The Data Breach and its Impact
The Target data breach, which occurred in late 2013, remains one of the most significant retail data breaches in history. Hackers gained access to Target’s payment processing systems, compromising sensitive information belonging to millions of customers. The breach exposed a wide range of personal data, including credit and debit card numbers, expiration dates, and security codes.
This breach had far-reaching consequences for affected individuals. Many customers experienced financial losses due to fraudulent charges made on their compromised cards. Identity theft became a significant concern, as stolen data could be used to create fake identities and access other sensitive accounts. The emotional distress caused by the breach, including feelings of violation and anxiety, should not be underestimated.
Potential Consequences for Affected Individuals
The Target data breach serves as a stark reminder of the potential consequences of data breaches for individuals. While the specific impact can vary depending on the individual’s circumstances, the following consequences are common:
- Financial Loss: Stolen credit card numbers can be used for fraudulent purchases, leading to financial loss for affected individuals. In some cases, individuals may need to dispute charges and deal with the hassle of obtaining new cards.
- Identity Theft: The stolen data can be used to create fake identities, which can be used for various fraudulent activities, including opening new credit accounts, obtaining loans, and committing other crimes. This can have a long-term impact on an individual’s credit score and financial standing.
- Emotional Distress: Data breaches can cause significant emotional distress, including feelings of violation, anxiety, and fear. The knowledge that personal information has been compromised can lead to sleepless nights, difficulty concentrating, and a sense of vulnerability.
Real-World Cases of Data Breach Damages, Target could pay data breach victims up to 10000 in damages
Numerous real-world cases demonstrate the significant damages that can result from data breaches. For instance, the Equifax breach in 2017 exposed the personal information of over 147 million individuals, leading to widespread identity theft and financial losses. The breach resulted in a massive settlement, with Equifax paying billions of dollars to affected individuals and government agencies.
“The Equifax breach was a wake-up call for businesses and individuals alike. It highlighted the importance of data security and the devastating consequences of failing to protect sensitive information.” – Cybersecurity Expert
Another notable case is the 2014 Sony Pictures Entertainment hack, which exposed sensitive information, including emails, financial data, and personal details of employees and actors. The breach caused significant financial losses for Sony, disrupted its operations, and led to reputational damage.
These cases illustrate the significant impact that data breaches can have on individuals, businesses, and society as a whole. It is essential for organizations to prioritize data security and implement robust measures to protect sensitive information.
Legal Framework for Data Breach Compensation
Data breaches are becoming increasingly common, resulting in significant financial and reputational harm to individuals and organizations. When a data breach occurs, victims may have legal recourse to seek compensation for their losses. This section delves into the legal framework governing data breach compensation, examining relevant laws, regulations, and legal arguments that support victims’ claims.
Legal Basis for Data Breach Compensation
Data breach compensation claims are typically grounded in various legal theories, including negligence, breach of contract, and statutory violations. The legal arguments supporting these claims depend on the specific circumstances of the breach and the applicable laws in the jurisdiction where the breach occurred.
Negligence
Negligence is a common legal theory used in data breach lawsuits. To establish negligence, victims must demonstrate that:
- The data controller owed them a duty of care.
- The data controller breached that duty of care by failing to implement reasonable security measures to protect their data.
- The breach caused them harm.
- The harm was foreseeable.
For instance, a company that fails to encrypt sensitive customer data, resulting in a data breach, could be found negligent if it can be proven that encryption was a reasonable security measure and that the breach was foreseeable.
Breach of Contract
Data breach victims may also have claims based on breach of contract if the data controller violated a contractual obligation to protect their data. For example, a company’s privacy policy or terms of service may contain provisions regarding data security. If the company breaches these provisions, victims may have a claim for breach of contract.
Statutory Violations
Several statutes, such as the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR), provide specific legal grounds for data breach compensation. These statutes impose data protection obligations on companies and may authorize victims to seek damages for violations.
Legal Precedent
Several landmark cases have established legal precedent for data breach compensation. For example, the 2013 case of *Spokeo, Inc. v. Robins* established that even if a data breach does not result in demonstrable financial harm, victims may still have standing to sue for statutory damages under the Fair Credit Reporting Act.
Examples of Legal Precedent
- Equifax Data Breach: In the Equifax data breach of 2017, millions of individuals had their personal information compromised. Class-action lawsuits were filed against Equifax, alleging negligence, breach of contract, and statutory violations. The settlement of these lawsuits resulted in significant compensation for affected individuals.
- Target Data Breach: The 2013 Target data breach compromised the credit card information of millions of customers. The company faced numerous lawsuits, including class-action lawsuits, alleging negligence and breach of contract. The settlement of these lawsuits resulted in significant financial compensation for affected customers.
Target’s Response and Settlement Offer: Target Could Pay Data Breach Victims Up To 10000 In Damages
Target’s response to the data breach was swift and comprehensive, aiming to mitigate the damage and restore customer trust. The company took immediate steps to contain the breach, notify affected customers, and offer credit monitoring services.
Target’s settlement offer, however, was a significant development in the aftermath of the breach. The offer of up to $10,000 per victim was a direct result of the widespread impact of the data breach and the resulting legal actions. This offer reflects the magnitude of the breach, the potential for financial harm to victims, and the legal precedent set by similar cases.
Factors Influencing the Settlement Offer
The settlement offer was influenced by several key factors:
- Magnitude of the Data Breach: The breach affected millions of customers, exposing sensitive personal information such as credit card details, addresses, and purchase history. This large-scale impact played a significant role in determining the settlement amount.
- Financial Harm to Victims: The stolen data could be used for identity theft, fraudulent purchases, and other financial crimes. The potential for significant financial harm to victims was a major concern for Target and contributed to the settlement offer.
- Legal Precedents: Previous data breach settlements, such as those involving companies like Equifax and Yahoo, set a precedent for substantial compensation to victims. Target’s legal team likely considered these precedents in determining the settlement amount.
- Public Pressure and Media Scrutiny: The data breach received extensive media coverage and public scrutiny, putting significant pressure on Target to address the issue and compensate victims. This pressure likely contributed to the settlement offer.
Benefits and Drawbacks of Accepting the Settlement Offer
The decision to accept or reject the settlement offer is a personal one for each victim. Here are some potential benefits and drawbacks to consider:
- Benefits:
- Financial Compensation: The settlement offer provides financial compensation for potential financial losses and the inconvenience caused by the data breach.
- Resolution and Closure: Accepting the settlement can provide closure for victims, allowing them to move on from the breach without the uncertainty and potential costs of a protracted legal battle.
- Time and Cost Savings: Pursuing individual lawsuits can be time-consuming and expensive. The settlement offer allows victims to avoid these costs and potential delays.
- Drawbacks:
- Limited Compensation: The settlement amount may not fully compensate victims for all their losses, especially those who have experienced significant financial harm or identity theft.
- Waiver of Future Claims: Accepting the settlement typically involves waiving the right to pursue future claims against Target related to the data breach. This could prevent victims from seeking additional compensation if they experience further losses.
- Potential for Higher Individual Settlements: Some victims may believe they could obtain a larger settlement by pursuing individual lawsuits, although this is not guaranteed.
Considerations for Victims
The Target data breach settlement offers a chance for affected individuals to receive compensation for the inconvenience and potential harm caused by the breach. However, deciding whether to accept the settlement offer requires careful consideration of several factors.
Evaluating the Settlement Offer
Before deciding whether to accept the settlement offer, victims should carefully evaluate the potential compensation amount against the inconvenience and potential risks associated with the breach.
- The Amount of Compensation: The settlement offers a maximum of $10,000 per victim, but the actual amount received will depend on the specific circumstances of each case. Victims should consider the costs they incurred due to the breach, such as credit monitoring, identity theft protection, and lost time.
- The Inconvenience and Potential Risks: The data breach could have resulted in identity theft, fraudulent charges, and other financial losses. Victims should consider the potential risks associated with the breach and the inconvenience of dealing with the aftermath.
- The Legal Process: Accepting the settlement offer means giving up the right to sue Target for damages. Victims should weigh the potential benefits of the settlement against the possibility of a larger payout through a lawsuit.
Filing a Claim
To file a claim, victims must complete a claim form and submit it to the settlement administrator. The claim form will require information about the victim’s identity, the nature of their losses, and any supporting documentation.
- Required Documentation: Victims should gather all relevant documentation to support their claim, such as credit reports, bank statements, police reports, and identity theft protection invoices.
- Claim Filing Deadline: Victims must file their claim by the deadline specified in the settlement agreement. Missing the deadline could result in the loss of their claim.
Data Security Implications
The Target data breach, which exposed the personal information of millions of customers, serves as a stark reminder of the importance of robust data security measures. It highlights the vulnerabilities that can exist within even large and seemingly secure organizations, and the devastating consequences that can result from a breach.
Security Vulnerabilities
The Target data breach was attributed to a combination of factors, including:
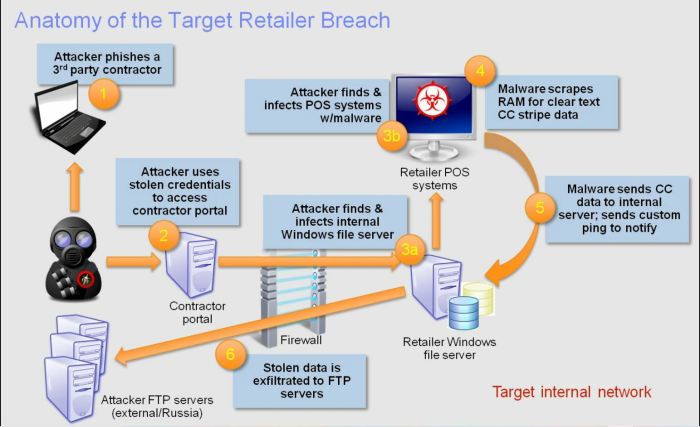
- Compromised Credentials: Hackers gained access to Target’s systems by exploiting stolen credentials from a third-party vendor. This highlights the importance of securing access to sensitive information and ensuring the security of third-party vendors.
- Weak Network Security: The attackers were able to move laterally within Target’s network, exploiting vulnerabilities in network security controls. This emphasizes the need for comprehensive network segmentation and robust security measures to prevent unauthorized access.
- Insufficient Endpoint Security: The attackers were able to install malware on Target’s point-of-sale (POS) systems, which allowed them to steal customer data. This underscores the importance of implementing strong endpoint security measures, such as antivirus software and intrusion detection systems.
Importance of Robust Data Security Measures
The Target data breach serves as a cautionary tale, demonstrating the critical need for organizations to prioritize data security. Robust data security measures are essential for protecting sensitive information and mitigating the risks of data breaches. These measures should include:
- Strong Password Policies: Enforce strong password requirements, such as length, complexity, and regular rotation, to make it difficult for attackers to guess or crack passwords.
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security by requiring users to provide multiple forms of identification, such as a password and a one-time code, before granting access to sensitive systems.
- Regular Security Audits: Conduct regular security audits to identify and address vulnerabilities in systems and networks. These audits should include penetration testing to simulate real-world attacks and assess the effectiveness of security controls.
- Data Encryption: Encrypt sensitive data both in transit and at rest to prevent unauthorized access even if systems are compromised. This ensures that data remains unreadable to attackers.
- Employee Training: Train employees on data security best practices, such as phishing awareness, secure password management, and incident reporting procedures. This helps to minimize the risk of human error and accidental data leaks.
- Incident Response Plan: Develop and test a comprehensive incident response plan to quickly and effectively handle data breaches. This plan should include steps for containing the breach, mitigating damage, and notifying affected individuals.
Best Practices for Protecting Sensitive Information
Protecting sensitive information requires a multi-faceted approach that encompasses various best practices, including:
- Data Minimization: Only collect and store the data that is absolutely necessary for business operations. This reduces the amount of sensitive information that could be compromised in a breach.
- Access Control: Implement strict access control measures to limit access to sensitive data to authorized individuals. This ensures that only those who need access to the data can view or modify it.
- Regular Security Updates: Keep all software and operating systems up to date with the latest security patches to address known vulnerabilities. This is essential for protecting against zero-day exploits and other emerging threats.
- Data Backup and Recovery: Regularly back up sensitive data and test the recovery process to ensure that data can be restored quickly and efficiently in the event of a breach or system failure.
Impact on Consumer Trust
The Target data breach, exposing millions of customers’ personal information, had a significant impact on consumer trust, not only in Target but also in other retailers. The incident raised concerns about the security of personal data and the ability of companies to protect it, leading to a decline in customer confidence and loyalty.
Transparency and Communication
Transparency and communication played a crucial role in restoring consumer trust after the data breach. Target’s initial response was widely criticized for its lack of transparency and timely communication. However, the company later improved its communication strategy by providing regular updates, offering credit monitoring services, and apologizing to affected customers. This proactive approach helped to rebuild trust and demonstrate the company’s commitment to customer safety.
“Target’s communication was initially criticized for its lack of transparency and timely communication. However, the company later improved its communication strategy by providing regular updates, offering credit monitoring services, and apologizing to affected customers.”
Long-Term Implications for Target’s Brand Reputation and Customer Loyalty
The data breach had long-term implications for Target’s brand reputation and customer loyalty. While the company has taken steps to improve its security measures and regain customer trust, the incident remains a significant event in its history. Some customers may have permanently lost trust in Target, while others may be more cautious about sharing their personal information with the company.
“The data breach had long-term implications for Target’s brand reputation and customer loyalty. While the company has taken steps to improve its security measures and regain customer trust, the incident remains a significant event in its history.”
Target could pay data breach victims up to 10000 in damages – The Target data breach serves as a stark reminder of the vulnerabilities inherent in our digital age and the importance of protecting personal information. It also underscores the crucial role that businesses play in safeguarding consumer data and the need for strong legal frameworks to hold them accountable for data breaches. As we navigate an increasingly interconnected world, the story of Target’s data breach continues to resonate, urging us to be vigilant about our online security and to demand greater transparency and accountability from those who handle our personal information.
Target’s potential payout of up to $10,000 to data breach victims might seem hefty, but some folks are taking a different approach to compensation. A developer recently tracked down pirates who downloaded his game illegally and instead of sending them a cease and desist, he wrote them a heartfelt thank you note. This heartwarming gesture, shared in a viral post , highlights the contrasting approaches to dealing with unauthorized access.
While Target aims to financially address the damage, this developer chose to foster understanding and appreciation.
 Standi Techno News
Standi Techno News