Two-Factor Authentication (2FA) on Twitter
In today’s digital world, securing your online accounts is paramount, especially on platforms like Twitter where you share your thoughts, opinions, and potentially sensitive information. Two-Factor Authentication (2FA) acts as an extra layer of security, making it much harder for unauthorized individuals to access your account.
The Importance of 2FA for Twitter Accounts
Two-Factor Authentication (2FA) is an essential security measure for all Twitter users. It adds an extra layer of protection to your account, making it significantly harder for hackers and malicious actors to gain unauthorized access. Even if someone manages to obtain your password, they’ll still need access to your 2FA code to log in. This significantly reduces the risk of account takeover and protects your personal information.
App-Based 2FA: A Superior Security Measure
App-based 2FA is a more secure option compared to SMS-based 2FA. While SMS-based 2FA sends a code to your phone via text message, it’s susceptible to SIM swapping attacks, where hackers can gain control of your phone number and intercept the 2FA code. App-based 2FA, on the other hand, utilizes authenticator apps like Google Authenticator or Authy, which generate time-based codes that are independent of your phone number. This makes it much more difficult for hackers to bypass 2FA and gain access to your account.
Setting Up App-Based 2FA on Twitter
Here’s a step-by-step guide on how to set up app-based 2FA on Twitter:
- Download and install an authenticator app: Choose a reputable authenticator app from the app store. Some popular options include Google Authenticator, Authy, and Microsoft Authenticator.
- Open your Twitter settings: Go to your profile and click on the “More” option, followed by “Settings and privacy.”
- Navigate to the “Security and Account access” section: Under “Security,” you’ll find the “Two-factor authentication” option. Click on it.
- Select “Set up app-based authentication”: This will prompt you to scan a QR code using your authenticator app.
- Scan the QR code with your authenticator app: The authenticator app will automatically add your Twitter account and generate a six-digit code.
- Enter the six-digit code on Twitter: Type the code generated by your authenticator app into the designated field on Twitter.
- Save your backup codes: Twitter will provide you with a set of backup codes. These codes are essential in case you lose access to your authenticator app or device. Store them securely in a safe place, separate from your phone.
Benefits of Authenticator Apps for 2FA
- Enhanced Security: Authenticator apps provide a more secure form of 2FA, as they are not reliant on phone numbers, making them less vulnerable to SIM swapping attacks.
- Improved Privacy: Authenticator apps don’t require sharing your phone number with third-party services, enhancing your privacy.
- Convenience: Authenticator apps are user-friendly and provide a quick and easy way to generate 2FA codes.
- Cross-Platform Compatibility: Most authenticator apps are available on both Android and iOS devices, making them accessible across multiple platforms.
Popular Authenticator Apps for Twitter
Two-factor authentication (2FA) is an essential security measure for any online account, and Twitter is no exception. 2FA adds an extra layer of protection to your account, making it much harder for unauthorized individuals to access it. While Twitter’s built-in SMS-based 2FA is convenient, using an authenticator app is generally considered more secure.
Popular Authenticator Apps
Authenticator apps generate time-based one-time passwords (TOTPs) that are used to verify your identity when logging into Twitter. These apps are designed to be more secure than SMS-based 2FA because they don’t rely on potentially vulnerable phone networks.
Here are some of the most popular authenticator apps compatible with Twitter:
- Google Authenticator: Developed by Google, it’s a widely trusted and user-friendly app. It’s available for both Android and iOS devices.
- Microsoft Authenticator: Developed by Microsoft, it offers a similar experience to Google Authenticator. It’s also available for both Android and iOS devices.
- Authy: A cross-platform app that allows you to back up your 2FA codes. This is useful if you lose your phone or switch devices.
- Authenticator: A simple and straightforward app developed by 1Password. It’s known for its clean interface and easy-to-use features.
- Duo Mobile: Developed by Duo Security, it offers a wide range of features, including support for multiple accounts and push notifications.
Comparing Authenticator Apps
| Feature | Google Authenticator | Microsoft Authenticator | Authy | Authenticator (1Password) | Duo Mobile |
|---|---|---|---|---|---|
| Security | Highly secure, backed by Google’s infrastructure | Highly secure, backed by Microsoft’s infrastructure | Highly secure, with backup options | Highly secure, integrated with 1Password’s security features | Highly secure, with advanced features like push notifications |
| User Interface | Simple and straightforward | Simple and straightforward | Clean and intuitive | Minimalistic and easy to navigate | Feature-rich and slightly more complex |
| Compatibility | Android, iOS | Android, iOS | Android, iOS, Windows, macOS | Android, iOS | Android, iOS, Windows, macOS |
Security Implications of App-Based 2FA
While app-based two-factor authentication (2FA) significantly enhances your Twitter account’s security, it’s crucial to understand the potential risks and take appropriate precautions. App-based 2FA, while generally considered more secure than SMS-based 2FA, is not foolproof and can be susceptible to vulnerabilities.
Vulnerabilities and Potential Exploits, Twitter supports app based two factor authentication
The security of app-based 2FA hinges on the integrity of the authenticator app and the device it’s installed on. A compromised app or device can potentially expose your 2FA codes, leaving your account vulnerable.
- Malware Infections: Malicious software can steal your 2FA codes from the authenticator app. It can either target the app directly or intercept the communication between the app and the device.
- Phishing Attacks: Phishing attacks can trick you into installing malicious apps or revealing your 2FA codes. These attacks often use convincing email or SMS messages that appear to be from legitimate sources.
- App Vulnerabilities: Authenticator apps themselves can have security vulnerabilities that attackers can exploit. These vulnerabilities could allow attackers to bypass 2FA protection or steal your codes.
- Device Compromise: If your device is compromised, an attacker could gain access to your authenticator app and steal your 2FA codes. This can happen through malware, physical access, or remote access vulnerabilities.
Choosing a Secure and Reputable Authenticator App
Selecting a trustworthy and secure authenticator app is essential for safeguarding your 2FA codes. Look for apps that meet the following criteria:
- Open-Source Code: Apps with open-source code allow independent security researchers to audit the code for vulnerabilities. This transparency increases trust and helps ensure the app’s security.
- Strong Security Features: Choose apps that offer robust security features such as encryption, two-factor authentication for the app itself, and regular security updates.
- Positive User Reviews: Check user reviews and ratings to get an idea of the app’s reputation and security track record. Look for apps with consistent positive reviews and a low number of negative reviews.
- Developed by Reputable Companies: Apps developed by established and reputable companies tend to have a higher level of security and reliability. Look for apps from companies with a proven track record in cybersecurity.
Securing Authenticator Apps and Protecting Generated Codes
Protecting your authenticator app and the codes it generates is crucial for maintaining the integrity of your 2FA. Follow these best practices:
- Keep Apps Updated: Regularly update your authenticator app to benefit from the latest security patches and bug fixes. These updates can help address vulnerabilities and improve the app’s overall security.
- Use a Strong Password: If your authenticator app requires a password, choose a strong and unique password. Avoid using the same password for multiple accounts.
- Enable App Lock: Consider enabling an app lock feature if available. This adds an extra layer of protection by requiring a password or fingerprint scan to access the app.
- Backup Your Codes: Create a backup of your 2FA codes in case you lose access to your device or need to reinstall the app. Store the backup securely, ideally in a physical location separate from your device.
- Avoid Sharing Codes: Never share your 2FA codes with anyone, including friends, family, or even Twitter support. Twitter will never ask for your 2FA codes.
- Use a Separate Device: If possible, use a separate device for your authenticator app. This reduces the risk of compromising your primary device and exposing your 2FA codes.
Alternatives to App-Based 2FA: Twitter Supports App Based Two Factor Authentication
While app-based 2FA is widely used, it’s not the only option available for securing your Twitter account. Twitter offers alternative methods, each with its own strengths and weaknesses.
Twitter supports app based two factor authentication – Exploring these alternatives is crucial for finding the 2FA method that best suits your security needs, comfort level, and technological resources. Some users may prefer the convenience of app-based 2FA, while others might find security keys or email verification more appealing. Let’s dive into these alternatives and see how they compare to app-based 2FA.
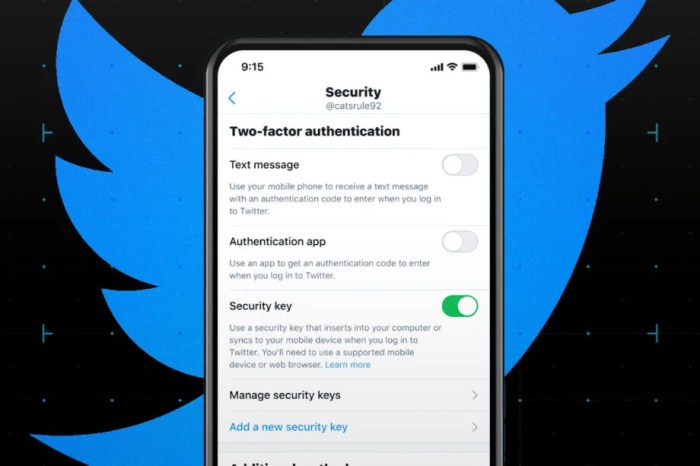
Security Keys
Security keys are physical devices that plug into your computer’s USB port or connect wirelessly via Bluetooth or NFC. When you log in to Twitter, the security key generates a unique code that you need to enter to complete the authentication process.
Security keys are considered the most secure form of 2FA because they are physically protected and don’t rely on software that could be compromised. They are also more resistant to phishing attacks, as they are not susceptible to malicious websites mimicking the real Twitter login page. However, security keys can be more expensive than app-based 2FA and require a physical device to be carried around.
Email-Based Verification
Email-based verification is a simpler alternative to app-based 2FA. When you log in to Twitter, you receive a verification code via email. This code needs to be entered to complete the authentication process.
Email-based verification is convenient because it doesn’t require any additional apps or hardware. However, it’s less secure than app-based 2FA or security keys. Email accounts are susceptible to phishing attacks and data breaches, which could compromise your Twitter account. If your email account is compromised, attackers could potentially gain access to your Twitter account by intercepting the verification code.
The Future of 2FA on Twitter
Twitter’s commitment to user security is evident in its embrace of Two-Factor Authentication (2FA). As technology evolves, so too will the ways in which we safeguard our online accounts. Looking ahead, Twitter’s 2FA system is poised for significant advancements that will further enhance user security and address emerging threats.
Advancements in 2FA Technology
The landscape of authentication technology is constantly evolving, and Twitter is well-positioned to leverage these advancements to bolster its 2FA system.
- Biometric Authentication: Imagine logging into your Twitter account with a simple fingerprint scan or facial recognition. Biometric authentication is becoming increasingly prevalent, offering a more secure and user-friendly alternative to traditional passwords and codes. Twitter could integrate these technologies into its 2FA system, making account access even more robust.
- FIDO2: The Fast Identity Online (FIDO) Alliance is promoting a new standard for passwordless authentication. FIDO2 leverages cryptographic keys stored on devices, eliminating the need for passwords and providing a more secure and convenient login experience. Twitter could adopt FIDO2, making it easier for users to access their accounts while enhancing security.
- Security Keys: Hardware security keys, like YubiKeys, are physical devices that plug into a computer’s USB port and provide an extra layer of security. When used with 2FA, they offer a highly secure and tamper-proof method of authentication. Twitter could encourage the use of security keys, making account access more secure for those who require an extra layer of protection.
In a world where online security is paramount, Twitter’s embrace of app-based 2FA is a welcome move. It’s a clear indication that they’re committed to providing a safe and secure platform for their users. So, ditch the text messages, download an authenticator app, and enjoy the peace of mind that comes with knowing your Twitter account is protected from the digital bad guys. After all, in the world of social media, security is the ultimate flex.
Twitter’s new app-based two-factor authentication is a welcome move, adding an extra layer of security to your account. It’s interesting to see how this aligns with Google’s upcoming change to its mobile search algorithm, which is set to take effect tomorrow. While these changes are in different areas, they both highlight a focus on user security and experience.
 Standi Techno News
Standi Techno News