App permissions user control sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset.
In today’s digital landscape, where apps are constantly vying for access to our personal information, understanding app permissions and how to control them is crucial for safeguarding our privacy and security. This guide delves into the evolution of app permissions, explores the different types of permissions requested, and provides insights into the user control mechanisms available to us. We’ll also examine the potential risks associated with granting excessive permissions, discuss best practices for app developers, and explore future trends in permission management.
The Evolution of App Permissions: App Permissions User Control
In the early days of mobile operating systems, app permissions were a relatively simple concept. Developers had broad access to user data and device functionality, with limited options for users to control these privileges. However, as mobile devices became more powerful and connected, the need for greater user control over app permissions grew significantly. This evolution has led to a complex landscape of permission models, with different platforms adopting unique approaches to balancing security, privacy, and user experience.
The Early Days: Limited User Control
The first mobile operating systems, such as Symbian and Palm OS, lacked sophisticated permission models. Apps could often access sensitive data and device features without explicit user consent. This approach was driven by the limited processing power and storage capacity of early mobile devices, which made granular permission management impractical. For example, an early mobile game might have been able to access your contact list without your knowledge, simply because the developers needed to store high scores locally on your device.
The Rise of User Control: iOS and Android
The introduction of the iPhone in 2007 marked a turning point in the evolution of app permissions. Apple’s iOS operating system introduced a more granular permission model, requiring users to explicitly grant access to specific device features, such as location services, camera, and microphone. This approach was adopted by other platforms, including Android, which introduced a similar permission system with its first release in 2008.
Different Approaches to Permission Management
The iOS and Android platforms have adopted different approaches to permission management, each with its own advantages and drawbacks. iOS typically presents permissions to the user on a per-app basis, while Android allows users to manage permissions at a system-wide level.
- iOS: iOS presents permissions in a more straightforward manner, typically asking the user to grant access to a specific feature when an app first requests it. This approach simplifies the user experience, but it can also lead to users granting permissions without fully understanding the implications.
- Android: Android offers more granular control over permissions, allowing users to selectively grant or deny access to specific features for individual apps. This approach provides greater flexibility, but it can also be more complex for users to navigate.
Key Milestones in App Permissions
Over the years, app permissions have evolved significantly, driven by user privacy concerns and technological advancements.
- Introduction of granular permissions: The shift from broad permissions to granular control over specific device features marked a significant step towards greater user privacy.
- Emphasis on user education: Platforms have begun to prioritize user education about app permissions, providing clear explanations and examples to help users make informed decisions.
- Emergence of permission management tools: Third-party apps and built-in operating system features have emerged to help users manage app permissions more effectively.
- Privacy-focused operating systems: Platforms like LineageOS and GrapheneOS have emerged, emphasizing user privacy and providing greater control over app permissions.
Types of App Permissions
In the modern digital landscape, apps have become an integral part of our lives, offering convenience and functionality. However, to provide these services, apps often require access to specific data and functionalities on our devices. This access is granted through permissions, which empower users to control what information and resources apps can utilize. This section delves into the various types of app permissions, explaining their purpose, potential uses, and associated risks.
Location Permissions
Location permissions enable apps to access your device’s location data, such as GPS coordinates, Wi-Fi network information, and cell tower data. This information allows apps to provide location-based services, such as:
- Navigation apps like Google Maps and Waze use location data to guide you to your destination.
- Weather apps utilize location data to provide accurate weather forecasts for your current location.
- Social media apps like Facebook and Instagram can use location data to recommend nearby friends or events.
Granting location permissions can pose potential risks:
- Privacy concerns: Apps can track your movements and potentially share this information with third parties, raising concerns about privacy violations.
- Security risks: Malicious apps can use location data to track your movements and potentially target you with scams or other attacks.
Camera Permissions
Camera permissions allow apps to access your device’s camera. This enables apps to capture photos and videos, perform facial recognition, and use augmented reality features. Here are some examples of how apps utilize camera permissions:
- Photo and video apps: Apps like Instagram and Snapchat use camera permissions to capture and share photos and videos.
- Scanning apps: Barcode scanners and QR code readers require camera permissions to scan codes.
- Augmented reality (AR) apps: AR apps overlay digital content onto the real world, often using the camera to capture the environment.
Granting camera permissions can present certain risks:
- Privacy concerns: Apps can secretly record videos or capture photos without your knowledge, potentially violating your privacy.
- Security risks: Malicious apps can use the camera to access your surroundings and potentially steal sensitive information.
Microphone Permissions
Microphone permissions allow apps to access your device’s microphone. This enables apps to record audio, perform voice recognition, and conduct audio calls. Here are some examples of how apps utilize microphone permissions:
- Voice assistants: Apps like Siri, Google Assistant, and Alexa use microphone permissions to listen to your voice commands.
- Voice recording apps: Apps like Voice Memos and Tape-a-Talk use microphone permissions to record audio notes.
- Video calling apps: Apps like Zoom and Skype use microphone permissions to transmit your voice during calls.
Granting microphone permissions can present certain risks:
- Privacy concerns: Apps can secretly record your conversations without your knowledge, potentially violating your privacy.
- Security risks: Malicious apps can use the microphone to listen to your conversations and potentially steal sensitive information.
Contacts Permissions
Contacts permissions allow apps to access your device’s contact list. This enables apps to share contacts with other users, sync contacts with online services, and perform contact management tasks. Here are some examples of how apps utilize contacts permissions:
- Messaging apps: Apps like WhatsApp and Messenger use contacts permissions to import your contacts and facilitate communication.
- Social media apps: Apps like Facebook and Instagram use contacts permissions to recommend friends and connect with existing contacts.
- Contact management apps: Apps like Google Contacts and Apple Contacts use contacts permissions to manage your contact list.
Granting contacts permissions can present certain risks:
- Privacy concerns: Apps can access your contact list and potentially share this information with third parties, raising concerns about privacy violations.
- Security risks: Malicious apps can use your contact list to spread spam or phishing attacks to your contacts.
Storage Permissions
Storage permissions allow apps to access your device’s internal storage. This enables apps to save files, access documents, and manage data on your device. Here are some examples of how apps utilize storage permissions:
- File management apps: Apps like File Explorer and Documents by Readdle use storage permissions to access and manage files on your device.
- Photo and video apps: Apps like Instagram and Snapchat use storage permissions to save photos and videos to your device.
- Document editing apps: Apps like Microsoft Word and Google Docs use storage permissions to access and save documents on your device.
Granting storage permissions can present certain risks:
- Privacy concerns: Apps can access your personal files and potentially share this information with third parties, raising concerns about privacy violations.
- Security risks: Malicious apps can use storage permissions to steal your personal data or install malware on your device.
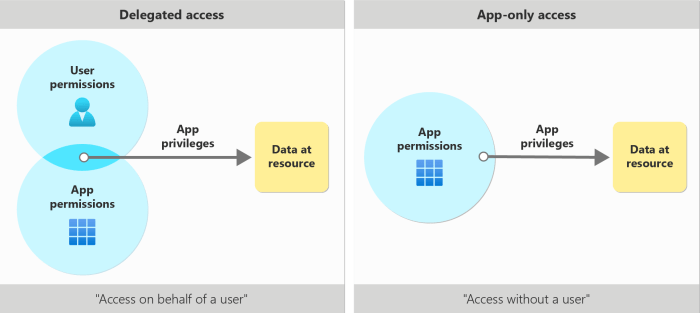
User Control Mechanisms
The evolution of app permissions has led to a focus on user control. Users are no longer passive recipients of permissions; they have tools to manage and customize how apps access their data and resources. These control mechanisms provide users with greater transparency and power over their digital privacy.
Permission Requests During App Installation
Permission requests during app installation are the first line of defense for users. This initial stage provides users with a clear understanding of the data and functionalities an app requires before granting access.
- Explicit Permissions: Users are presented with a list of permissions the app requires and are given the option to accept or deny each request. This approach empowers users to make informed decisions about what data they are willing to share. For example, a photo editing app might request access to the camera, storage, and microphone. The user can choose to grant only camera access if they only intend to use the app for editing photos from their gallery.
- Conditional Permissions: Some apps request permissions only when they are needed. For example, a weather app might request location access only when the user wants to see the weather forecast for their current location. This approach reduces the potential for apps to collect unnecessary data and improves user privacy.
- Bundled Permissions: In some cases, apps may bundle multiple permissions together. This can be problematic because it can force users to grant access to data they don’t want to share in order to use a desired feature. For example, an app might bundle access to the camera, microphone, and contacts, even if the user only wants to use the app for its camera functionality. This practice can be considered less user-friendly as it reduces user control.
In-App Permission Settings
In addition to installation-time requests, many apps allow users to manage permissions within the app itself. This provides users with a more granular level of control over how apps access their data.
- App-Specific Settings: Apps can provide settings that allow users to control specific aspects of data access. For example, a social media app might allow users to choose whether to share their location, contacts, or photos. This level of control allows users to customize their privacy preferences for each app.
- Permission Revocation: Users can often revoke permissions they have previously granted to apps. This is especially important for apps that might have access to sensitive data, such as location or contacts. For example, if a user no longer wants a fitness app to access their location data, they can revoke that permission.
- Notifications and Alerts: Apps can notify users when they are accessing sensitive data. This helps users stay aware of how apps are using their data and allows them to take action if they feel uncomfortable with the access.
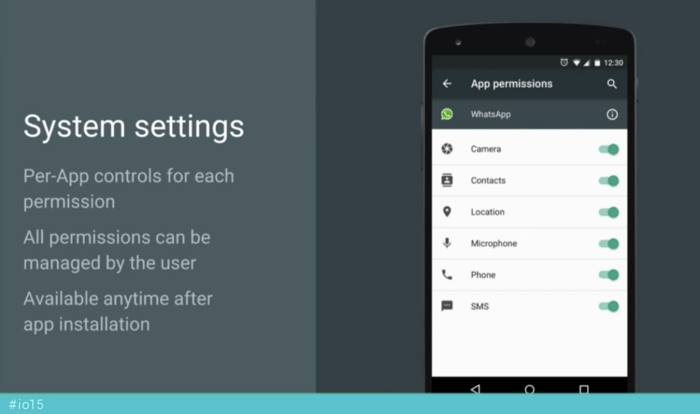
System-Level Permission Management
Operating systems provide system-level settings for managing app permissions. These settings offer a centralized location for users to control the permissions granted to all apps on their device.
- Centralized Control: System-level settings provide a single point of access for managing app permissions. Users can view and modify permissions for all installed apps in one place, making it easier to maintain control over their privacy.
- Default Permission Settings: Operating systems often offer default permission settings that can be applied to all apps. This can help users quickly establish a baseline level of privacy control for their device.
- Advanced Settings: System-level settings often include advanced options for managing app permissions, such as the ability to block specific types of access or set limits on data usage. This level of control can be beneficial for users who are concerned about their privacy and want to take extra precautions.
Privacy and Security Implications
In the modern digital landscape, apps have become an integral part of our lives, offering convenience and access to a vast array of services. However, with this convenience comes a potential trade-off – our privacy and security. The permissions granted to apps play a crucial role in determining the extent to which our personal information is accessible and potentially vulnerable.
Excessive app permissions can significantly impact our privacy and security, raising concerns about the potential misuse of our data.
Data Collection and Sharing
The permissions granted to apps directly influence the amount and type of data they can collect and share. Apps often request access to sensitive information such as location, contacts, camera, microphone, and even our browsing history.
- For example, a social media app might request access to your contacts to suggest friends to follow. While this may seem harmless, it allows the app to collect and potentially share your contact list with third-party advertisers or data brokers.
- Similarly, a fitness app might request access to your location data to track your runs or walks. However, this access could also be used to track your movements and potentially share your location with other users or third parties.
The potential for data misuse is significant, as collected data can be used for targeted advertising, profiling, identity theft, and even blackmail.
Informed Consent and User Awareness
To mitigate these risks, it is crucial to ensure informed consent and user awareness regarding app permissions. Users should be fully aware of the implications of granting specific permissions and the potential consequences for their privacy and security.
- App developers should provide clear and concise explanations of why specific permissions are required and how the data will be used.
- Users should be encouraged to carefully review the permissions requested by apps before granting them access.
- Educating users about the potential risks associated with excessive app permissions is essential for promoting responsible app usage and protecting user privacy.
Best Practices for App Developers
App developers play a crucial role in ensuring user privacy and security. By adhering to best practices for permission usage, they can build trust and enhance user experience.
Developers should strive to minimize permission requests and provide clear explanations to users. This fosters transparency and empowers users to make informed decisions about the data they share.
It’s a classic tale: we grant apps access to our data, often without fully understanding the implications. This can lead to privacy concerns, especially when we consider the recent news that World of Warcraft has lost nearly 3 million subscribers. While not directly related to app permissions, it highlights the need for users to be more cautious about what information they share and how they manage their digital footprint.
Permission Categories and Best Practices
To ensure responsible permission usage, developers should consider the following best practices categorized by permission type:
| Permission Category | Best Practices |
|---|---|
| Location |
|
| Camera |
|
| Microphone |
|
| Contacts |
|
| Storage |
|
| Network |
|
User Empowerment and Awareness
The digital landscape is riddled with apps, each vying for your attention and data. But the power to control your digital privacy lies within your hands. By understanding app permissions and wielding them wisely, you can protect your information and navigate the online world with greater confidence.
Strategies for Enhanced Control Over App Permissions
Users can actively safeguard their privacy by implementing these strategies.
- Scrutinize Permissions: Before installing an app, carefully review the permissions it requests. Ask yourself, “Do I really need this app to access my contacts, location, or microphone?” If an app requests access to information that seems unnecessary, consider not installing it or finding an alternative.
- Grant Permissions Selectively: Don’t blindly grant all permissions an app requests. Instead, grant only the permissions that are absolutely necessary for the app to function.
- Regularly Audit Permissions: Periodically check the permissions granted to your apps. Over time, apps may have been updated, granting them access to more data than initially intended. Review and revoke unnecessary permissions.
- Use Permission Management Tools: Many devices and operating systems offer built-in permission management tools. These tools allow you to easily review and modify the permissions granted to apps. Utilize these features to ensure you have control over your data.
- Choose Apps Wisely: Opt for apps from reputable developers and those with positive user reviews. Research the app’s privacy policy and terms of service to understand how your data will be used.
User Education and Awareness in Privacy Protection
Knowledge is power. By educating users about app permissions and privacy, we can empower them to make informed decisions.
- Awareness Campaigns: Public awareness campaigns can effectively highlight the importance of understanding app permissions and the potential risks associated with granting unnecessary access. These campaigns can utilize various channels, such as social media, public service announcements, and educational materials.
- Interactive Resources: Providing interactive resources, such as quizzes and tutorials, can make learning about app permissions engaging and accessible. These resources can be tailored to different age groups and technical proficiency levels.
- Simplified Language: Explaining app permissions in clear and concise language, avoiding technical jargon, can make it easier for users to grasp the concepts and make informed decisions.
- Privacy Checklists: Providing checklists that guide users through the process of reviewing app permissions and making informed choices can be a valuable tool. These checklists can be tailored to different types of apps, such as social media, banking, and shopping apps.
Empowering Tools for Effective Permission Management
Various tools and resources can empower users to manage app permissions effectively.
- App Permission Managers: Third-party apps, specifically designed to manage app permissions, can provide a centralized platform for reviewing and adjusting permissions for all your apps. These apps can offer features like automatic permission audits, granular control over permissions, and the ability to block apps from accessing specific data.
- Privacy-Focused Browsers: Browsers that prioritize user privacy, such as Brave, DuckDuckGo, and Tor, can enhance your online security by limiting tracking and data collection. These browsers often have built-in permission management features that give you greater control over your data.
- Privacy-Focused Search Engines: Search engines that focus on privacy, such as DuckDuckGo and Startpage, do not track your searches or store your personal information. These engines can help you maintain your online privacy while searching for information.
Future Trends and Considerations
The realm of app permissions is constantly evolving, driven by technological advancements and a growing awareness of user privacy. This evolution is paving the way for more granular control over data access, context-aware permission management, and user-centric approaches to app functionality.
Permission Granularity, App permissions user control
The concept of fine-grained permission control allows users to precisely dictate which specific data an app can access. Instead of granting blanket access to entire categories of data, such as contacts or location, users can selectively authorize access to specific elements.
For example, a fitness app might only require access to your location when you are actively using the app for tracking your runs. It wouldn’t need constant access to your location when you are not using the app. This level of granularity empowers users to maintain greater control over their privacy while still enabling apps to function effectively.
As technology continues to evolve, so too will the ways in which apps request and utilize our personal information. Staying informed about app permissions, exercising caution when granting access, and utilizing the tools available to manage permissions are essential for protecting our digital privacy. By understanding the intricacies of app permissions, we can navigate the digital world with greater awareness and control, ensuring our data remains secure and our online experiences remain positive.
 Standi Techno News
Standi Techno News