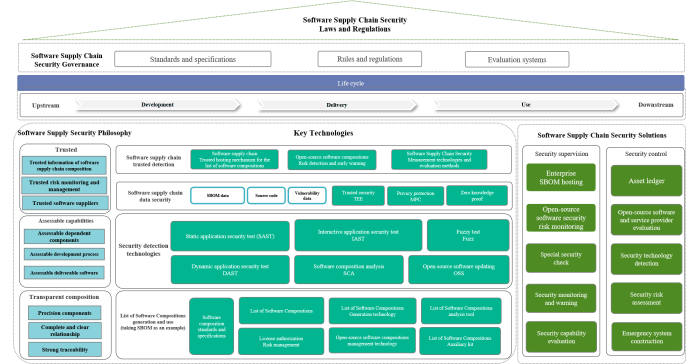
Software supply chain security remains a challenge for most enterprises, a reality underscored by the increasing frequency and sophistication of attacks targeting these critical systems. Imagine a world where a single compromised component within your software can bring your entire operation to a standstill, leaving you vulnerable to data breaches, financial losses, and reputational damage. This isn’t a hypothetical scenario; it’s a growing threat that businesses must actively address.
The modern software landscape is complex, relying on a vast network of interconnected components, dependencies, and third-party suppliers. This interconnectedness, while enabling innovation, also creates vulnerabilities. Attackers exploit these weaknesses, infiltrating the supply chain to introduce malicious code or gain unauthorized access to sensitive information. The consequences can be devastating, impacting not just the targeted organization but also its customers, partners, and the broader ecosystem.
Strategies for Enhancing Software Supply Chain Security: Software Supply Chain Security Remains A Challenge For Most Enterprises
Software supply chain security remains a significant challenge for many enterprises. While some progress has been made, the constant evolution of threats and vulnerabilities demands a proactive and comprehensive approach. This section delves into key strategies to strengthen software supply chain security throughout the development lifecycle.
Best Practices for Robust Security Measures, Software supply chain security remains a challenge for most enterprises
Implementing robust security measures across the software development lifecycle is crucial to mitigate risks. This involves integrating security considerations into each stage, from design and development to deployment and maintenance.
- Secure Development Practices: Employ secure coding practices to minimize vulnerabilities. This includes using secure libraries, validating user inputs, and implementing robust authentication and authorization mechanisms. Regularly conduct code reviews and penetration testing to identify and remediate potential security flaws.
- DevSecOps Integration: Integrate security into the DevOps pipeline. This involves automating security checks, vulnerability scanning, and threat modeling throughout the development process. Continuous monitoring and feedback loops enable early detection and remediation of security issues.
- Secure Configuration Management: Implement secure configuration management practices to ensure that systems and applications are properly configured. This includes using strong passwords, limiting user privileges, and disabling unnecessary services. Regularly review and update configurations to address evolving threats.
Framework for Secure Software Procurement and Dependency Management
Secure software procurement and dependency management are critical aspects of supply chain security. This involves carefully vetting software vendors and managing dependencies to minimize risks.
- Vendor Due Diligence: Conduct thorough due diligence on software vendors before procurement. This includes evaluating their security practices, certifications, and track record. Consider factors such as their security policies, vulnerability disclosure processes, and incident response capabilities.
- Dependency Management: Establish a robust dependency management process to track and manage software dependencies. This involves using tools for dependency analysis, vulnerability scanning, and patch management. Regularly update dependencies to address known vulnerabilities.
- Software Bill of Materials (SBOM): Implement Software Bill of Materials (SBOM) to create a comprehensive inventory of software components. SBOMs provide transparency into the software supply chain, enabling better tracking and management of dependencies.
Vulnerability Scanning and Patching
Regular vulnerability scanning and patching are essential to identify and remediate vulnerabilities in software components. This helps to mitigate risks from known exploits and prevent attackers from gaining access to sensitive information.
- Automated Vulnerability Scanning: Integrate automated vulnerability scanning tools into the development and deployment processes. These tools can identify potential vulnerabilities in code, dependencies, and operating systems. Regular scanning helps to detect vulnerabilities early and facilitate timely remediation.
- Patch Management: Implement a comprehensive patch management process to ensure timely application of security patches. This involves regularly checking for available patches, testing them in controlled environments, and deploying them promptly to production systems.
- Threat Intelligence: Leverage threat intelligence to stay informed about emerging threats and vulnerabilities. This includes subscribing to security advisories, threat feeds, and vulnerability databases. This information can help prioritize patching efforts and enhance security awareness.
The Role of Automation and Artificial Intelligence in Supply Chain Security
In today’s digital landscape, software supply chain security is a paramount concern. As the complexity of software development and deployment continues to increase, enterprises need to adopt advanced strategies to safeguard their supply chains from malicious actors. Automation and artificial intelligence (AI) play a crucial role in bolstering these defenses, offering powerful tools to enhance visibility, detect threats, and respond effectively.
Streamlining Security Processes with Automation
Automation can significantly enhance the efficiency and effectiveness of security processes, reducing manual efforts and freeing up security teams to focus on more strategic tasks. By automating repetitive tasks, organizations can achieve greater speed, accuracy, and consistency in their security operations.
- Vulnerability Scanning and Patching: Automating vulnerability scanning and patching processes can help organizations quickly identify and remediate vulnerabilities across their software supply chains. This includes regularly scanning for known vulnerabilities in open-source libraries, third-party components, and internal codebases, and automatically deploying patches when available.
- Software Composition Analysis (SCA): SCA tools can be automated to analyze software bills of materials (SBOMs) and identify potential vulnerabilities or security risks associated with third-party components. This enables organizations to track dependencies, assess risk levels, and proactively mitigate vulnerabilities before they are exploited.
- Security Policy Enforcement: Automation can help enforce security policies across the software development lifecycle, ensuring compliance with best practices and industry standards. This can include automatically verifying code quality, enforcing code signing, and implementing secure coding practices.
Real-Time Threat Detection and Response with AI
AI and machine learning (ML) algorithms are capable of analyzing vast amounts of data in real-time, identifying patterns and anomalies that might indicate malicious activity. This empowers organizations to detect threats proactively, respond quickly, and minimize the impact of attacks.
- Anomaly Detection: AI algorithms can analyze network traffic, user behavior, and code changes to identify unusual patterns that might indicate malicious activity. This can help detect attacks such as code injection, data exfiltration, and unauthorized access attempts.
- Threat Intelligence Gathering: AI can be used to collect and analyze threat intelligence from various sources, including open-source data, security forums, and industry reports. This information can be used to identify emerging threats, predict attack vectors, and develop proactive security measures.
- Real-Time Response: AI-powered security systems can automatically respond to detected threats in real-time, minimizing the impact of attacks. This includes actions such as isolating compromised systems, blocking malicious traffic, and alerting security teams.
AI for Threat Intelligence Gathering and Risk Assessment
AI can be a valuable tool for gathering and analyzing threat intelligence, providing insights into emerging threats, attack trends, and potential vulnerabilities.
- Threat Landscape Analysis: AI can analyze vast amounts of data from various sources to identify emerging threats and attack patterns. This can help organizations stay ahead of attackers by understanding the latest threats and vulnerabilities.
- Risk Assessment: AI can be used to assess the risk associated with specific software components, third-party vendors, and development practices. This can help organizations prioritize security efforts and allocate resources effectively.
- Vulnerability Prediction: AI can be used to predict potential vulnerabilities in software based on historical data and code analysis. This can help organizations identify and address vulnerabilities before they are exploited.
The Future of Software Supply Chain Security
The software supply chain is constantly evolving, with new technologies and attack vectors emerging all the time. To stay ahead of the curve, organizations need to adopt a proactive approach to security, embracing emerging trends and technologies that can help them build more resilient supply chains.
The Impact of Blockchain and Distributed Ledger Technology
Blockchain and distributed ledger technology (DLT) have the potential to revolutionize software supply chain security. These technologies can be used to create immutable records of software components, making it much harder for attackers to tamper with or forge them. This increased transparency and accountability can help to build trust in the supply chain and reduce the risk of malicious actors introducing vulnerabilities into the software development process.
- Increased Transparency and Traceability: Blockchain can create a transparent and auditable record of all software components, from source code to deployment. This makes it possible to track the origin and history of every component, making it much harder for attackers to introduce malicious code.
- Enhanced Trust and Security: By providing a secure and tamper-proof record of software components, blockchain can help to build trust between developers, vendors, and users. This can reduce the risk of counterfeit software and ensure that only legitimate components are used in the software development process.
- Automated Verification and Validation: Blockchain can be used to automate the verification and validation of software components, ensuring that they meet security standards and requirements. This can help to reduce the risk of vulnerabilities being introduced into the software development process.
The Role of Collaboration and Information Sharing
Collaboration and information sharing are essential for strengthening software supply chain defenses. By sharing threat intelligence and best practices, organizations can collectively improve their security posture and protect themselves from emerging threats.
- Threat Intelligence Sharing: Organizations can share information about known vulnerabilities, attack vectors, and malicious actors. This can help to raise awareness about emerging threats and enable organizations to take proactive steps to mitigate their risks.
- Best Practice Sharing: Organizations can share best practices for securing the software supply chain. This can include information about secure coding practices, vulnerability management, and incident response.
- Joint Security Initiatives: Organizations can work together to develop joint security initiatives, such as industry-wide standards for secure software development or vulnerability disclosure programs.
Navigating the complex landscape of software supply chain security requires a multifaceted approach. It demands a commitment to robust security practices throughout the software development lifecycle, including secure procurement, dependency management, vulnerability scanning, and continuous monitoring. Leveraging automation and artificial intelligence can significantly enhance these efforts, enabling organizations to detect and respond to threats in real-time. By embracing a culture of security awareness, collaboration, and information sharing, businesses can strengthen their defenses against evolving threats and ensure the integrity of their software supply chains.
Securing the software supply chain is a constant battle for most enterprises, but it’s not the only challenge they face. Companies are also grappling with the need to reduce their carbon footprint, and the nzero grid carbon intensity tool can help them track and optimize their energy usage. While these two issues might seem unrelated, they both point to the need for organizations to be proactive and innovative in addressing the challenges of the modern world.
 Standi Techno News
Standi Techno News