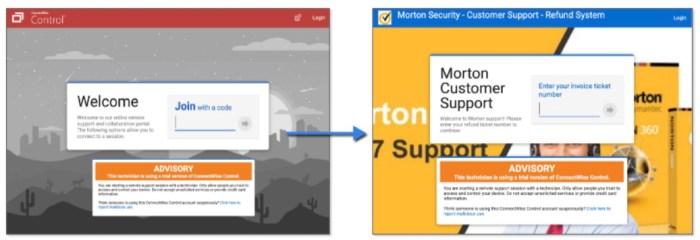
Researchers say easy to exploit security bugs in ConnectWise remote access software now under mass attack, a situation that has security experts raising serious concerns. ConnectWise, a popular provider of remote access solutions for IT professionals, has found itself in the crosshairs of a massive cyberattack. The vulnerability, discovered by researchers, allows attackers to easily exploit the software, potentially gaining access to sensitive data and systems. This attack highlights the ever-growing threat of cybercrime and the critical need for robust cybersecurity measures.
The vulnerability, which affects multiple versions of ConnectWise’s remote access software, allows attackers to bypass security measures and gain unauthorized access to systems. This could allow attackers to steal data, install malware, or even take control of the targeted systems. The scope of the attack is significant, with reports suggesting that numerous organizations across the globe are being targeted. This underscores the seriousness of the situation and the potential impact on businesses and individuals alike.
The ConnectWise Remote Access Software Vulnerability
ConnectWise, a leading provider of IT management solutions, recently discovered critical vulnerabilities in its remote access software. These vulnerabilities could allow attackers to gain unauthorized access to sensitive data and systems, potentially causing significant disruption to businesses.
Vulnerability Details
The vulnerabilities discovered in ConnectWise’s remote access software are primarily related to authentication and authorization flaws. These flaws could allow attackers to bypass security measures and gain access to systems without proper credentials.
Impact of the Vulnerabilities
The impact of these vulnerabilities is significant, as they could potentially allow attackers to:
- Gain unauthorized access to sensitive data, including customer information, financial records, and proprietary business data.
- Disrupt business operations by causing system outages or data breaches.
- Install malware or other malicious software on affected systems.
- Take control of affected systems and use them for malicious purposes, such as launching further attacks.
Mitigation Steps, Researchers say easy to exploit security bugs in connectwise remote access software now under mass attack
ConnectWise has released security updates to address these vulnerabilities. Users are strongly advised to apply these updates immediately to protect their systems. Additionally, users should consider implementing other security measures, such as:
- Using strong passwords and multi-factor authentication.
- Keeping software up-to-date.
- Implementing a robust security awareness program for employees.
- Monitoring network traffic for suspicious activity.
The Scope of the Attack
The recent ConnectWise vulnerability has resulted in a widespread attack, highlighting the vulnerability of remote access software and the potential for significant disruption. While ConnectWise has addressed the vulnerability, the ongoing attacks demonstrate the scale and persistence of the threat.
Evidence of Mass Attack
The evidence suggests that ConnectWise is facing a “mass attack,” with multiple indicators pointing towards a coordinated effort.
- Increased reports of attacks: Security researchers and organizations have reported a significant surge in attacks targeting ConnectWise software.
- Global distribution: The attacks have been reported from various regions across the globe, indicating a widespread campaign.
- Similar attack patterns: The attacks share common characteristics, such as exploiting the same vulnerability and using similar tactics, suggesting a coordinated effort.
Motives Behind the Attacks
The motives behind the attacks can be multifaceted, with potential goals including:
- Data theft: Attackers may aim to steal sensitive data from organizations, including customer information, financial records, and intellectual property.
- Disruption of operations: Attacks can disrupt critical business operations by compromising systems and networks, leading to downtime and financial losses.
- Extortion: Attackers may demand ransom payments in exchange for restoring access to compromised systems or releasing stolen data.
- Espionage: State-sponsored actors may target organizations for intelligence gathering or to gain access to sensitive information.
Targeted Organizations
The attacks have targeted a diverse range of organizations, including:
- Small and medium-sized businesses (SMBs): SMBs often rely on remote access software for managing their operations, making them attractive targets for attackers.
- Healthcare providers: Healthcare organizations handle sensitive patient data, making them a prime target for data theft and extortion.
- Financial institutions: Financial institutions store sensitive financial information, making them a target for both financial gain and espionage.
- Government agencies: Government agencies often handle classified information, making them a target for state-sponsored espionage.
Impact of the Vulnerability on Users
The ConnectWise remote access software vulnerability has significant implications for users, potentially exposing their systems and sensitive data to unauthorized access. This vulnerability allows attackers to exploit weaknesses in the software, granting them control over devices and networks.
Potential Consequences for Affected Users
The consequences of this vulnerability can be severe for affected users. Attackers can gain unauthorized access to sensitive information, including:
- Personal data, such as financial records, medical records, and identity documents.
- Business data, such as customer information, financial statements, and intellectual property.
- Network credentials and access to internal systems.
Attackers can also use this access to:
- Install malware and ransomware, encrypting data and demanding ransom payments.
- Steal data and sell it on the dark web.
- Disrupt business operations by deleting or modifying critical data.
- Launch further attacks against other systems connected to the compromised network.
Mitigation Strategies for Users
Users of ConnectWise remote access software should take immediate steps to mitigate the risk of exploitation. Here are some essential actions:
- Update the software: Install the latest security patches and updates released by ConnectWise to address the vulnerability. This is the most critical step to protect your systems.
- Enable multi-factor authentication: This adds an extra layer of security by requiring users to provide multiple forms of authentication before accessing the software. This makes it significantly harder for attackers to gain unauthorized access.
- Use strong passwords: Ensure you are using strong and unique passwords for all your accounts, including ConnectWise remote access. Avoid using easily guessable passwords or reusing passwords across multiple accounts.
- Limit access to sensitive data: Implement access control measures to restrict access to sensitive information only to authorized personnel. This can help minimize the impact of a successful attack.
- Monitor for suspicious activity: Regularly monitor your systems for any signs of unauthorized access, such as unusual login attempts, changes in system behavior, or data breaches. This can help you detect and respond to attacks quickly.
- Implement a robust security strategy: Develop a comprehensive security strategy that includes regular security assessments, employee training, and incident response plans. This will help you proactively identify and mitigate potential vulnerabilities and respond effectively to security incidents.
ConnectWise’s Response to the Vulnerability: Researchers Say Easy To Exploit Security Bugs In Connectwise Remote Access Software Now Under Mass Attack
ConnectWise, the company behind the Remote Access software, reacted swiftly to the discovery of the vulnerability. They acknowledged the severity of the issue and took immediate steps to mitigate the risk for their users.
ConnectWise’s Actions in Addressing the Vulnerability
ConnectWise’s response to the vulnerability involved several key actions. These actions aimed to minimize the impact of the vulnerability and protect users from potential exploitation.
- Issuing a Security Advisory: ConnectWise promptly released a security advisory that detailed the vulnerability, its potential impact, and recommended steps for users to take. This advisory served as a critical communication tool, alerting users to the risk and providing guidance on how to protect themselves.
- Developing and Deploying Patches: ConnectWise swiftly developed and deployed patches to address the vulnerability. These patches were designed to fix the underlying security flaw, preventing attackers from exploiting it. The availability of these patches was a crucial step in mitigating the risk for users.
- Providing Support to Affected Users: ConnectWise offered support to affected users, helping them to implement the patches and address any related issues. This support included technical assistance, documentation, and guidance on how to secure their systems.
Effectiveness of ConnectWise’s Actions
ConnectWise’s actions were effective in addressing the vulnerability and protecting users. The rapid response and proactive measures taken by the company demonstrated a commitment to security and user safety.
- Prompt Action: ConnectWise’s prompt response to the vulnerability was crucial in minimizing the potential impact. The company’s swift actions in issuing a security advisory and developing patches allowed users to take timely steps to protect themselves.
- Comprehensive Approach: ConnectWise adopted a comprehensive approach to addressing the vulnerability, covering various aspects, including security advisories, patches, and support for affected users. This comprehensive approach ensured that users had access to the necessary information and resources to protect themselves.
- User-Centric Focus: ConnectWise’s response prioritized user safety and provided support to help them implement the necessary security measures. This user-centric focus ensured that users were not left vulnerable and had the resources to protect themselves.
Comparison to Industry Best Practices
ConnectWise’s response to the vulnerability aligns with industry best practices for handling security vulnerabilities. Their actions reflect a commitment to transparency, timely action, and user safety.
- Transparency: ConnectWise’s public disclosure of the vulnerability and its response demonstrated transparency, which is a crucial aspect of responsible security practices.
- Timely Action: The company’s swift development and deployment of patches, as well as their prompt communication with users, highlight their commitment to timely action, which is essential in mitigating security risks.
- User Focus: ConnectWise’s provision of support and guidance to affected users demonstrates a user-centric approach to security, prioritizing user safety and empowering them to protect themselves.
The Importance of Software Security
The recent ConnectWise Remote Access Software vulnerability highlights the critical need for robust software security practices. This attack underscores the potential consequences of insecure software, demonstrating the far-reaching impact on individuals, organizations, and the digital landscape as a whole.
The Need for Regular Security Updates and Patches
Software security updates and patches are essential for mitigating vulnerabilities and protecting against potential attacks. These updates address known security flaws and weaknesses, preventing attackers from exploiting them.
Regularly updating software is like reinforcing the walls of a fortress against potential invaders.
- Improved Security Posture: Updates address known vulnerabilities, strengthening the software’s defenses against attacks.
- Reduced Risk of Exploitation: Timely updates prevent attackers from exploiting known weaknesses before they can be patched.
- Enhanced Resilience: Regular updates help software stay current with the latest security best practices, increasing its resilience against evolving threats.
The Importance of Responsible Software Development Practices
Building security into software from the ground up is crucial for preventing vulnerabilities from emerging in the first place. This involves adopting a security-first approach throughout the development lifecycle.
- Secure Coding Practices: Developers must follow secure coding principles to minimize the introduction of vulnerabilities into the codebase.
- Regular Security Testing: Thorough security testing at all stages of development helps identify and address potential vulnerabilities before release.
- Security Awareness Training: Educating developers about security best practices and common vulnerabilities helps them write more secure code.
Recommendations for Users and Organizations
This vulnerability underscores the critical importance of taking proactive measures to protect your systems and data. Here are some recommendations for users and organizations to enhance their security posture and mitigate the risks associated with this vulnerability.
Recommendations for ConnectWise Users
It’s essential for all users of ConnectWise’s remote access software to take immediate steps to secure their systems. These recommendations are tailored to different user types, addressing their specific needs and concerns.
| User Type | Recommendations |
|---|---|
| Individual |
|
| Small Business |
|
| Enterprise |
|
General Best Practices for Cybersecurity
Regardless of your user type, there are several general best practices you can implement to enhance your cybersecurity posture:
- Stay informed about the latest security threats: Keep up-to-date on the latest security threats and vulnerabilities. Subscribe to security newsletters, follow security experts on social media, and attend industry conferences.
- Use strong passwords and two-factor authentication: This is essential for all your online accounts, not just those related to ConnectWise.
- Back up your data regularly: This will help you recover from a data loss event, such as a ransomware attack.
- Be cautious of suspicious emails and links: Don’t click on links or open attachments from unknown senders.
- Keep your software up to date: Software updates often include security patches that fix vulnerabilities.
The attack on ConnectWise serves as a stark reminder of the importance of software security and the need for proactive measures to protect against cyber threats. Organizations and individuals alike must take steps to secure their systems and stay informed about the latest vulnerabilities. This includes regularly updating software, implementing strong passwords, and being cautious about suspicious emails and links. The responsibility for safeguarding our digital world lies with everyone, and by working together, we can mitigate the risks and build a more secure online environment.
While researchers are busy patching up security holes in ConnectWise’s remote access software, which is currently under a massive attack, Google is taking a bold leap into the future of video creation. Google’s new AI-powered video generation tool, Veo , is set to revolutionize the way we create and consume video content. It’s a stark contrast to the urgent need to address the vulnerabilities in ConnectWise, highlighting the ever-present tension between innovation and security in the digital world.
 Standi Techno News
Standi Techno News