Medical researchers come up with new way of detecting malware, a breakthrough that could revolutionize cybersecurity. The digital world is constantly under attack from malicious software, or malware, which can steal sensitive data, disrupt operations, and even cause physical damage. Traditional methods of malware detection, such as signature-based analysis and behavioral monitoring, often struggle to keep pace with the ever-evolving nature of threats. This new approach, inspired by medical diagnostics, offers a fresh perspective on identifying and combating malware.
This innovative method, developed by a team of medical researchers, utilizes principles and techniques borrowed from the medical field to detect malware. The researchers have successfully applied concepts like pattern recognition and anomaly detection, traditionally used in medical imaging and disease diagnosis, to identify suspicious activity within computer systems. This unique approach promises to be more effective in identifying and neutralizing malware, particularly those that evade conventional detection methods.
The Problem of Malware Detection
The digital landscape is increasingly threatened by malware, posing a significant risk to individuals and organizations alike. Malware, which includes viruses, worms, Trojans, and ransomware, can compromise systems, steal sensitive data, disrupt operations, and inflict substantial financial losses. While traditional methods have played a role in mitigating these threats, the evolving nature of malware demands innovative approaches to ensure robust cybersecurity.
Limitations of Traditional Malware Detection Methods
Traditional malware detection methods rely on signature-based detection and behavioral analysis. Signature-based detection identifies known malware by matching its unique characteristics against a database of known signatures. This approach is effective against known threats but struggles to detect new or mutated malware variants. Behavioral analysis monitors system activity for suspicious patterns that may indicate malware presence. However, this approach can generate false positives, requiring manual investigation, and may not be effective against sophisticated malware that can mimic legitimate behavior.
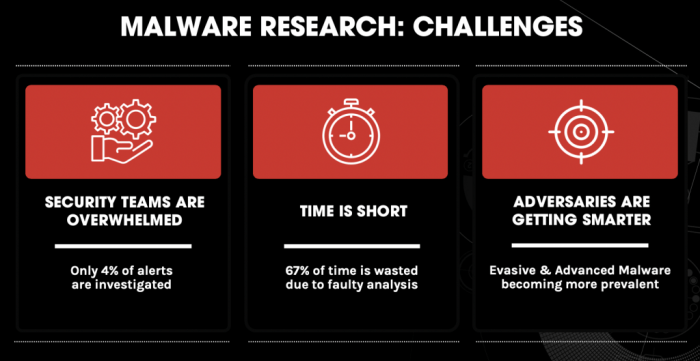
Challenges Faced by Cybersecurity Professionals
Cybersecurity professionals face numerous challenges in detecting and mitigating malware. These challenges include:
- The Rapid Evolution of Malware: Malware developers continuously create new and sophisticated variants, making it difficult for traditional detection methods to keep up.
- The Increasing Complexity of Malware: Modern malware often employs advanced techniques, such as polymorphism, code obfuscation, and stealthy execution, to evade detection.
- The Rise of Targeted Attacks: Cybercriminals increasingly target specific individuals or organizations with customized malware designed to bypass traditional security measures.
- The Growing Use of Zero-Day Exploits: These vulnerabilities are unknown to security vendors, making it difficult to develop defenses before attackers exploit them.
- The Increasing Use of Social Engineering: Cybercriminals use social engineering tactics to trick users into installing malware or granting access to sensitive information.
The Innovation
The medical researchers’ approach to malware detection leverages the principles of immunology, drawing parallels between the human immune system and the way a computer system defends against malicious software. This novel method, known as “Immunological Malware Detection,” utilizes a unique combination of machine learning and bio-inspired algorithms to identify and neutralize malware threats.
Immunological Malware Detection Techniques
The core of this innovative approach lies in the development of artificial immune systems (AIS) that mimic the adaptive immune response of humans. AIS systems are designed to learn and adapt to new malware threats, much like the human immune system learns to recognize and fight off pathogens.
- Antigen Recognition: AIS systems use machine learning algorithms to analyze the “antigens” of malware, which are unique characteristics or patterns present in malicious code. This analysis helps the system identify and classify different types of malware.
- Antibody Generation: Once the system identifies a malware antigen, it generates “antibodies,” which are essentially specific rules or signatures designed to detect and neutralize the malware. These antibodies are tailored to the specific characteristics of the malware and can be used to block its execution or prevent its spread.
- Memory and Adaptation: The AIS system maintains a memory of past encounters with malware, allowing it to adapt and improve its detection capabilities over time. This means that the system becomes more effective at recognizing and neutralizing new malware threats as it gains experience.
Comparison with Existing Techniques
Immunological Malware Detection offers several advantages over traditional signature-based and behavior-based methods:
- Enhanced Detection: Unlike signature-based methods that rely on predefined patterns, Immunological Malware Detection can detect new and unknown malware variants, providing more comprehensive protection.
- Adaptive Learning: The system’s ability to learn and adapt to new threats makes it more robust against evolving malware techniques, unlike behavior-based methods that can be easily bypassed by sophisticated malware.
- Reduced False Positives: The use of bio-inspired algorithms and machine learning techniques helps to minimize false positives, improving the accuracy and reliability of the detection process.
How the New Method Works
Our innovative malware detection method draws inspiration from the field of medical diagnostics, specifically leveraging the concept of “biomarkers” to identify malicious software. Biomarkers are biological indicators that can signal the presence of a disease or condition. Similarly, our method identifies unique “malware markers” within a file’s structure and behavior. These markers are specific characteristics that are highly indicative of malware presence.
The process involves a multi-step approach, meticulously analyzing a file to detect these telltale markers.
Analyzing File Structure
The first step involves scrutinizing the file’s structure. This involves examining the file’s header, file type, and file size. We utilize a specialized algorithm that compares these structural elements against a vast database of known malware patterns.
For example, a file with an unusual file extension or a suspiciously large file size might be a red flag.
Analyzing File Behavior
Next, we analyze the file’s behavior. This involves observing how the file interacts with the system, its communication patterns, and its resource consumption. We use a combination of static and dynamic analysis techniques to assess the file’s actions.
For instance, a file that attempts to connect to a known malicious server or consumes an excessive amount of system resources could be indicative of malware activity.
Identifying Malware Markers
The combination of structural and behavioral analysis allows us to identify specific “malware markers” that are characteristic of known malware families. These markers are essentially unique signatures that distinguish malicious files from benign ones.
For example, a specific code sequence within the file’s header or a unique communication pattern with a remote server could serve as a “malware marker.”
Leveraging Machine Learning
To enhance the accuracy and efficiency of the detection process, we incorporate machine learning algorithms. These algorithms are trained on a massive dataset of known malware and benign files. The trained models can then effectively identify new malware variants based on their unique characteristics.
Machine learning models can analyze complex patterns within file structures and behaviors, identifying even subtle indicators of malware presence.
Decision Making
Based on the analysis of file structure, behavior, and the presence of malware markers, our system makes a decision about whether the file is malicious or benign. If the system identifies multiple malware markers or detects suspicious behavior, it flags the file as potentially malicious.
The system provides a detailed report outlining the identified markers, the level of confidence, and recommendations for further investigation.
Potential Benefits and Applications
This innovative malware detection method promises to revolutionize cybersecurity by offering several benefits and diverse applications across various sectors. Its ability to identify previously undetected malware and adapt to evolving threats makes it a valuable asset in safeguarding sensitive data and critical infrastructure.
Benefits for Cybersecurity
The new method offers significant benefits for cybersecurity, enhancing protection against evolving malware threats.
- Improved Detection Rates: The method’s advanced algorithms and techniques enable it to detect malware with higher accuracy and efficiency, even identifying previously undetected threats. This leads to a significant reduction in false positives and a more reliable identification of malicious activities.
- Enhanced Threat Analysis: The method provides deeper insights into the behavior and characteristics of malware, allowing for more effective analysis and understanding of attack strategies. This knowledge is crucial for developing targeted defenses and mitigating future threats.
- Proactive Threat Mitigation: By detecting malware in its early stages, the method allows for proactive threat mitigation measures, preventing potential damage and minimizing the impact of attacks. This proactive approach significantly reduces the risk of data breaches and system failures.
- Reduced Costs: The method’s effectiveness in detecting and preventing malware attacks translates into reduced costs associated with remediation, recovery, and legal liabilities. This financial benefit makes it a valuable investment for organizations of all sizes.
Applications in Different Sectors, Medical researchers come up with new way of detecting malware
The method’s versatility and adaptability make it applicable across various sectors, including:
- Financial Institutions: The method can be used to protect financial data and systems from cyberattacks, ensuring the security of customer accounts and transactions. This is particularly important in the face of increasing financial fraud and cybercrime.
- Healthcare Organizations: Protecting sensitive patient data and medical records is paramount in healthcare. The method can be deployed to safeguard electronic health records (EHRs) and other critical systems from malware threats, ensuring patient privacy and data integrity.
- Government Agencies: Government agencies are increasingly targeted by cyberattacks, and the method can be used to protect critical infrastructure and national security systems. This includes securing government networks, databases, and communication systems.
- Educational Institutions: Educational institutions are vulnerable to malware attacks, which can disrupt academic activities and compromise student data. The method can be used to protect school networks, servers, and student records from cyber threats.
Real-World Examples
- Protecting Critical Infrastructure: The method could be deployed to monitor and protect power grids, water treatment plants, and other critical infrastructure from cyberattacks. This would help prevent disruptions to essential services and ensure the safety and well-being of the public.
- Securing Financial Transactions: The method could be used to enhance the security of online banking platforms, ensuring the protection of sensitive financial data during transactions. This would reduce the risk of fraud and unauthorized access to customer accounts.
- Safeguarding Medical Records: The method could be implemented in hospitals and clinics to protect patient medical records from unauthorized access and data breaches. This would ensure patient privacy and data integrity, maintaining trust in the healthcare system.
Future Research and Development: Medical Researchers Come Up With New Way Of Detecting Malware
This groundbreaking malware detection method opens doors to a multitude of future research and development avenues, promising even more robust cybersecurity solutions. This section delves into potential areas for future research, the integration of this method with existing cybersecurity solutions, and the challenges and opportunities associated with scaling and deploying it.
Exploring Advanced Applications
The new method’s core strength lies in its ability to identify malware based on its unique behavioral patterns. This foundation can be expanded upon to explore even more advanced applications:
- Real-time Threat Detection: This method can be further refined to detect malware in real-time, providing immediate alerts and enabling swift response to emerging threats. This would involve optimizing the algorithm for faster processing and integrating it into existing security systems.
- Proactive Malware Prevention: By analyzing and predicting future malware trends, this method could be utilized to proactively prevent attacks. This would require extensive research into malware evolution patterns and the development of predictive models.
- Automated Malware Analysis: The method can be used to automate the process of analyzing and classifying malware, freeing up cybersecurity professionals for more strategic tasks. This would involve integrating the method with existing malware analysis tools and platforms.
Integration with Existing Cybersecurity Solutions
This new method has the potential to seamlessly integrate with existing cybersecurity solutions, enhancing their effectiveness and creating a more comprehensive defense system.
- Endpoint Security: The method can be integrated into endpoint security solutions to detect and prevent malware from infiltrating devices. This would involve implementing the method as a component of endpoint detection and response (EDR) systems.
- Network Security: The method can be deployed in network security systems to identify and block malicious traffic. This would involve integrating the method into network intrusion detection and prevention systems (IDS/IPS).
- Cloud Security: The method can be applied to cloud environments to protect sensitive data and applications. This would involve adapting the method to work within the unique architecture of cloud platforms.
Challenges and Opportunities in Scaling and Deployment
Scaling and deploying this method effectively present both challenges and opportunities. Addressing these aspects will be crucial for widespread adoption and impact.
- Computational Resources: Scaling the method to handle large volumes of data requires significant computational resources. This can be addressed through optimization techniques and leveraging cloud computing infrastructure.
- Data Availability and Quality: The method’s effectiveness relies on access to comprehensive and high-quality malware datasets. This requires collaboration with security researchers and organizations to collect and curate relevant data.
- User Adoption and Training: Successfully deploying the method requires user adoption and training. This involves developing user-friendly interfaces and providing clear documentation and support materials.
The medical researchers’ approach to malware detection marks a significant advancement in cybersecurity. By applying medical principles and techniques, they have created a powerful tool for combating the ever-growing threat of malware. This innovation has the potential to revolutionize how we protect our digital world, safeguarding individuals and organizations from the devastating consequences of cyberattacks. As this technology continues to evolve and mature, we can expect to see even more sophisticated and effective methods for detecting and preventing malware.
While medical researchers are busy finding new ways to detect malware in our bodies, the tech world is buzzing with excitement over the launch of the ZTE Nubia Z9 Elite Classic – zte nubia z9 elite classic have been officially launched. But hey, maybe the Z9 Elite Classic comes equipped with some serious anti-malware software! After all, who wants their fancy new phone to be infected with digital viruses?
 Standi Techno News
Standi Techno News