Apple launch bug bounty program – Apple, the tech giant known for its sleek devices and tight-lipped security, has finally taken the plunge into the world of bug bounty programs. This move signifies a shift in Apple’s approach to security, embracing the power of the community to uncover vulnerabilities and strengthen its defenses.
The program, launched in 2022, offers rewards to security researchers who identify and report critical flaws in Apple’s software and hardware. It’s a game-changer for the tech industry, opening the door for collaboration between Apple and the global security community.
Apple’s Bug Bounty Program: Apple Launch Bug Bounty Program
Apple’s Bug Bounty Program is a way for security researchers to help Apple improve the security of its products and services by finding and reporting vulnerabilities. The program incentivizes researchers to discover and report security flaws in Apple’s software, hardware, and services.
Program Scope and Purpose
The program’s purpose is to encourage security researchers to find and report vulnerabilities in Apple’s products and services. By rewarding researchers for their efforts, Apple aims to improve the overall security of its ecosystem. The program covers a wide range of Apple products and services, including iOS, macOS, watchOS, tvOS, iCloud, Safari, and more.
Vulnerabilities Eligible for Rewards, Apple launch bug bounty program
Apple’s Bug Bounty Program offers rewards for various types of vulnerabilities, including:
- Code Execution: Exploiting a vulnerability to gain control of a device or system.
- Data Disclosure: Accessing sensitive data without authorization.
- Denial of Service: Preventing a device or service from functioning correctly.
- Spoofing: Impersonating a legitimate user or system.
- Privilege Escalation: Gaining unauthorized access to higher privileges on a system.
- Logic Flaws: Exploiting flaws in the logic of a system or application.
- Authentication Bypass: Circumventing authentication mechanisms to gain unauthorized access.
Eligibility Criteria and Reporting Process
To participate in Apple’s Bug Bounty Program, researchers must meet the following eligibility criteria:
- Be at least 18 years old.
- Agree to the program’s terms and conditions.
- Follow Apple’s responsible disclosure guidelines.
To report a vulnerability, researchers must submit a detailed report through Apple’s Bug Bounty Program website. The report should include information such as the affected product or service, the vulnerability’s severity, a detailed description of the vulnerability, and proof of concept. Apple reviews all reports and rewards researchers for eligible vulnerabilities based on their severity and impact.
Program Structure and Incentives
Apple’s Bug Bounty program is structured to reward security researchers for identifying and reporting vulnerabilities in Apple’s products and services. The program offers a tiered reward system, with higher rewards for more critical vulnerabilities.
The program aims to encourage responsible disclosure and enhance the security of Apple’s ecosystem. By incentivizing researchers to report vulnerabilities, Apple can proactively address security risks and protect its users from potential threats.
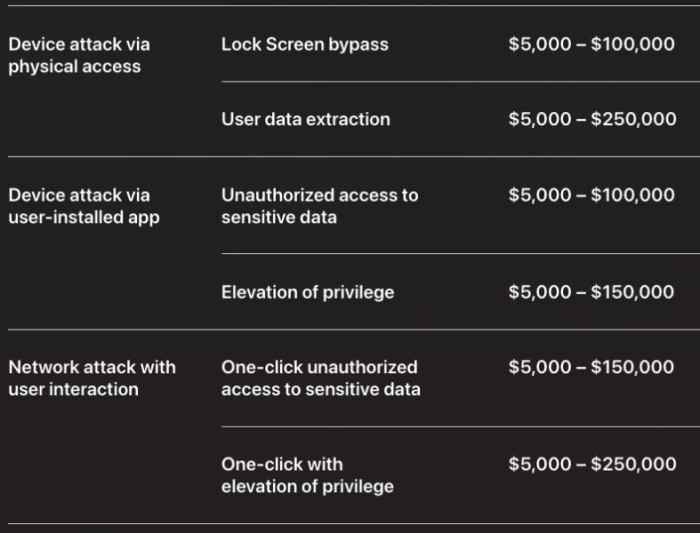
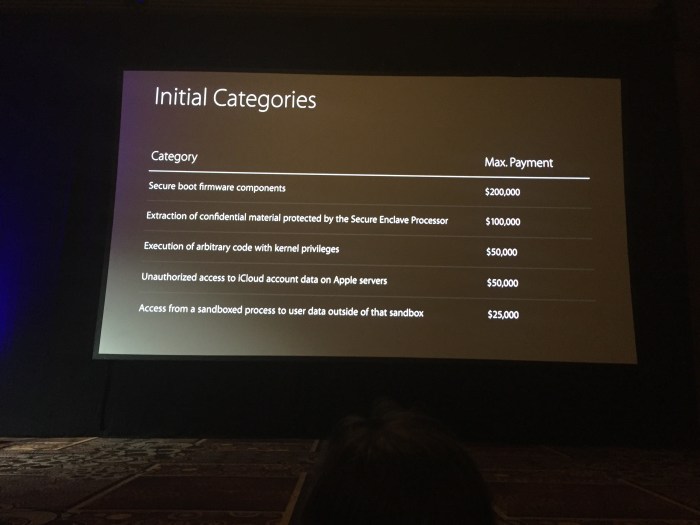
Reward Tiers
Apple’s Bug Bounty program offers various reward tiers based on the severity and impact of the vulnerability reported.
Here’s a breakdown of the reward tiers:
- Low: This tier typically includes vulnerabilities that pose minimal risk to Apple’s products and services. The reward for this tier is usually a small amount, often in the form of a gift card or merchandise.
- Medium: This tier covers vulnerabilities that pose a moderate risk to Apple’s products and services. The reward for this tier is typically higher than the low tier, often in the form of a cash reward.
- High: This tier encompasses vulnerabilities that pose a significant risk to Apple’s products and services. The reward for this tier is significantly higher than the medium tier, often in the form of a substantial cash reward.
- Critical: This tier covers vulnerabilities that pose a critical risk to Apple’s products and services. The reward for this tier is the highest, often in the form of a substantial cash reward and potentially additional benefits, such as recognition and a dedicated security researcher program.
Comparison with Other Tech Giants
Apple’s Bug Bounty program is comparable to other tech giants’ programs, with varying reward structures and incentives. For instance, Google’s Vulnerability Rewards Program offers rewards based on the severity of the vulnerability, with a maximum reward of up to $31,337. Microsoft’s Bug Bounty program also offers a tiered reward system, with rewards ranging from $500 to $20,000.
Effectiveness of Incentives
Apple’s Bug Bounty program has been effective in attracting and motivating security researchers. The program’s tiered reward system, with its emphasis on critical vulnerabilities, encourages researchers to focus on high-impact issues. Apple’s reputation for responsible disclosure and its commitment to security have also contributed to the program’s success.
Apple’s Bug Bounty program has been instrumental in identifying and mitigating security vulnerabilities in its products and services. The program has helped to enhance the security of Apple’s ecosystem and protect its users from potential threats.
Impact on Apple’s Security Posture
Apple’s Bug Bounty Program has played a pivotal role in strengthening the company’s security posture. By incentivizing ethical hackers to identify and report vulnerabilities, Apple has been able to proactively address security flaws before they can be exploited by malicious actors.
Vulnerabilities Discovered and Patched
The program has been instrumental in discovering and patching a wide range of vulnerabilities across Apple’s products and services. These vulnerabilities have included:
- Zero-day exploits: These are vulnerabilities that are unknown to the software developer and can be exploited immediately upon discovery. The program has helped Apple identify and patch zero-day exploits in its operating systems, web browsers, and other software. For instance, in 2022, a researcher working with Apple’s Bug Bounty Program discovered a zero-day vulnerability in iOS that could have allowed attackers to take control of a user’s device. Apple quickly patched the vulnerability, preventing potential attacks.
- Cross-site scripting (XSS) vulnerabilities: These vulnerabilities allow attackers to inject malicious scripts into websites, potentially stealing user data or hijacking accounts. Apple’s Bug Bounty Program has helped the company identify and patch XSS vulnerabilities in its websites and web applications. For example, in 2021, a researcher working with the program discovered an XSS vulnerability in Apple’s iCloud website. Apple promptly patched the vulnerability, preventing attackers from exploiting it to steal user data.
- Denial-of-service vulnerabilities: These vulnerabilities allow attackers to disrupt the normal operation of a service or device. Apple’s Bug Bounty Program has helped the company identify and patch denial-of-service vulnerabilities in its products and services. In 2020, a researcher working with the program discovered a denial-of-service vulnerability in Apple’s FaceTime service. Apple patched the vulnerability, preventing attackers from causing widespread disruptions to the service.
Future Directions and Considerations
Apple’s bug bounty program is a dynamic initiative that is constantly evolving to adapt to the ever-changing landscape of cybersecurity threats. As technology advances and new vulnerabilities emerge, Apple’s program is expected to undergo further development to remain effective and relevant.
Potential Expansion of Scope and Reward Structure
Apple’s bug bounty program could expand its scope to encompass a wider range of products and services, including emerging technologies like augmented reality (AR) and artificial intelligence (AI). The program could also explore the inclusion of new vulnerability categories, such as those related to privacy and data security. Additionally, Apple might consider enhancing its reward structure to incentivize the discovery of high-impact vulnerabilities, potentially offering tiered rewards based on the severity and complexity of the discovered issue.
Emerging Security Challenges
Apple’s bug bounty program can play a vital role in addressing emerging security challenges. As the use of Internet of Things (IoT) devices proliferates, Apple could expand its program to include these devices, encouraging researchers to identify vulnerabilities in connected home appliances, smartwatches, and other IoT devices. Additionally, the increasing adoption of cloud computing and mobile applications presents new opportunities for attackers. Apple’s bug bounty program could be expanded to incentivize the discovery of vulnerabilities in its cloud infrastructure and mobile applications.
Benefits and Drawbacks of Apple’s Bug Bounty Program
| Benefit | Drawback |
|---|---|
| Improved security posture by identifying and mitigating vulnerabilities | Potential for disclosing vulnerabilities before they can be patched, leading to security risks |
| Enhanced reputation and trust among users by demonstrating a commitment to security | Possibility of attracting malicious actors who exploit the program for personal gain |
| Access to a diverse pool of security researchers with specialized expertise | The cost of managing and administering the program, including reward payouts |
Apple’s bug bounty program is a bold step towards a more transparent and collaborative security ecosystem. It’s a testament to the company’s commitment to security and a recognition of the value of crowdsourced security research. As Apple continues to evolve its program, we can expect to see even more significant contributions from the security community, ultimately making Apple products even more secure for users worldwide.
Apple’s new bug bounty program is a hot topic, and for good reason. It’s all about finding and fixing vulnerabilities before they become a major headache. But while Apple is focusing on the digital world, there are other companies looking to the stars. Check out asteroid mining startup Astroforge’s recent demonstration mission , which shows the challenges and triumphs of exploring new frontiers.
Maybe one day, bug bounty programs will be used to protect space-based infrastructure, too!
 Standi Techno News
Standi Techno News