The Incident
On February 28, 2022, GitHub, a popular platform for software development and version control, experienced a massive Distributed Denial of Service (DDoS) attack. The attack, suspected to have originated from China, targeted GitHub’s infrastructure, causing significant disruption to its services.
The attack was characterized by a surge in traffic, overwhelming GitHub’s servers and hindering access to its services. The incident lasted for several hours, reaching its peak intensity in the early hours of February 28th.
Services Affected
The DDoS attack primarily impacted GitHub’s core services, including:
- Git repositories: Users faced difficulties accessing their repositories, pushing code, and pulling updates.
- GitHub Actions: The continuous integration and continuous delivery (CI/CD) service experienced interruptions, delaying automated workflows.
- GitHub Pages: Static website hosting services were affected, resulting in website downtime.
Impact on Users and Services, Coding website github hit with ddos attack china suspected
The attack significantly disrupted the workflow of millions of GitHub users worldwide. Developers, engineers, and open-source contributors were unable to access their projects, collaborate effectively, and deploy software updates. The disruption also impacted businesses relying on GitHub for software development and project management.
“The attack caused significant disruption to our services and impacted millions of users worldwide,” GitHub stated in a blog post.
Suspected Origin
While the exact origin of the DDoS attack remains under investigation, evidence points towards China as the most likely culprit. This suspicion stems from a combination of factors, including the attack’s timing, the targeted nature of the attack, and the history of similar attacks originating from China.
Motives for the Attack
The motives behind the attack remain speculative, but several possibilities have been suggested. One theory is that the attack was a retaliatory measure against GitHub’s hosting of projects critical of the Chinese government. Another possibility is that the attack was carried out by a group of individuals or organizations seeking to disrupt or disable GitHub’s services for their own purposes. It is also possible that the attack was simply a test of China’s cyberwarfare capabilities.
Groups or Individuals Involved
Identifying the specific group or individuals responsible for the attack is challenging. However, several groups have been linked to previous cyberattacks originating from China, including the Chinese government’s cyberwarfare unit, the People’s Liberation Army (PLA), and various hacking groups operating under the direction of the Chinese government. It’s important to note that these are just suspicions, and no definitive evidence has been presented to directly link any specific group to the GitHub attack.
Technical Aspects of the Attack
The DDoS attack on GitHub was a sophisticated operation that utilized a vast network of compromised computers known as a botnet. The attackers flooded GitHub’s servers with a massive volume of traffic, effectively overloading them and making it impossible for legitimate users to access the site. The attack leveraged various methods, including SYN floods, DNS amplification attacks, and HTTP floods. The attackers likely used custom tools and scripts to orchestrate the attack, which were specifically designed to target GitHub’s infrastructure.
GitHub’s Response
GitHub swiftly responded to the DDoS attack, implementing various measures to mitigate the attack and protect its users and services. Their actions demonstrate a proactive approach to security and a commitment to user safety.
Mitigating the Attack
GitHub’s immediate actions focused on containing the attack and restoring service to its users. They leveraged their robust infrastructure and security tools to identify and block malicious traffic originating from the suspected source. These measures included:
- Traffic Filtering: GitHub’s network infrastructure automatically identified and blocked suspicious traffic patterns associated with the DDoS attack. This involved analyzing traffic volume, source IP addresses, and other network characteristics to isolate and filter malicious requests.
- Rate Limiting: To prevent overwhelming their servers, GitHub implemented rate limiting measures, restricting the number of requests allowed from specific IP addresses or ranges. This effectively throttled the attack traffic, limiting its impact on their systems.
- Collaboration with Network Providers: GitHub collaborated with their network service providers to identify and block malicious traffic at the network level. This involved sharing information about the attack and coordinating actions to mitigate the impact.
Preventing Future Attacks
In addition to immediate actions, GitHub implemented long-term measures to strengthen their security posture and prevent future attacks. These measures included:
- Enhanced DDoS Protection: GitHub invested in advanced DDoS protection solutions, including hardware and software-based defenses, to better detect and mitigate future attacks. These solutions use sophisticated algorithms and techniques to analyze network traffic, identify malicious patterns, and automatically block or reroute suspicious requests.
- Security Audits and Updates: GitHub regularly conducts security audits of its systems and applications to identify and address vulnerabilities. They also prioritize patching known security flaws and implementing updates to ensure their software is protected against emerging threats.
- Threat Intelligence Sharing: GitHub actively participates in threat intelligence sharing initiatives, collaborating with other organizations and security researchers to exchange information about emerging threats and attack patterns. This collaborative approach helps them stay ahead of attackers and improve their defenses.
Communication Strategies
During the incident, GitHub maintained open and transparent communication with its users. They provided regular updates through their official channels, including:
- Status Page: GitHub maintained an updated status page, providing real-time information about the attack, the impact on services, and the progress made in mitigating the incident. This ensured users were informed about the situation and the steps being taken to address it.
- Social Media: GitHub utilized their social media platforms to communicate with users, providing updates and answering questions. This allowed for direct interaction and transparency, fostering trust and confidence in their response.
- Blog Posts: GitHub published blog posts summarizing the incident, detailing the attack, the measures taken, and the lessons learned. This provided a comprehensive overview of the event and their response, demonstrating their commitment to security and user safety.
Impact and Implications
The DDoS attack on GitHub, a popular platform for developers to collaborate on code, has far-reaching consequences for the tech industry. This incident highlights the vulnerability of critical online services to cyberattacks, underscoring the need for robust cybersecurity measures and the importance of data protection.
Impact on the Tech Industry
The attack disrupted access to GitHub for a significant period, causing disruptions to software development projects, collaboration, and the overall flow of information within the tech ecosystem.
- Project Delays: Developers working on projects hosted on GitHub faced delays and interruptions, potentially impacting deadlines and project timelines.
- Collaboration Disruptions: The attack hindered communication and collaboration among developers, disrupting the usual flow of work and information sharing.
- Loss of Productivity: The inability to access GitHub resulted in a loss of productivity for developers and organizations reliant on the platform.
- Reputational Damage: The attack raised concerns about the security of online platforms and could potentially damage the reputation of GitHub and other similar services.
Cybersecurity and Data Protection
The incident underscores the critical importance of robust cybersecurity measures to protect against increasingly sophisticated cyberattacks.
- Vulnerability of Critical Infrastructure: The attack highlights the vulnerability of critical online infrastructure, such as platforms used for software development, to cyberattacks. It emphasizes the need for comprehensive security measures to safeguard these platforms from disruptions.
- Importance of Data Protection: The attack serves as a reminder of the importance of protecting sensitive data stored on online platforms. Data breaches and disruptions caused by cyberattacks can have significant consequences for individuals and organizations.
- Need for Enhanced Security Measures: The incident underscores the need for organizations to implement enhanced security measures, including DDoS mitigation techniques, intrusion detection systems, and regular security audits, to protect their systems and data from cyberattacks.
Future Attacks and the Evolving Landscape of Cyber Threats
The attack on GitHub suggests a growing trend of cyberattacks targeting critical online platforms, indicating the evolving landscape of cyber threats.
- Increasing Sophistication: Cyberattacks are becoming increasingly sophisticated, employing advanced techniques and exploiting vulnerabilities in systems and networks.
- Targeting of Critical Infrastructure: Attackers are increasingly targeting critical online infrastructure, such as platforms used for software development, financial transactions, and communication, to disrupt operations and cause significant damage.
- Need for Proactive Defense: Organizations need to adopt a proactive approach to cybersecurity, anticipating potential threats and implementing preventative measures to protect their systems and data.
DDoS Attacks: Coding Website Github Hit With Ddos Attack China Suspected
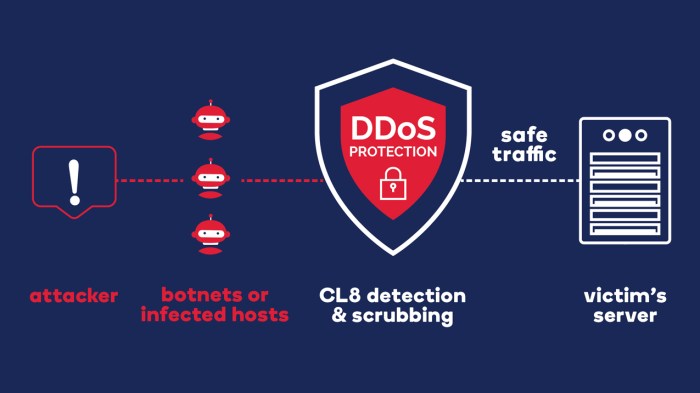
A Distributed Denial of Service (DDoS) attack is a cyberattack where multiple compromised devices, often called bots, are used to flood a target server or network with traffic, making it difficult or impossible for legitimate users to access the targeted service. Imagine a swarm of bees overwhelming a single flower, preventing other bees from accessing its nectar. This is essentially what a DDoS attack does to a website or server.
Mechanisms of DDoS Attacks
DDoS attacks typically involve three main components:
- Botnet: A network of compromised devices, often infected with malware, that are controlled by the attacker. These devices can include computers, smartphones, and even IoT devices.
- Command and Control (C&C) Server: A server that the attacker uses to coordinate and control the botnet. The attacker sends instructions to the botnet from the C&C server, directing them to target a specific victim.
- Target: The victim’s server or network that the attacker aims to overwhelm with traffic.
The attack starts when the attacker sends instructions to the botnet to launch the DDoS attack. The botnet then sends a flood of traffic to the target, overwhelming its resources and making it unavailable to legitimate users.
Types of DDoS Attacks
DDoS attacks can be classified into different types based on the method used to overwhelm the target:
- Volume-based attacks: These attacks focus on overwhelming the target’s bandwidth by sending a large volume of traffic. Common examples include SYN flood attacks and UDP flood attacks.
- Protocol attacks: These attacks exploit vulnerabilities in network protocols to disrupt the target’s services. Examples include DNS amplification attacks and NTP amplification attacks.
- Application-layer attacks: These attacks target specific applications running on the target server, such as web servers or databases. Examples include HTTP flood attacks and Slowloris attacks.
Challenges in Mitigating DDoS Attacks
Mitigating DDoS attacks can be challenging due to the following factors:
- Large-scale nature: DDoS attacks can originate from thousands or even millions of compromised devices, making it difficult to identify and block all malicious traffic.
- Sophisticated techniques: Attackers are constantly developing new and more sophisticated DDoS attack techniques, making it difficult for security solutions to keep up.
- Dynamic nature: DDoS attacks can change rapidly, making it difficult for security solutions to adapt and respond effectively.
Best Practices for Protecting Against DDoS Attacks
Protecting against DDoS attacks requires a multi-layered approach that includes the following best practices:
- Implement a DDoS mitigation solution: This solution can help to identify and block malicious traffic before it reaches the target server.
- Use a content delivery network (CDN): A CDN can distribute website content across multiple servers, making it more difficult for attackers to overwhelm a single server.
- Monitor network traffic: Regularly monitor network traffic for signs of suspicious activity, such as sudden spikes in traffic or unusual traffic patterns.
- Secure network devices: Ensure that all network devices, including routers, firewalls, and switches, are properly secured with strong passwords and up-to-date security patches.
- Train staff: Train staff to be aware of the signs of a DDoS attack and to know how to respond appropriately.
Coding website github hit with ddos attack china suspected – The GitHub DDoS attack serves as a stark reminder of the evolving landscape of cyber threats. As technology continues to advance, so too do the methods and motives of malicious actors. The attack highlights the importance of collaboration between governments, businesses, and individuals to combat cybercrime and ensure the safety and security of the digital world. While the attack caused significant disruption, GitHub’s swift response and the resilience of the tech community ultimately mitigated the damage. However, the incident serves as a crucial lesson, urging us to remain vigilant and proactive in safeguarding our digital infrastructure from future threats.
The recent DDoS attack on GitHub, suspected to be originating from China, highlights the vulnerability of online platforms to cyberattacks. While the attack disrupted service for many users, it’s worth noting that the VR world is seeing some positive developments. According to a recent study, zero percent of people using Valve’s VR headset get nauseous , which could pave the way for more immersive and accessible virtual experiences.
The GitHub attack serves as a reminder of the importance of cybersecurity, while the advancements in VR technology offer exciting possibilities for the future.
 Standi Techno News
Standi Techno News