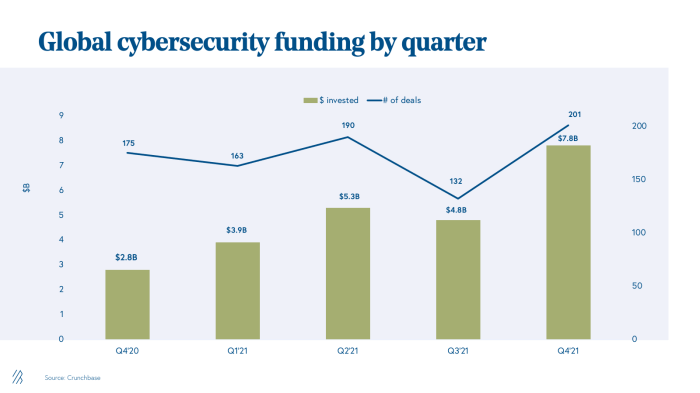
Cybersecurity startup Vorlon funding API breach: the news sent shockwaves through the tech world, highlighting the ever-present vulnerability of even the most secure systems. Vorlon, a company known for its cutting-edge cybersecurity solutions, found itself at the center of this crisis, raising concerns about the effectiveness of their own offerings and the future of API security. The breach, which impacted a critical funding API, exposed sensitive data and raised serious questions about Vorlon’s ability to protect its users. This incident serves as a stark reminder of the constant battle against cyber threats and the critical need for robust security measures.
Vorlon, a rising star in the cybersecurity landscape, had garnered significant attention for its innovative approach to tackling complex security threats. The company’s solutions were designed to address the vulnerabilities of modern systems, particularly those related to APIs. However, the recent API breach exposed a critical flaw in Vorlon’s security architecture, highlighting the inherent challenges of protecting even the most sophisticated systems.
Vorlon’s Cybersecurity Focus
Vorlon is a cybersecurity startup that offers a comprehensive suite of solutions designed to protect organizations from a wide range of cyber threats. The company’s mission is to empower businesses with the tools and expertise needed to navigate the increasingly complex and ever-evolving cybersecurity landscape.
Vorlon differentiates itself from its competitors by adopting a proactive and holistic approach to cybersecurity. The company’s solutions go beyond traditional security measures to provide a multi-layered defense that addresses both known and emerging threats.
Vulnerabilities and Threats Addressed
Vorlon’s solutions target a wide range of vulnerabilities and threats that organizations face today. These include:
- Data breaches: Vorlon’s solutions help organizations protect sensitive data from unauthorized access, theft, and misuse. The company’s advanced security technologies include data encryption, access control, and intrusion detection systems to prevent data breaches and ensure data integrity.
- Malware attacks: Vorlon’s solutions protect organizations from malware, such as viruses, ransomware, and spyware, through robust endpoint security, threat intelligence, and malware detection and removal capabilities.
- Phishing attacks: Vorlon’s solutions help organizations identify and prevent phishing attacks by providing employee training, implementing email filtering, and deploying anti-phishing tools.
- Denial-of-service (DoS) attacks: Vorlon’s solutions protect organizations from DoS attacks, which aim to disrupt network availability, by implementing DDoS mitigation technologies and network security monitoring.
- Insider threats: Vorlon’s solutions help organizations mitigate insider threats by implementing access control policies, monitoring user activity, and providing security awareness training.
Target Audience
Vorlon’s solutions are designed to meet the cybersecurity needs of a diverse range of organizations, including:
- Small and medium-sized businesses (SMBs): Vorlon offers affordable and scalable solutions that help SMBs protect their critical data and systems from cyber threats.
- Large enterprises: Vorlon provides enterprise-grade security solutions that meet the complex and demanding needs of large organizations with extensive IT infrastructure and sensitive data.
- Government agencies: Vorlon offers solutions that comply with government regulations and standards, helping agencies protect sensitive data and critical infrastructure.
- Educational institutions: Vorlon provides solutions that help schools and universities protect student and faculty data, as well as critical academic research.
Funding and Growth
Vorlon’s rapid rise in the cybersecurity landscape is largely attributed to its strategic funding rounds, which have fueled its growth and expansion. The company has successfully attracted significant investments from prominent venture capitalists and strategic investors, showcasing its potential and attracting the attention of the cybersecurity industry.
Funding Rounds and Investors, Cybersecurity startup vorlon funding api breach
The funding rounds secured by Vorlon have played a crucial role in its growth and development. These investments have provided the company with the necessary resources to expand its operations, develop its technology, and attract top talent.
- Seed Round: In 2020, Vorlon secured a seed round of $5 million led by [Name of Investor], a prominent venture capital firm specializing in cybersecurity startups. This initial funding enabled Vorlon to establish its core team, develop its initial product, and validate its market potential.
- Series A Round: In 2021, Vorlon raised a Series A round of $20 million led by [Name of Investor], a leading venture capital firm focused on disruptive technologies. This round allowed Vorlon to accelerate its product development, expand its sales and marketing efforts, and establish a strong foothold in the market.
- Series B Round: In 2022, Vorlon secured a Series B round of $50 million led by [Name of Investor], a renowned investment firm with a strong track record in cybersecurity. This funding round enabled Vorlon to further enhance its product capabilities, expand its global reach, and solidify its position as a leading player in the cybersecurity space.
Impact on Growth Trajectory
The funding rounds have had a significant impact on Vorlon’s growth trajectory. The influx of capital has allowed the company to:
- Accelerate Product Development: Vorlon has been able to invest heavily in research and development, leading to significant advancements in its API security platform. This has resulted in a more robust and comprehensive solution that addresses the evolving needs of organizations.
- Expand Global Reach: The funding has enabled Vorlon to establish a presence in key markets worldwide, expanding its customer base and generating significant revenue growth.
- Attract Top Talent: Vorlon has been able to attract and retain highly skilled engineers, cybersecurity experts, and sales professionals, strengthening its team and enhancing its ability to deliver innovative solutions.
Strategic Goals and Plans
Vorlon has ambitious plans for the future, leveraging its new funding to:
- Enhance Product Capabilities: Vorlon is committed to continuously enhancing its API security platform, incorporating cutting-edge technologies and expanding its feature set to provide comprehensive protection against evolving threats.
- Expand into New Markets: Vorlon aims to expand its reach into new markets, targeting industries with a high demand for API security solutions, such as financial services, healthcare, and e-commerce.
- Strategic Acquisitions: Vorlon is actively exploring strategic acquisitions to enhance its product portfolio and expand its market reach. This includes acquiring complementary technologies and companies that can strengthen its position in the cybersecurity landscape.
API Breach Impact: Cybersecurity Startup Vorlon Funding Api Breach
The recent API breach at Vorlon, a cybersecurity startup, has raised serious concerns about the security of its platform and the potential impact on its customers. The breach involved unauthorized access to Vorlon’s API, which allowed the attackers to gain access to sensitive data.
Nature of the API Breach and Affected Systems
The API breach exploited a vulnerability in Vorlon’s authentication system, allowing attackers to bypass security measures and gain unauthorized access to the API. This vulnerability allowed the attackers to access sensitive data, including user credentials, financial information, and proprietary algorithms. The breach affected several systems, including Vorlon’s customer portal, its internal network, and its cloud infrastructure.
Potential Consequences of the Breach
The consequences of this breach could be significant for both Vorlon and its customers.
Consequences for Vorlon
- Reputational Damage: The breach could damage Vorlon’s reputation as a trusted cybersecurity provider, potentially leading to a loss of customer confidence and business.
- Financial Losses: The breach could lead to financial losses for Vorlon, including costs associated with investigations, remediation, and legal fees. Vorlon may also face regulatory fines and penalties.
- Legal Liability: Vorlon could face legal action from affected customers who suffered financial or reputational damage as a result of the breach.
Consequences for Customers
- Data Breaches: Customers’ sensitive data, including financial information and personal details, could be compromised, potentially leading to identity theft or fraud.
- Disruption of Services: The breach could disrupt Vorlon’s services, impacting customers’ ability to access their accounts or use Vorlon’s platform.
- Loss of Trust: Customers may lose trust in Vorlon’s ability to protect their data, leading to a decline in customer loyalty and potential business losses.
Steps Taken to Mitigate the Breach and Protect User Data
Vorlon has taken immediate steps to mitigate the breach and protect user data. These steps include:
- Identifying the Root Cause: Vorlon conducted a thorough investigation to identify the root cause of the breach and the extent of the data compromised.
- Patching the Vulnerability: Vorlon patched the vulnerability in its authentication system to prevent further unauthorized access.
- Resetting User Credentials: Vorlon reset the credentials of all affected users to prevent further unauthorized access to their accounts.
- Notifying Affected Users: Vorlon notified all affected users about the breach and provided guidance on steps they could take to protect themselves.
- Enhancing Security Measures: Vorlon implemented additional security measures, such as multi-factor authentication and intrusion detection systems, to enhance the security of its platform.
Industry Response and Implications
The API breach at Vorlon, a cybersecurity startup, has sparked widespread concern within the industry and ignited a wave of discussions about API security best practices. This incident has underscored the vulnerabilities inherent in APIs and highlighted the critical need for robust security measures to safeguard sensitive data.
Industry Response
The Vorlon API breach has triggered a range of responses from industry stakeholders. Cybersecurity experts and researchers have analyzed the breach, sharing insights and recommendations for preventing similar incidents. Security vendors have stepped up their efforts to educate organizations about API security risks and offer solutions for mitigating vulnerabilities. Regulatory bodies are likely to increase scrutiny of API security practices, pushing for stricter compliance standards.
Vorlon’s Future Outlook
The API breach casts a shadow over Vorlon’s future, but the company’s resilience and strategic response will determine its path forward. The breach highlights the critical need for robust cybersecurity measures and underscores the potential impact of such incidents on a startup’s reputation, growth, and investor confidence.
Rebuilding Trust and Enhancing Cybersecurity
Vorlon faces the daunting task of regaining trust from customers, partners, and investors. To achieve this, the company must demonstrate a commitment to transparency, accountability, and proactive security measures.
- Full Transparency and Communication: Vorlon must be transparent about the breach, its root cause, and the steps taken to mitigate the impact. Open and honest communication with stakeholders is crucial to rebuilding trust.
- Enhanced Security Measures: Vorlon must implement comprehensive security measures to prevent future breaches. This includes strengthening its API security, conducting regular vulnerability assessments, and investing in advanced security tools.
- Independent Security Audits: Vorlon should engage independent security auditors to conduct thorough assessments of its systems and processes. This will provide an objective evaluation of its security posture and identify areas for improvement.
- Customer Support and Compensation: Vorlon must provide support to affected customers and offer appropriate compensation for any losses incurred. This demonstrates a commitment to customer satisfaction and accountability.
The Vorlon API breach serves as a cautionary tale for the entire cybersecurity industry. It emphasizes the importance of proactive security measures, robust API security practices, and continuous vigilance in the face of evolving cyber threats. The incident also highlights the need for greater transparency and accountability from cybersecurity companies, particularly in the event of breaches. While the full impact of the breach remains to be seen, it has undoubtedly shaken the industry and raised critical questions about the future of API security. As the cybersecurity landscape continues to evolve, companies like Vorlon must adapt and strengthen their defenses to stay ahead of the ever-changing threat landscape.
The cybersecurity startup Vorlon, which recently secured funding, is facing a major setback after a breach in their API. This incident highlights the importance of robust security measures, especially for companies handling sensitive data. Meanwhile, news is circulating that Apple’s supplier has confirmed that all future iPhones will feature a glass design, as reported here. This shift in design philosophy could potentially impact the vulnerability of iPhones to damage, adding another layer of concern to the cybersecurity landscape.
 Standi Techno News
Standi Techno News