Mozi botnet take down china sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail with hipwee author style and brimming with originality from the outset. Imagine a digital battlefield where a massive botnet, known as Mozi, wreaked havoc across the globe. This botnet, with its roots shrouded in mystery, unleashed a torrent of cyberattacks, targeting critical infrastructure, stealing sensitive data, and disrupting everyday life. At the heart of this cyberwarfare lies a complex relationship between Mozi and China, a story that intertwines technical prowess with geopolitical intrigue. This article delves into the captivating saga of the Mozi botnet, exploring its origins, its devastating capabilities, and the international effort to dismantle this digital menace.
The Mozi botnet, a global threat, emerged as a formidable force in the digital landscape. Its creators, cloaked in anonymity, unleashed a powerful weapon capable of launching devastating distributed denial-of-service (DDoS) attacks, stealing sensitive data, and remotely controlling infected devices. The botnet’s reach extended far and wide, infecting millions of devices across the globe, from humble home computers to critical infrastructure, leaving a trail of digital destruction in its wake. This cyber-weapon, with its tentacles reaching into every corner of the internet, presented a formidable challenge to cybersecurity experts and law enforcement agencies worldwide.
The Mozi Botnet
The Mozi botnet, a sophisticated and persistent threat, emerged in 2019 and quickly gained notoriety for its global reach and diverse capabilities. This botnet has evolved over time, constantly adapting to counter security measures and expanding its arsenal of malicious activities.
Origins and Evolution
The Mozi botnet’s origins can be traced back to a Chinese cybercrime group known as “Earth,” which has been active for several years. Mozi, named after a renowned Chinese philosopher, is believed to be the brainchild of this group. The botnet’s evolution is characterized by its relentless pursuit of new vulnerabilities, its ability to spread rapidly across networks, and its constant adaptation to evade detection.
Functionality
The Mozi botnet is a versatile tool that can be used for a wide range of malicious activities. Its core functionalities include:
- Distributed Denial-of-Service (DDoS) Attacks: Mozi can orchestrate large-scale DDoS attacks, overwhelming target servers with traffic and rendering them inaccessible. This can disrupt critical services, cripple online businesses, and cause significant financial damage.
- Data Theft: The botnet can steal sensitive information from infected devices, including personal data, financial credentials, and proprietary business data. This information can be used for identity theft, financial fraud, and other illicit purposes.
- Remote Control: Mozi’s operators can remotely control infected devices, allowing them to execute arbitrary commands, install malware, and spy on user activity. This gives them complete control over compromised systems, enabling them to launch further attacks or use the infected devices as proxies for other malicious activities.
Geographical Distribution
Mozi has infected devices in numerous countries around the world, making it a truly global threat. Its impact has been felt across various regions, including:
- North America: Mozi has been observed infecting devices in the United States, Canada, and Mexico. The botnet’s presence in North America highlights its ability to exploit vulnerabilities in devices across different geographical locations.
- Europe: Mozi has also been detected in European countries, including the United Kingdom, Germany, and France. Its widespread presence in Europe demonstrates its global reach and its ability to target critical infrastructure and businesses.
- Asia: The botnet’s origins in China have given it a strong foothold in Asia, with infections reported in countries like Japan, South Korea, and India. The botnet’s activity in Asia highlights the need for robust security measures to combat cyber threats.
Mozi Botnet and China: Mozi Botnet Take Down China
The Mozi botnet, a sophisticated and highly distributed network of compromised devices, has garnered significant attention for its global reach and disruptive capabilities. While the botnet’s origins and motivations remain somewhat shrouded in mystery, its complex relationship with China has sparked debate and scrutiny.
Potential Links to China
The Mozi botnet’s potential links to China are a subject of ongoing investigation and speculation. While definitive evidence is lacking, several factors suggest a possible connection. First, the botnet’s command and control infrastructure has been traced back to servers located in China. Second, the botnet’s malware code exhibits similarities to other malware strains known to have originated from China. Third, the botnet’s targeting of Chinese organizations, including government agencies and businesses, suggests a potential interest in espionage or cyberwarfare.
Chinese Cybersecurity Response
Chinese cybersecurity firms and government agencies played a crucial role in the takedown of the Mozi botnet. The National Computer Virus Emergency Response Center (CNCERT) issued warnings and advisories to Chinese users about the botnet’s threats. Chinese cybersecurity companies, such as Qihoo 360 and Tencent, actively developed and deployed tools to detect and remove the botnet’s malware. These efforts, in collaboration with international cybersecurity partners, contributed significantly to the botnet’s disruption.
Impact on China’s Digital Infrastructure and Economy
The Mozi botnet’s impact on China’s digital infrastructure and economy is multifaceted. The botnet’s widespread distribution and its ability to compromise critical systems posed a significant threat to national security and economic stability. The botnet’s targeting of Chinese organizations, including government agencies and financial institutions, raised concerns about data breaches, espionage, and cyberattacks. The botnet’s impact on China’s digital infrastructure could have far-reaching consequences, potentially disrupting critical services and undermining public trust in online security.
Takedown Strategies and Challenges
The takedown of the Mozi botnet was a complex and multifaceted operation that required the coordinated efforts of cybersecurity researchers, law enforcement agencies, and internet service providers (ISPs) worldwide. This global collaboration was crucial in dismantling this sophisticated botnet, which posed a significant threat to internet security.
Technical Challenges
Cybersecurity researchers and law enforcement agencies faced numerous technical challenges in taking down the Mozi botnet. The botnet’s architecture was designed to be resilient and difficult to detect and disrupt. Some of the key technical challenges included:
- Distributed nature: The Mozi botnet was distributed across a vast network of infected devices, making it difficult to identify and target all infected systems.
- Sophisticated evasion techniques: The botnet employed sophisticated evasion techniques, such as using dynamic domain names and encrypted communication channels, to avoid detection by security tools.
- Botnet’s resilience: The botnet was designed to be resilient to takedown attempts, with mechanisms for self-replication and rapid recovery after attacks.
- Limited visibility: The botnet’s activities were often hidden from view, making it difficult to track its spread and identify its command-and-control servers.
Takedown Strategies
The takedown of the Mozi botnet involved a multi-pronged approach, combining technical and legal strategies. Key strategies employed included:
- Sinkholing: This involved redirecting infected devices to a controlled server, preventing them from communicating with the botnet’s command-and-control infrastructure.
- Malware analysis: Researchers analyzed the Mozi botnet’s malware to understand its functionality, identify its vulnerabilities, and develop mitigation strategies.
- Collaboration with ISPs: Collaboration with ISPs was crucial to identify and remove infected devices from their networks. This involved working with ISPs to block malicious traffic, disable infected devices, and notify users about the threat.
- Law enforcement action: Law enforcement agencies investigated the botnet’s operators and took legal action to disrupt their activities. This involved seizing servers, shutting down websites, and pursuing criminal charges against individuals involved in the botnet’s operation.
Effectiveness of Takedown Strategies, Mozi botnet take down china
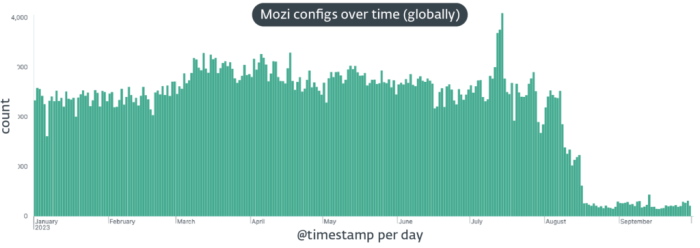
The takedown strategies employed against the Mozi botnet were largely successful in significantly reducing its activity. The botnet’s command-and-control infrastructure was disrupted, and its ability to spread and infect new devices was significantly curtailed. However, the botnet’s resilience and its ability to adapt and evolve presented ongoing challenges.
“While the takedown of the Mozi botnet was a significant victory, it highlights the ongoing need for collaboration between cybersecurity researchers, law enforcement agencies, and ISPs to combat the evolving threat of botnets.” – [Source: Cybersecurity Expert]
Lessons Learned and Future Implications
The Mozi botnet takedown offers valuable insights into the evolving nature of cyber threats and the importance of international collaboration in combating them. It underscores the need for robust cybersecurity practices and policies to protect against future attacks.
The Evolving Nature of Botnet Threats
The Mozi botnet incident highlights the ever-changing nature of botnet threats. Botnets are becoming increasingly sophisticated, utilizing advanced techniques like machine learning and artificial intelligence to evade detection and carry out attacks.
- Increased sophistication: Mozi’s ability to exploit vulnerabilities in network devices and its use of obfuscation techniques to hide its malicious activities demonstrate the increasing sophistication of botnets.
- Rapid evolution: Botnet operators are constantly adapting their tactics and strategies, making it challenging to stay ahead of them. This rapid evolution requires continuous monitoring and analysis to identify new threats and vulnerabilities.
- Global reach: Mozi’s widespread infection across multiple countries underscores the global nature of botnet threats. This highlights the need for international cooperation to effectively combat these threats.
The Importance of International Cooperation
The Mozi botnet takedown was a testament to the power of international collaboration in combating cyber threats. Multiple countries and organizations worked together to gather intelligence, share information, and coordinate takedown efforts.
- Information sharing: The ability to share threat intelligence and data between countries and organizations is crucial for effective botnet takedowns. This allows for a more comprehensive understanding of the threat and facilitates coordinated responses.
- Joint operations: International cooperation enables coordinated takedown operations, disrupting botnet infrastructure and preventing further attacks. This requires a high level of trust and coordination between different entities.
- Resource sharing: Collaboration allows countries and organizations to pool resources and expertise, enabling them to leverage specialized capabilities for botnet takedowns. This includes sharing technical knowledge, tools, and personnel.
Future Implications for Cybersecurity
The Mozi botnet incident has significant implications for future cybersecurity practices and policies. It underscores the need for a proactive approach to security, focusing on prevention, detection, and response.
- Enhanced security practices: Organizations need to adopt robust cybersecurity practices, including regular vulnerability assessments, patching systems promptly, and implementing multi-factor authentication. These measures can help prevent botnet infections and mitigate the impact of attacks.
- Improved threat intelligence: Continuous monitoring and analysis of threat intelligence are crucial for staying ahead of evolving botnet threats. This includes tracking emerging vulnerabilities, identifying new attack vectors, and understanding the tactics and strategies used by botnet operators.
- Strengthened international cooperation: The Mozi botnet takedown emphasizes the need for increased international cooperation in combating cyber threats. This includes developing frameworks for information sharing, establishing joint task forces, and promoting collaboration between cybersecurity agencies and organizations.
The takedown of the Mozi botnet serves as a stark reminder of the ever-evolving nature of cyber threats. This global cyberwarfare highlights the importance of international cooperation in combating these digital menaces. The lessons learned from this incident will shape cybersecurity practices and policies for years to come, as nations strive to protect their digital infrastructure and safeguard their citizens from the growing threat of cyberattacks. The saga of the Mozi botnet is a testament to the ingenuity of both the attackers and the defenders, a story that continues to unfold in the ever-changing landscape of cyberspace.
The Mozi botnet takedown in China was a major win for cybersecurity, showcasing the power of international collaboration. While we celebrate this victory, it’s also a reminder of the ever-evolving landscape of cyber threats. This underscores the importance of staying ahead of the curve, which is why you should check out our salesforce lookback 2023 for insights on the latest trends and best practices in the field.
With knowledge as our weapon, we can continue to fight back against malicious actors like those behind the Mozi botnet.
 Standi Techno News
Standi Techno News