The Wannacry Attack
The WannaCry ransomware attack, which began on May 12, 2017, was a global cyberattack that affected hundreds of thousands of computers in over 150 countries. It was a significant event that highlighted the vulnerabilities of computer systems and the potential impact of ransomware attacks.
The Nature of the Wannacry Attack
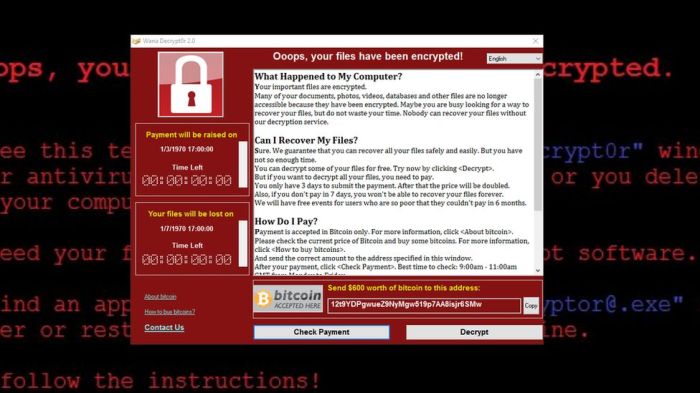
The Wannacry attack exploited a vulnerability in Microsoft’s Windows operating system, specifically a flaw in the Server Message Block (SMB) protocol. This vulnerability allowed attackers to remotely access and control vulnerable computers without requiring user interaction. The attack was carried out using a ransomware program that encrypted files on infected computers, rendering them inaccessible until a ransom was paid.
The Impact of the Attack
The WannaCry attack had a significant impact on individuals, businesses, and governments worldwide.
- Individuals lost access to their personal files, including photos, documents, and financial records.
- Businesses experienced disruptions to their operations, leading to lost productivity and revenue.
- Governments faced challenges in providing essential services, such as healthcare and transportation.
The attack also highlighted the need for better cybersecurity practices and the importance of patching vulnerabilities promptly.
The Ransomware Used in the Attack
The ransomware used in the WannaCry attack, known as WannaCry, encrypted files on infected computers using the AES-128 encryption algorithm. Once encrypted, the files were inaccessible unless a ransom was paid in Bitcoin. The ransom demand varied depending on the time of infection, but it was typically around $300.
Attribution and Evidence: Wannacry Attack Source Publicly Named North Korea
The Wannacry attack, which crippled computers across the globe in 2017, remains a significant cybersecurity event. While the perpetrators initially remained anonymous, investigations pointed towards a North Korean connection. This attribution wasn’t just based on speculation; it was backed by substantial evidence and technical analysis of the malware itself.
The investigation into the origins of Wannacry led to a specific group of hackers: the Lazarus Group. This group, widely believed to be a North Korean cybercrime organization, has been linked to various high-profile cyberattacks, including the Sony Pictures hack and the Bangladesh Bank heist.
The Lazarus Group
The Lazarus Group is a sophisticated and well-resourced cybercrime group, known for its advanced hacking capabilities and its alleged ties to the North Korean government. While the group’s activities have been documented since 2009, its link to North Korea was solidified after the WannaCry attack.
- Extensive Cybercrime History: The group’s history includes a range of attacks, targeting financial institutions, government agencies, and even entertainment companies. They are known for their use of custom-built malware and their ability to evade detection.
- Sophisticated Techniques: The Lazarus Group is renowned for its sophisticated hacking techniques, including spear phishing, zero-day exploits, and advanced malware development. They often target high-value assets, such as financial data and confidential information.
- Political Motivation: Many believe the Lazarus Group’s attacks are driven by political motives. Their targets often align with North Korea’s geopolitical interests, and their actions have been linked to the country’s foreign policy agenda.
Technical Analysis of Wannacry
The Wannacry ransomware, at its core, was a sophisticated piece of malware designed to encrypt files on infected computers and demand a ransom for their decryption. Its technical analysis revealed crucial clues that pointed towards the Lazarus Group and, by extension, North Korea.
- Code Similarities: The code used in Wannacry shared significant similarities with other malware known to have been developed by the Lazarus Group. This code similarity, while not conclusive on its own, provided a strong indication of a shared origin.
- Command and Control Infrastructure: The malware used a command and control (C&C) infrastructure that had been previously linked to the Lazarus Group. This infrastructure allowed the attackers to communicate with infected computers and control their actions.
- Exploitation of a Known Vulnerability: Wannacry exploited a vulnerability in the Windows operating system, known as EternalBlue. This vulnerability, later confirmed to have been developed by the National Security Agency (NSA), was leaked online and used by the Lazarus Group to spread the ransomware.
“The Lazarus Group is a highly skilled and persistent cybercrime group with a history of targeting high-value assets. The technical analysis of Wannacry, combined with the group’s known activities, provides strong evidence linking them to the attack.” – Cybersecurity Expert
North Korea’s Cyberwarfare Capabilities
North Korea’s cyberwarfare capabilities have gained significant attention in recent years, particularly after the WannaCry ransomware attack in 2017, which was attributed to the country. While North Korea has denied involvement in the attack, the evidence suggests a sophisticated and well-resourced cyberwarfare program.
History of Cyberattacks
North Korea has a history of engaging in cyberattacks, often targeting South Korea, the United States, and other countries. These attacks have ranged from propaganda campaigns and website defacements to large-scale data breaches and disruptive attacks on critical infrastructure.
- 2014 Sony Pictures Hack: This high-profile attack targeted Sony Pictures Entertainment, resulting in the release of confidential data and the cancellation of the film “The Interview,” which depicted the assassination of North Korean leader Kim Jong-un. The attack was widely attributed to North Korea, although the country never officially claimed responsibility.
- 2017 WannaCry Ransomware Attack: The WannaCry ransomware attack, which affected computers in over 150 countries, was attributed to a North Korean hacking group known as Lazarus Group. The attack exploited a vulnerability in Microsoft Windows, encrypting data on infected computers and demanding a ransom for its decryption.
- 2017 NotPetya Ransomware Attack: While not directly attributed to North Korea, some experts believe that the NotPetya attack, which caused billions of dollars in damage, was likely carried out by a group with ties to the country. The attack used similar tactics to WannaCry, but with more sophisticated malware and a wider impact.
International Response and Countermeasures
The Wannacry attack triggered a global response, encompassing investigations, sanctions, and collaborative efforts to mitigate the impact and prevent future attacks. Governments, cybersecurity firms, and international organizations worked together to understand the attack, attribute it to its perpetrators, and develop countermeasures.
International Investigations and Sanctions
The international community swiftly launched investigations to determine the origin and extent of the Wannacry attack. The United Kingdom’s National Crime Agency (NCA) and the US Department of Homeland Security (DHS) led the investigations, collaborating with other countries to gather intelligence and identify the attackers. The investigations focused on tracing the attack’s origin, analyzing the malware, and identifying the individuals or groups responsible.
Following the investigations, several countries imposed sanctions on North Korea for its alleged role in the Wannacry attack. The United States, the European Union, and South Korea imposed sanctions on individuals and entities associated with North Korea’s cyberwarfare activities. These sanctions aimed to deter future attacks and pressure North Korea to abandon its malicious cyber activities.
Cybersecurity Response and Mitigation Efforts
Governments and cybersecurity firms worldwide implemented measures to mitigate the impact of the Wannacry attack and prevent similar attacks in the future.
- Governments issued cybersecurity advisories and guidelines, urging organizations to patch vulnerabilities and strengthen their defenses.
- Cybersecurity firms developed and released security patches and tools to detect and remove the Wannacry malware from infected systems.
- International organizations like the United Nations and Interpol collaborated to share information and coordinate responses to the attack.
Cybersecurity Best Practices and Vulnerability Patching, Wannacry attack source publicly named north korea
The Wannacry attack highlighted the critical importance of cybersecurity best practices and vulnerability patching. The attack exploited a vulnerability in Microsoft’s Windows operating system, which had been publicly disclosed months earlier. Organizations that had not patched the vulnerability were particularly vulnerable to the attack.
- Regularly patching software vulnerabilities is essential to prevent attackers from exploiting known weaknesses.
- Implementing strong passwords and multi-factor authentication can enhance security and prevent unauthorized access to systems.
- Regularly backing up data is crucial to minimize data loss in the event of an attack.
- Educating employees about cybersecurity threats and best practices is essential to prevent them from becoming targets of attacks.
Lessons Learned and Future Implications
The WannaCry attack served as a stark reminder of the vulnerability of our interconnected world to cyberattacks. It exposed critical weaknesses in cybersecurity practices and highlighted the need for a more proactive approach to mitigating future threats. This section delves into the lessons learned from the WannaCry attack, examines the evolving landscape of cyberattacks, and explores the potential implications for global security.
Cybersecurity Preparedness: A Critical Need
The WannaCry attack underscored the importance of robust cybersecurity preparedness. The attack exploited a vulnerability in Microsoft Windows, which had been patched by Microsoft months earlier. However, many organizations had failed to implement the patch, leaving themselves vulnerable.
- Patching and Updating Systems: The WannaCry attack emphasized the critical need for organizations to prioritize regular patching and updating of software. Outdated systems are prime targets for attackers who exploit known vulnerabilities. Organizations must adopt a proactive approach to software updates, ensuring that they are applied promptly and consistently.
- Network Segmentation: The attack highlighted the importance of network segmentation. By segmenting networks, organizations can limit the spread of malware in the event of a successful attack. This can help to contain the damage and prevent the compromise of critical systems.
- Backup and Recovery: The WannaCry attack demonstrated the importance of having robust backup and recovery plans in place. Many organizations were unable to recover from the attack because they lacked adequate backups or their backups were compromised. Organizations should ensure that they have multiple backups stored offline and regularly test their recovery plans.
- Security Awareness Training: The WannaCry attack highlighted the importance of security awareness training for employees. Many users fell victim to the attack because they clicked on malicious links or opened infected attachments. Organizations should invest in comprehensive security awareness training programs to educate employees about the latest threats and best practices for protecting themselves and their data.
The Evolving Nature of Cyberattacks
The WannaCry attack was a significant event, but it was just one example of the ever-evolving nature of cyberattacks. Attackers are constantly developing new techniques and tools, making it increasingly difficult to defend against their attacks.
- Sophistication of Attacks: Cyberattacks are becoming increasingly sophisticated. Attackers are using advanced techniques, such as artificial intelligence (AI) and machine learning, to automate their attacks and evade detection. This makes it more difficult to identify and respond to threats in a timely manner.
- Targeting of Critical Infrastructure: Attackers are increasingly targeting critical infrastructure, such as power grids, transportation systems, and healthcare facilities. These attacks can have a significant impact on the economy and public safety.
- Use of Ransomware: Ransomware attacks, like WannaCry, have become increasingly common. Attackers use ransomware to encrypt victims’ data and demand payment for its release. This can be extremely disruptive to businesses and individuals.
- Nation-State Actors: Nation-state actors are increasingly involved in cyberwarfare. These actors have the resources and expertise to carry out sophisticated and destructive attacks. They are also more likely to engage in espionage and other forms of cybercrime.
Attribution of Cyberattacks: A Complex Challenge
Attributing cyberattacks to specific actors is a complex and challenging task. Attackers often use sophisticated techniques to disguise their identities and origins. This makes it difficult to gather evidence that can definitively link an attack to a particular actor.
- Technical Analysis: Technical analysis can provide valuable insights into the tools and techniques used in an attack. However, this information alone is often not sufficient to identify the attacker. Attackers can use readily available tools and techniques, making it difficult to distinguish them from other actors.
- Intelligence Gathering: Intelligence gathering can play a crucial role in attributing cyberattacks. This involves collecting information from various sources, such as open-source intelligence, signals intelligence, and human intelligence. However, intelligence gathering can be time-consuming and resource-intensive.
- Political Considerations: Political considerations can also influence the attribution of cyberattacks. Governments may be reluctant to publicly attribute attacks to their adversaries for fear of escalating tensions or jeopardizing diplomatic relations.
The Future of Cyberwarfare: A Growing Threat
Cyberwarfare is a growing threat to global security. As technology continues to advance, cyberattacks are becoming more sophisticated and destructive. The potential for cyberattacks to disrupt critical infrastructure, cripple economies, and destabilize governments is increasing.
- Increased Reliance on Technology: Our increasing reliance on technology makes us more vulnerable to cyberattacks. As we become more interconnected and reliant on critical infrastructure, the potential impact of cyberattacks grows.
- Rise of AI and Machine Learning: The rise of AI and machine learning is likely to further exacerbate the threat of cyberwarfare. These technologies can be used to automate attacks, making them more efficient and effective.
- Blurred Lines Between Cybercrime and Cyberwarfare: The lines between cybercrime and cyberwarfare are becoming increasingly blurred. Criminal organizations are increasingly using tactics and tools that were once associated with nation-state actors.
Wannacry attack source publicly named north korea – The Wannacry attack served as a stark reminder of the growing threat of cyberwarfare. It highlighted the importance of cybersecurity preparedness, the need for robust defenses, and the critical role of international cooperation in combating these threats. While the attack was a significant setback, it also sparked a global conversation about cybersecurity, leading to increased awareness and a renewed focus on strengthening defenses. The world, however, is still grappling with the evolving landscape of cybercrime and the potential for future attacks. As technology advances, so too will the sophistication of cyberattacks, demanding constant vigilance and innovation in our defenses. The fight against cybercrime is a continuous battle, and the Wannacry attack serves as a potent reminder that we must be prepared for the next digital onslaught.
Remember the WannaCry attack? The one that shook the internet and was publicly attributed to North Korea? Well, it’s a good reminder that security is paramount, and that’s why it’s great to see that iOS 10 is installed on 48 percent of devices. This means that a significant chunk of Apple users are running a relatively secure operating system, which is good news in the face of potential threats like WannaCry.
 Standi Techno News
Standi Techno News