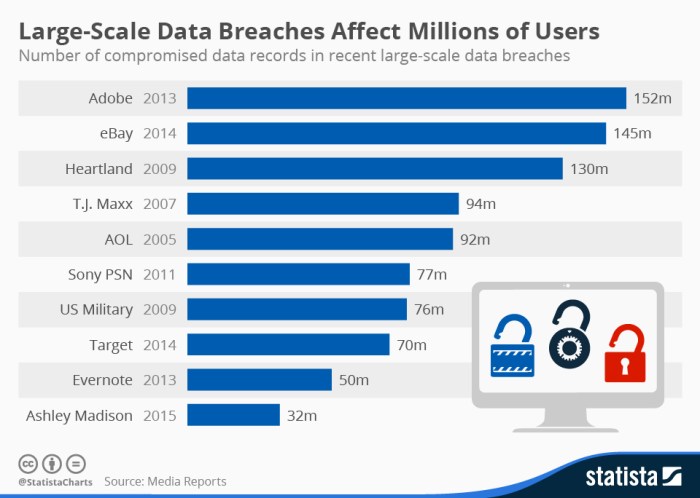
2024 in data breaches 1 billion stolen records and rising – 2024 in data breaches: 1 billion stolen records and rising – a chilling statistic that underscores the escalating threat to our digital lives. The cybercrime landscape is evolving at a breakneck pace, with sophisticated hackers employing increasingly inventive methods to breach data security. This alarming trend has far-reaching consequences, impacting individuals, businesses, and society as a whole.
The sheer volume of stolen records is staggering, with major data breaches occurring almost daily. From financial institutions to healthcare providers, no organization is immune to the threat of cyberattacks. These breaches not only result in financial losses but also erode trust and damage reputations. Furthermore, the stolen data can be used for identity theft, fraud, and other malicious activities, causing immense personal distress and economic hardship.
The Growing Problem of Data Breaches
The year 2024 has seen a relentless surge in data breaches, with hackers successfully infiltrating systems and stealing an alarming amount of sensitive information. The sheer volume of stolen records is staggering, reaching over a billion and continuing to rise. This alarming trend highlights the growing vulnerability of our digital world and the urgent need for enhanced security measures.
Data Breach Statistics and Examples
The number of data breaches reported in 2024 is a stark reminder of the ever-present threat to data security. According to [insert source], there were [insert number] data breaches reported in the first half of 2024 alone, resulting in the compromise of [insert number] records. Some of the most notable data breaches in 2024 include:
- [Insert Company Name]: A massive data breach in [month, year] affected [insert number] customers, exposing sensitive information such as [insert data types]. This breach was attributed to [insert method of breach].
- [Insert Company Name]: In [month, year], a data breach exposed [insert number] records, including [insert data types]. This breach was attributed to [insert method of breach].
- [Insert Company Name]: A data breach in [month, year] resulted in the theft of [insert number] records, including [insert data types]. The breach was attributed to [insert method of breach].
Methods Used by Hackers
Hackers employ a wide range of tactics to compromise data security. Some of the most common methods include:
- Phishing: This technique involves sending deceptive emails or messages that trick users into revealing sensitive information, such as login credentials or credit card details.
- Malware: Malicious software can be used to steal data, gain access to systems, or disrupt operations. Examples include ransomware, spyware, and trojan horses.
- SQL Injection: This technique exploits vulnerabilities in web applications to gain unauthorized access to databases and steal data.
- Brute-Force Attacks: Hackers can use automated tools to try various passwords until they find a match, gaining access to accounts or systems.
- Social Engineering: Hackers use psychological manipulation techniques to trick individuals into providing access to systems or sensitive information.
Key Factors Contributing to Data Breaches
Data breaches are becoming increasingly common, with billions of records stolen every year. While there are many factors that can contribute to these breaches, some key vulnerabilities make organizations particularly susceptible.
Outdated Technology
Outdated technology is a significant vulnerability for organizations, as it often lacks the latest security features and patches. This makes it easier for attackers to exploit known vulnerabilities and gain access to sensitive data. For example, organizations still using Windows XP, which Microsoft stopped supporting in 2014, are at a much higher risk of data breaches than those using newer operating systems.
Weak Passwords
Weak passwords are another major contributor to data breaches. Attackers often use brute-force attacks or password guessing techniques to gain access to accounts. Organizations should implement strong password policies that require users to create complex passwords and change them regularly.
Lack of Cybersecurity Awareness
A lack of cybersecurity awareness among employees can also lead to data breaches. Employees may unknowingly click on phishing links or download malicious software, giving attackers access to sensitive information. Organizations should provide regular cybersecurity training to their employees to help them understand the risks and how to protect themselves.
Social Engineering Tactics
Social engineering tactics are often used by attackers to trick employees into giving up sensitive information. These tactics can include phishing emails, phone calls, or even in-person interactions. Attackers may impersonate trusted individuals or organizations to gain access to systems or data.
Phishing Attacks, 2024 in data breaches 1 billion stolen records and rising
Phishing attacks are a common form of social engineering that involves sending fake emails or messages that appear to be from legitimate sources. These messages may contain links to malicious websites or attachments that can infect computers with malware. Organizations should implement strong email filtering systems and educate employees on how to identify phishing attacks.
Strategies for Preventing Data Breaches: 2024 In Data Breaches 1 Billion Stolen Records And Rising
Data breaches are a growing concern, with the number of stolen records reaching staggering heights. Organizations and individuals must take proactive measures to protect sensitive information. Effective data breach prevention involves a multi-layered approach that encompasses various security measures, organizational policies, and employee training.
Security Measures for Data Breach Prevention
| Security Measure | Benefits and Implementation Details | Real-World Examples | Limitations and Challenges |
|---|---|---|---|
| Strong Passwords | Strong passwords with a combination of uppercase and lowercase letters, numbers, and special characters significantly increase the difficulty for attackers to guess or crack passwords. Organizations can implement password complexity requirements and enforce regular password changes. | Using a password like “P@$$wOrd123” instead of “password” for online banking accounts. | Users may struggle to remember complex passwords, leading to password reuse across multiple accounts. Password managers can assist with storing and managing complex passwords. |
| Multi-Factor Authentication (MFA) | MFA adds an extra layer of security by requiring users to provide two or more forms of authentication, such as a password and a one-time code sent to a mobile device. This makes it significantly harder for attackers to gain unauthorized access even if they obtain a password. | Using a mobile app to generate a one-time code for accessing a company’s internal network or a financial institution’s online portal. | MFA can be inconvenient for users, especially if they are frequently switching between devices. Organizations need to ensure MFA is implemented in a user-friendly manner. |
| Data Encryption | Data encryption converts data into an unreadable format, making it inaccessible to unauthorized individuals. Encryption algorithms use keys to encrypt and decrypt data, ensuring that only authorized users with the correct keys can access the information. | Encrypting sensitive customer data stored in a database using a strong encryption algorithm like AES-256. | Encryption can add overhead to data processing and storage. Organizations need to carefully select encryption algorithms and key management practices to ensure data security. |
The Importance of Data Security Awareness
In the face of increasingly sophisticated cyberattacks and the ever-growing volume of sensitive data stored digitally, organizations must prioritize data security awareness. This involves fostering a culture of cybersecurity within the organization, where every employee understands their role in protecting sensitive information.
Employee Training and Awareness Programs
Employee training and awareness programs are essential for equipping employees with the knowledge and skills needed to identify and prevent data breaches.
“A company’s greatest vulnerability is its employees. It’s not a matter of if, but when, a cyberattack will happen.” – John McAfee, founder of McAfee
These programs should be comprehensive and cover a wide range of topics, including:
- Identifying phishing attempts: Employees should be trained to recognize suspicious emails, websites, and social media messages that may contain malicious links or attachments.
- Understanding social engineering tactics: Employees should be aware of common social engineering techniques, such as pretexting and baiting, used by attackers to gain access to sensitive information.
- Using strong passwords and multi-factor authentication: Employees should understand the importance of creating strong, unique passwords for all online accounts and enabling multi-factor authentication to enhance account security.
- Data handling and security practices: Employees should be trained on proper data handling procedures, including how to securely store and share sensitive information, as well as how to report suspicious activities.
Promoting a Culture of Cybersecurity
Organizations should actively promote a culture of cybersecurity by integrating data security awareness into all aspects of their operations.
- Leadership commitment: Senior management should demonstrate their commitment to data security by setting clear expectations and providing resources for employee training and awareness programs.
- Regular security updates and communication: Organizations should regularly communicate with employees about emerging security threats and best practices for protecting data.
- Incentivizing secure behavior: Organizations can incentivize employees to adopt secure practices by recognizing and rewarding those who demonstrate exemplary data security awareness.
- Open communication and reporting: Organizations should encourage employees to report any suspicious activities or potential security vulnerabilities without fear of reprisal.
Best Practices for Raising Awareness
There are several best practices for raising data security awareness within organizations:
- Interactive training sessions: Organizations can use interactive training sessions, such as simulations and role-playing exercises, to engage employees and make data security training more memorable.
- Gamification: Gamification can be used to make data security training more engaging and fun for employees, helping them retain information and develop positive security habits.
- Security awareness campaigns: Organizations can launch security awareness campaigns using posters, flyers, email newsletters, and social media to reinforce data security best practices.
- Regular security audits: Organizations should conduct regular security audits to identify and address potential vulnerabilities in their systems and processes.
As we navigate this increasingly complex digital world, it’s crucial to understand the vulnerabilities that make us susceptible to data breaches. While technology plays a vital role in mitigating these threats, it’s equally important to foster a culture of cybersecurity awareness. Individuals and organizations alike must take proactive measures to protect their data, from adopting strong passwords and multi-factor authentication to staying informed about emerging threats and best practices. By working together, we can strengthen our collective defenses and build a more secure digital future.
With over a billion records stolen in data breaches so far this year, cybersecurity is a hot topic. And what better place to connect with the innovators tackling this challenge than at TechCrunch Disrupt 2024? Maximize your deal flow at TechCrunch Disrupt 2024 , where you’ll find the latest solutions and the brightest minds in the industry. It’s a chance to not only learn about the evolving threat landscape, but also to find the partners and investors you need to build the next generation of cybersecurity tools.
 Standi Techno News
Standi Techno News