Initial Assessment
The first step for an elite hacker upon encountering an iMac is to conduct a thorough initial assessment. This involves analyzing the system’s vulnerabilities, the user’s security practices, and identifying potential entry points.
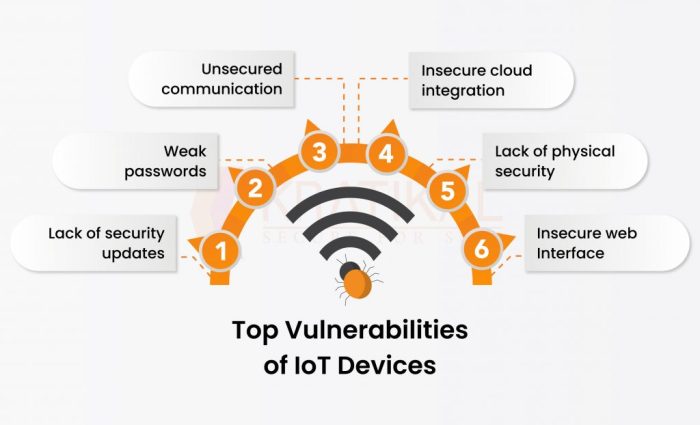
Identifying Potential Vulnerabilities
The hacker will first focus on identifying potential vulnerabilities in the iMac’s operating system and software. This can involve:
- Checking for outdated software: The hacker will look for any outdated operating systems, applications, or plugins, as these often contain known security flaws.
- Searching for known vulnerabilities: The hacker will use various tools and databases to search for publicly known vulnerabilities in the iMac’s software.
- Analyzing network configurations: The hacker will investigate the iMac’s network settings, looking for misconfigured firewall rules, open ports, or other vulnerabilities that could be exploited.
Analyzing User Security Practices
The hacker will also analyze the user’s security practices, looking for any potential weaknesses. This includes:
- Password strength: The hacker will try to determine the strength of the user’s passwords, as weak passwords can be easily cracked.
- Use of security software: The hacker will check if the user has installed and updated anti-virus and anti-malware software.
- Social engineering: The hacker might attempt to gather information about the user through social media or other online sources, which could be used to exploit their vulnerabilities.
Methods to Gain Initial Access
After assessing the vulnerabilities and security practices, the hacker will choose a method to gain initial access to the iMac. Some common methods include:
- Exploiting known vulnerabilities: If the hacker finds a known vulnerability in the iMac’s software, they can exploit it to gain access.
- Phishing attacks: The hacker might send a phishing email or message that tricks the user into clicking a malicious link or downloading a file.
- Brute-force attacks: The hacker could try to guess the user’s password by attempting various combinations.
- Social engineering: The hacker might try to trick the user into giving them access to the iMac by pretending to be a legitimate source.
Exploiting Vulnerabilities
After a thorough initial assessment, the next step for an elite hacker is to identify and exploit vulnerabilities in the macOS system. This involves leveraging weaknesses in the operating system, applications, or network configurations to gain unauthorized access or control.
Techniques for Exploiting Vulnerabilities
Exploiting vulnerabilities involves various techniques, ranging from simple to highly sophisticated. Here’s a breakdown of the most common methods:
- Code Injection: This technique involves introducing malicious code into a vulnerable application, causing it to execute the hacker’s commands. This could be achieved through buffer overflows, SQL injection, or cross-site scripting (XSS) attacks.
- Remote Code Execution (RCE): RCE exploits allow attackers to execute arbitrary code on a remote system. This often occurs through vulnerabilities in web servers, network protocols, or applications.
- Privilege Escalation: Once a hacker gains access to a system, they may attempt to elevate their privileges to gain administrative control. This can be done by exploiting vulnerabilities in the operating system or by using social engineering techniques.
- Denial-of-Service (DoS) Attacks: These attacks aim to disrupt or disable a system or service by overwhelming it with requests or data. DoS attacks can be used to prevent legitimate users from accessing the system or to extract information from the target.
Common Exploits Used Against macOS Systems
macOS systems, while generally considered secure, are not immune to vulnerabilities. Here are some common exploits that have been used against macOS systems:
- Zero-day exploits: These exploits target previously unknown vulnerabilities in the operating system or applications. Zero-day exploits are particularly dangerous because there is no patch available to fix them.
- Kernel vulnerabilities: The macOS kernel is responsible for managing the system’s core functions. Vulnerabilities in the kernel can allow attackers to gain root access to the system, giving them complete control.
- Web browser vulnerabilities: Web browsers are a common target for attackers because they often contain vulnerabilities that can be exploited to gain access to the user’s computer.
- Application vulnerabilities: Applications, such as email clients, web browsers, and productivity software, can also contain vulnerabilities that can be exploited by attackers.
Examples of Specific Vulnerabilities and Their Exploitation Methods
Several vulnerabilities have been discovered in macOS systems over the years, with varying degrees of impact. Here are some examples:
- CVE-2019-6284: This vulnerability in the macOS kernel allowed attackers to gain root access to the system by exploiting a flaw in the “sandbox” security mechanism. This vulnerability was patched by Apple in macOS 10.14.5.
- CVE-2020-17087: This vulnerability in the macOS “Font Book” application allowed attackers to execute arbitrary code on the victim’s computer by exploiting a flaw in the way the application handled font files. This vulnerability was patched by Apple in macOS 10.15.6.
- CVE-2021-30665: This vulnerability in the macOS “Safari” web browser allowed attackers to gain access to the user’s computer by exploiting a flaw in the way the browser handled web pages. This vulnerability was patched by Apple in macOS 11.4.
Information Gathering
After successfully gaining access to the iMac, the next step for an elite hacker is to gather as much information as possible about the target system and its user. This information can be used to further exploit vulnerabilities, steal sensitive data, or even launch more sophisticated attacks.
Gathering Information about the iMac
Information about the iMac itself is crucial. This includes details like the operating system version, installed software, network configuration, and connected peripherals.
- System Information: The hacker can use tools like `system_profiler` or `sw_vers` to gather information about the iMac’s hardware and software. This includes the model, processor, memory, storage capacity, and operating system version.
- Network Configuration: Network information like IP address, subnet mask, default gateway, and DNS servers can be obtained using commands like `ifconfig` or `ipconfig`. This helps the hacker understand the network environment and identify potential entry points.
- Installed Software: By listing the installed applications using commands like `ls -l /Applications` or `pkgutil –list`, the hacker can identify potential vulnerabilities associated with specific software versions.
- Connected Peripherals: Information about connected devices like printers, external drives, and network shares can be obtained using tools like `lsusb` or `lsblk`. This can help the hacker identify potential attack vectors or valuable data stored on these peripherals.
Gathering Information about the User
Information about the iMac’s user can be extremely valuable for targeted attacks. This includes details like usernames, passwords, browsing history, email accounts, and personal files.
- Password Recovery: Hackers can attempt to recover passwords using various techniques, including brute-force attacks, dictionary attacks, or password cracking tools. This can involve exploiting weak passwords or using password managers to extract stored credentials.
- File System Exploration: By navigating the user’s file system, the hacker can gain access to sensitive data like documents, images, emails, and browser history. This can be done using tools like `find` or `grep` to search for specific file types or s.
- Keyloggers: Keyloggers can be used to record every keystroke made on the iMac, allowing the hacker to capture passwords, credit card details, and other sensitive information. Keyloggers can be installed secretly or disguised as legitimate software.
- Browser Data: The hacker can access the user’s browsing history, cookies, and saved passwords from browsers like Safari or Chrome. This information can be used to steal personal information or track the user’s online activities.
Using Tools for Information Gathering
Hackers use a variety of tools and techniques to gather information about the iMac and its user. Some common tools include:
- Nmap: A powerful network scanning tool that can identify open ports, services running on the iMac, and potential vulnerabilities.
- Burp Suite: A web security tool that can intercept and analyze network traffic, allowing the hacker to identify and exploit vulnerabilities in web applications.
- Wireshark: A network packet analyzer that can capture and analyze all network traffic passing through the iMac, revealing sensitive information like passwords, usernames, and website URLs.
- Metasploit: A penetration testing framework that includes a vast library of exploits and tools for gathering information, exploiting vulnerabilities, and maintaining access to the target system.
Maintaining Access
After successfully exploiting vulnerabilities and gathering information, the next step for an elite hacker is to establish persistent access to the iMac. This involves implementing methods that allow them to maintain control over the system even after the initial attack has ended. This access can be used for various purposes, including data exfiltration, further reconnaissance, or even launching future attacks.
Backdoor Creation
Creating backdoors is a common tactic for maintaining persistent access. A backdoor is a hidden entry point into a system that allows access without going through the usual security measures.
* Reverse Shells: These are a common method of creating backdoors. They involve establishing a connection from the target system back to the attacker’s server, allowing the attacker to control the system remotely.
* Trojan Horses: This involves disguising malicious code as legitimate software. When the user installs the Trojan horse, it creates a backdoor, allowing the attacker to access the system.
* Rootkits: These are programs that hide themselves within the operating system, making them difficult to detect. They can be used to create backdoors and maintain access without detection.
Bypass Security Measures
Elite hackers often employ various techniques to bypass security measures and maintain access. These techniques can range from exploiting known vulnerabilities to creating custom tools and scripts.
* Disabling Security Software: Elite hackers may attempt to disable or circumvent security software, such as antivirus programs and firewalls, to prevent detection.
* Credential Harvesting: They may try to steal login credentials, such as usernames and passwords, to gain access to the system.
* Exploiting System Weaknesses: They may exploit vulnerabilities in the operating system or applications to gain access and maintain control.
Stealthy Access
Maintaining access without detection is crucial for elite hackers. This involves using techniques that minimize their footprint and avoid raising alarms.
* Using Legitimate Software: Hackers may use legitimate software, such as remote administration tools, to access the system without raising suspicion.
* Minimizing Network Traffic: They may try to minimize network traffic generated by their activities to avoid detection by security systems.
* Using Obfuscation: Hackers may use obfuscation techniques to disguise their malicious code, making it difficult to detect.
* Timing Attacks: They may exploit the timing of their actions to avoid detection. For instance, they may choose to operate during off-peak hours when security systems are less likely to be active.
Escalating Privileges
Once an elite hacker has gained initial access to an iMac, the next step is to escalate privileges. This means gaining higher-level access, often referred to as root access, which allows the hacker to control the entire system. This section delves into the methods used to bypass user account restrictions and achieve complete control over the iMac.
Bypassing User Account Restrictions
Bypassing user account restrictions is a crucial step in escalating privileges. Hackers employ various techniques to circumvent these limitations, including:
- Exploiting Known Vulnerabilities: Hackers leverage known vulnerabilities in the operating system or applications to gain elevated privileges. For instance, a vulnerability in a specific version of macOS could allow them to execute code with root privileges. This often involves exploiting unpatched software or system flaws.
- Password Cracking: If the user’s password is weak or easily guessable, hackers might attempt to crack it using brute-force attacks or dictionary attacks. This involves systematically trying different password combinations until the correct one is found.
- Social Engineering: Hackers can use social engineering techniques to trick users into providing their passwords or granting them access to sensitive information. This might involve phishing emails, fake websites, or impersonating trusted individuals.
- Using System Utilities: Some system utilities, like the “sudo” command, allow users to execute commands with elevated privileges. Hackers can exploit these utilities by manipulating their settings or using them in unexpected ways.
Exploiting System Utilities
System utilities like “sudo” provide legitimate ways to elevate privileges. However, hackers can manipulate these utilities to gain unauthorized access.
“The ‘sudo’ command allows users to execute commands with root privileges. Hackers might exploit this by using a vulnerability in the ‘sudo’ command itself or by tricking users into executing malicious commands with ‘sudo’.”
Gaining Root Access
Once user account restrictions are bypassed, the next goal is to gain root access. This involves obtaining the highest level of privileges on the iMac, allowing the hacker to control the entire system.
- Exploiting System Vulnerabilities: Hackers can leverage known vulnerabilities in the operating system or specific applications to gain root access. This often involves exploiting unpatched software or system flaws that allow them to execute code with root privileges.
- Using Rootkits: Rootkits are malicious software designed to hide their presence and grant hackers persistent root access. They can modify system files and processes, making it difficult to detect and remove them.
- Exploiting Privilege Escalation Vulnerabilities: Some applications or system utilities may contain vulnerabilities that allow a user with limited privileges to escalate to root access. These vulnerabilities often involve misconfigurations or logic errors in the code.
Data Exfiltration
The final stage in a successful hack is extracting the stolen data from the iMac. This process requires careful planning and execution to avoid detection and ensure the data is successfully transferred to the hacker’s control.
Methods for Data Exfiltration
The methods used to exfiltrate data from a compromised iMac vary depending on the hacker’s resources, the target’s security measures, and the size of the data being stolen.
- Email: This is a common method for exfiltrating small amounts of data. The hacker can use a compromised email account or create a new one to send the stolen data to themselves or a designated server.
- File Transfer Protocol (FTP): FTP is a standard protocol for transferring files between computers. Hackers can use FTP to upload stolen data to a remote server under their control.
- Cloud Storage: Services like Dropbox, Google Drive, and OneDrive offer convenient ways to store and share files. Hackers can use these services to upload stolen data and access it from anywhere.
- Remote Access Tools: Tools like TeamViewer and AnyDesk allow remote access to a computer. Hackers can use these tools to access the iMac remotely and download the stolen data.
- Steganography: This technique involves hiding data within other files, like images or audio files. This makes it difficult for security software to detect the exfiltrated data.
Hiding and Disguising Exfiltrated Data
Hackers employ various techniques to hide and disguise exfiltrated data, making it harder for security measures to detect and prevent its transfer.
- Encryption: Encryption scrambles data, making it unreadable without the decryption key. Hackers use strong encryption algorithms to protect stolen data during transmission.
- Data Segmentation: Large data files are broken down into smaller segments, making them less conspicuous and easier to transmit in multiple stages.
- Data Compression: Compressing data reduces its size, allowing for faster transmission and making it less likely to trigger security alarms.
- Data Obfuscation: This technique involves modifying the data’s appearance, making it difficult to identify as valuable information. For example, they might replace characters with random symbols or change the file format.
Examples of Data Exfiltration Methods
Here are some real-world examples of how hackers have used different data exfiltration methods to steal sensitive information.
- In 2014, the Sony Pictures hack involved the theft of terabytes of data, including confidential emails, scripts, and financial records. The hackers used a combination of malware and remote access tools to exfiltrate the data, which was later leaked online.
- The 2017 Equifax data breach affected millions of individuals. The hackers exploited a vulnerability in Equifax’s web server to gain access to sensitive data, including Social Security numbers, credit card details, and driver’s license information. They exfiltrated the data using a custom-built malware program.
Covering Tracks
After successfully infiltrating the iMac and achieving their objectives, elite hackers understand the importance of leaving no trace of their intrusion. The goal is to ensure their actions remain undetected, minimizing the risk of exposure and potential consequences.
Removing Logs and Evidence
The primary objective is to erase any evidence of their presence from the system’s logs. This includes eliminating system activity logs, application logs, and any other records that might reveal their actions.
- Deleting System Logs: Elite hackers utilize a range of techniques to delete system logs, including command-line tools like `logadm` and `syslogd` on macOS. They might also employ custom scripts to automate the process, ensuring a thorough removal of log entries.
- Manipulating Logs: Instead of deleting logs entirely, hackers may choose to manipulate them to conceal their activities. They might alter timestamps, replace log entries with fabricated data, or even redirect log files to hidden locations.
- Disabling Logging: In some cases, hackers might temporarily disable system logging to prevent any record of their actions from being created. However, this approach is risky as it could trigger alerts or raise suspicions if the system administrator notices the change.
Minimizing the Risk of Detection
Beyond log manipulation, elite hackers employ various techniques to minimize the risk of detection.
- Using Rootkits: Rootkits are sets of tools designed to hide malicious software from detection by security tools. They can modify the system’s operating system kernel to conceal their presence and prevent the removal of malicious files.
- Network Obfuscation: Hackers might use techniques to obscure their network traffic, making it difficult to identify their activities. This could involve using VPNs, proxies, or TOR networks to mask their IP addresses and encrypt their communications.
- Deleting Temporary Files: Elite hackers understand the importance of cleaning up temporary files, cache, and browsing history. These files often contain valuable information about their activities and could be used to trace their actions.
- Overwriting Disk Space: In extreme cases, hackers might overwrite free disk space with random data to prevent forensic analysis. This makes it difficult to recover deleted files or identify the presence of malicious software.
Ethical Considerations: What Elite Hackers Do Upon Encountering An Imac
Hacking an iMac, even if done for educational or research purposes, raises ethical concerns. While the technical aspects of hacking are fascinating, it’s crucial to consider the potential consequences of unauthorized access, especially when it involves personal data or sensitive information.
The legal consequences of unauthorized access to an iMac can be severe, depending on the specific circumstances and the intent behind the actions. Here’s a breakdown of potential legal implications:
Unauthorized access to a computer system is a crime in most countries.
- Violation of Privacy: Accessing someone’s personal files, emails, or browsing history without their consent is a clear violation of their privacy, potentially leading to legal action.
- Data Theft: Stealing personal information, financial data, or intellectual property can result in criminal charges, including identity theft and fraud.
- System Damage: Intentionally causing harm to a computer system or network can result in serious legal consequences, including fines and imprisonment.
- Civil Lawsuits: Victims of hacking may pursue civil lawsuits for damages caused by unauthorized access, including financial losses and emotional distress.
Ethical Hacking for Security Purposes, What elite hackers do upon encountering an imac
Ethical hacking, also known as penetration testing, is a legitimate practice used by security professionals to identify and exploit vulnerabilities in computer systems. This process helps organizations improve their security posture and prevent malicious attacks.
- Vulnerability Assessment: Ethical hackers conduct comprehensive security assessments to identify weaknesses in systems, applications, and networks.
- Penetration Testing: Ethical hackers simulate real-world attacks to test the effectiveness of security controls and identify potential entry points for malicious actors.
- Security Audits: Ethical hackers perform regular security audits to ensure compliance with industry standards and best practices.
- Bug Bounty Programs: Organizations offer rewards to ethical hackers who identify and report vulnerabilities in their systems, incentivizing responsible disclosure.
What elite hackers do upon encountering an imac – In the realm of cybersecurity, the encounter between an elite hacker and an iMac is a complex dance of skill and strategy. It’s a clash of intellect, where the hacker’s ability to exploit vulnerabilities is met with the user’s efforts to protect their digital assets. The story of this encounter is a reminder that vigilance and proactive security measures are crucial in today’s interconnected world. By understanding the methods and motivations behind these attacks, we can better safeguard our digital lives and ensure that our data remains secure.
Elite hackers, those digital ninjas, often scoff at the sight of an iMac, seeing it as a sleek but ultimately limited device. However, their disdain might momentarily shift to curiosity if they find a hidden gem: a Windows XP machine tucked away, perhaps running some legacy software. After all, even in this age of advanced operating systems, Windows XP still holds the No.
2 spot in terms of popularity, according to a recent study. This enduring legacy could provide a gateway to vulnerabilities, making even the most seasoned hacker pause and consider their next move.
 Standi Techno News
Standi Techno News