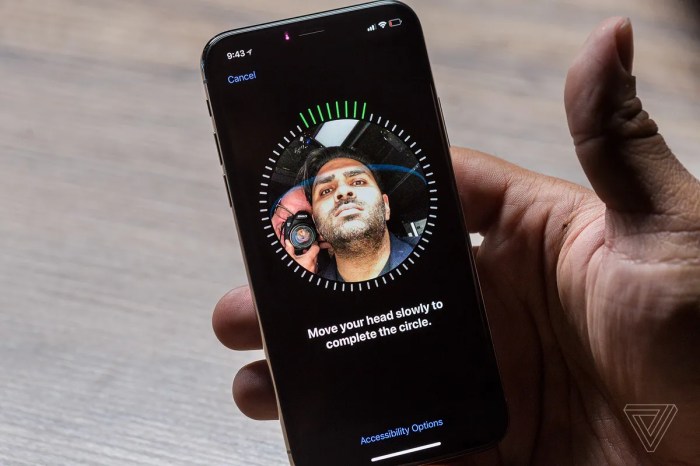
The iPhone X marked a significant shift in smartphone security with the introduction of Face ID, a facial recognition system that replaced the traditional fingerprint sensor. Face ID revolutionized how users unlock their devices, offering a more secure and convenient alternative.
How Face ID Works
Face ID leverages a combination of hardware and software components to achieve facial recognition.
* Hardware Components:
* TrueDepth Camera System: This system consists of a dot projector, an infrared camera, and a flood illuminator. The dot projector projects over 30,000 invisible infrared dots onto the user’s face, creating a depth map. The infrared camera captures this map, while the flood illuminator illuminates the face in low-light conditions.
* Secure Enclave: This dedicated processor within the iPhone’s A11 Bionic chip securely stores and processes the user’s facial data.
* Software Components:
* Machine Learning Algorithms: These algorithms analyze the captured depth map and create a mathematical representation of the user’s face.
* Neural Network: This network compares the captured facial data with the stored representation, enabling the device to recognize the user.
Capturing and Analyzing Facial Data
When setting up Face ID, the iPhone X captures multiple images of the user’s face from different angles. These images are then processed by the Secure Enclave to create a unique mathematical representation of the user’s facial features. This representation is stored securely and is not shared with any third parties.
During authentication, the TrueDepth camera system captures a depth map of the user’s face. This map is then compared to the stored representation using the neural network. If the two match, the device unlocks.
Comparison with Other Facial Recognition Technologies
Face ID stands out from other facial recognition technologies due to its:
* Depth Sensing: Face ID utilizes depth sensing, which creates a more accurate and secure representation of the user’s face compared to 2D facial recognition systems.
* Secure Enclave: The Secure Enclave ensures that the user’s facial data is stored securely and cannot be accessed by unauthorized parties.
* Anti-Spoofing Measures: Face ID incorporates anti-spoofing measures to prevent unauthorized access through masks, photos, or videos.
While Face ID offers significant advantages, it also has some limitations:
* Angle Dependency: Face ID requires the user to be facing the device directly for accurate recognition.
* Lighting Sensitivity: Strong sunlight or darkness can affect the performance of the TrueDepth camera system.
* Limited Facial Recognition: Face ID is designed to recognize a single user, making it less suitable for applications requiring multiple user recognition.
Data Sharing Practices
Apple has implemented Face ID, a biometric authentication system that uses facial recognition to unlock iPhones and authorize payments. While Face ID offers convenience and security, it also raises concerns about data privacy and how Apple handles the facial data it collects.
Apple’s stated goal is to ensure user privacy while providing a secure and convenient experience. However, understanding Apple’s data sharing practices is crucial for making informed decisions about using Face ID.
Types of Facial Data Collected
Apple collects facial data during Face ID setup and usage. This data includes:
* Face Scan: This is a 3D map of your face created during the initial Face ID setup process. It is used to identify you when you unlock your iPhone.
* Face ID Enrollment: This involves capturing multiple images of your face from different angles to create a unique representation.
* Face ID Usage Data: This includes information about when Face ID is used, such as the time and date of unlock attempts.
Apple’s Data Sharing Policies
Apple states that facial data is encrypted and stored securely on your device.
* On-Device Storage: Apple emphasizes that your facial data is never sent to Apple’s servers. It is stored locally on your device and not shared with any third-party applications.
* Encryption: Apple uses end-to-end encryption to protect your facial data. This means that only your device can access and decrypt the data.
* Anonymization: Apple also anonymizes facial data used for research and development. This means that your personal identity is not associated with the data used for these purposes.
Comparison with Other Companies
Apple’s data sharing practices differ significantly from companies like Google and Facebook.
* Data Collection: Google and Facebook collect vast amounts of user data, including facial data, from various sources, such as their apps and websites. This data is often used for targeted advertising and other purposes.
* Data Sharing: Google and Facebook share user data with third-party companies, including advertisers. This data sharing is often done without explicit user consent.
Apple’s stated policy is to keep your facial data private and secure, while Google and Facebook’s practices raise concerns about data privacy and transparency.
Developer Access to Face Data
Apple, in its commitment to user privacy, carefully regulates how developers can access and use facial data collected by Face ID. While Face ID offers a secure and convenient way for users to unlock their iPhones and authenticate transactions, it’s crucial to understand the limitations and safeguards in place to protect user privacy.
Developers may require access to facial data for specific purposes, such as:
- Authentication: Developers can use Face ID to verify a user’s identity for accessing apps or services, enhancing security and reducing the need for passwords. For example, a banking app might use Face ID to authorize transactions.
- Personalization: Facial data can be used to personalize user experiences. For instance, an app could use Face ID to identify the user and tailor content recommendations or settings based on their preferences.
Privacy and Security Concerns
The sharing of facial data with developers raises significant privacy and security concerns. While Face ID technology offers a secure and convenient authentication method, the potential for misuse of this sensitive information necessitates careful consideration of the ethical, legal, and regulatory implications.
Potential Privacy Risks
Sharing facial data with developers introduces a range of potential privacy risks. Facial recognition technology, while powerful, can be used to identify individuals without their knowledge or consent. This raises concerns about the potential for unauthorized surveillance, identity theft, and discrimination. For example, a developer could use facial data to track individuals’ movements, create profiles based on their facial expressions, or even target them with personalized advertising based on their perceived emotions.
Ethical Implications of Using Facial Data
The use of facial data for purposes beyond authentication, such as targeted advertising or surveillance, raises significant ethical questions. For instance, using facial recognition to analyze people’s emotions in public spaces could lead to the creation of social profiles that could be used to discriminate against individuals or groups. Similarly, the use of facial data for targeted advertising could exacerbate existing inequalities and lead to the creation of echo chambers that reinforce biases and prejudices.
Legal and Regulatory Frameworks
The collection and use of facial data are subject to a complex web of legal and regulatory frameworks. These frameworks vary significantly across jurisdictions and are constantly evolving. For example, the European Union’s General Data Protection Regulation (GDPR) imposes strict requirements on the collection and use of personal data, including facial data. The GDPR requires organizations to obtain explicit consent from individuals before collecting their facial data and to ensure that the data is used only for the purpose for which it was collected. Similarly, the California Consumer Privacy Act (CCPA) provides consumers with the right to access, delete, and opt out of the sale of their personal data, including facial data.
User Consent and Control
Apple’s Face ID technology, while lauded for its convenience and security, raises significant concerns about user privacy and control over their facial data. The question of how users can control the sharing of their facial data with developers and the transparency of Apple’s data sharing practices are crucial aspects of this discussion.
User Control Over Facial Data Sharing
Users have a degree of control over how their facial data is shared with developers through iPhone settings. Here’s how:
- Face ID & Passcode Settings: Users can access the “Face ID & Passcode” settings on their iPhones to manage the apps that have access to their facial data. This allows users to selectively grant or deny access to specific apps.
- App Permissions: When an app requests access to Face ID data, users receive a prompt asking for their permission. Users can choose to grant or deny access on a case-by-case basis.
These mechanisms provide users with a degree of control over their facial data. However, the effectiveness of these controls is subject to debate.
Transparency of Apple’s Data Sharing Practices
Apple emphasizes its commitment to user privacy and data security. The company states that it does not collect or store users’ facial data. However, the company’s data sharing practices with developers raise concerns about transparency.
- Limited Information Provided: Apple’s documentation and privacy policies provide limited information about how facial data is shared with developers. The exact nature of the data shared and how it is used by developers remains unclear.
- Lack of Granular Control: Users lack granular control over the specific types of facial data shared with developers. While they can choose to grant or deny access, they cannot select which specific data points are shared.
This lack of transparency raises concerns about the potential misuse of facial data by developers.
Effectiveness of User Consent Mechanisms
User consent mechanisms are a crucial aspect of data privacy. However, the effectiveness of these mechanisms in protecting privacy and security is debatable.
- Limited Understanding: Users may not fully understand the implications of granting access to their facial data. The complex nature of data sharing practices and the lack of clear information can make it difficult for users to make informed decisions.
- Potential for Deception: Developers may use misleading language or obscure the true purpose of data collection in their app permission requests. This can lead users to grant access unknowingly, compromising their privacy.
Despite these concerns, user consent mechanisms are a critical step in protecting user privacy. However, further efforts are needed to improve transparency, provide users with more granular control, and ensure that consent is truly informed and meaningful.
Industry Best Practices
In the realm of data privacy and security, handling sensitive user data, especially facial data, requires adherence to stringent best practices. These practices aim to minimize privacy risks, ensure responsible data usage, and maintain user trust.
Apple’s Data Privacy and Security Approach Compared to Industry Standards
Apple’s approach to data privacy and security is often lauded for its emphasis on user control and data minimization. The company’s commitment to privacy is reflected in its policies, technologies, and practices.
- Data Minimization: Apple’s design philosophy emphasizes collecting only the necessary data for the intended purpose. This principle is applied to facial data, where only a mathematical representation of the face is stored, not the actual image.
- On-Device Processing: Facial recognition processing for Face ID occurs on the device itself, not on remote servers. This reduces the risk of data breaches and unauthorized access.
- User Consent and Control: Apple requires explicit user consent for the use of facial data. Users have the ability to delete their Face ID data at any time.
- Transparency: Apple provides clear and concise information about its data collection practices, including how facial data is used and secured.
While Apple’s approach aligns with many industry best practices, it’s important to note that regulations and standards are evolving.
The Role of Technology and Policies in Mitigating Privacy Risks
Technological advancements and robust policies are crucial in mitigating privacy risks associated with facial data sharing.
- Differential Privacy: This technique adds noise to data to protect individual privacy while preserving the overall data pattern. This can be applied to facial data to anonymize it while still allowing for analysis and insights.
- Data Encryption: Encrypting facial data ensures that only authorized parties can access it. This prevents unauthorized access and protects data from breaches.
- Access Control: Implementing strict access control mechanisms limits who can access facial data and for what purposes. This ensures responsible data usage and minimizes potential misuse.
- Data Retention Policies: Defining clear data retention policies ensures that facial data is only stored for as long as necessary and then deleted. This reduces the risk of data breaches and unauthorized access over time.
Iphone x face data shared with developers – The sharing of iPhone X face data with developers raises critical questions about privacy and security. While Apple promises to safeguard user information, the potential for misuse and the lack of complete transparency leave many users uneasy. As technology continues to evolve, it’s crucial to have open discussions about data privacy and ensure that users have control over their own information. Ultimately, it’s up to each individual to decide how much data they’re comfortable sharing and to hold tech companies accountable for protecting our privacy.
It’s a wild world out there when it comes to privacy, especially with the iPhone X’s facial recognition data being shared with developers. But hey, at least your Xiaomi Mi 4i can handle some serious graphics, check out its GFXBench scores here. Maybe that’s a better trade-off than sharing your face with the world, right?
 Standi Techno News
Standi Techno News