The Nature of the Flaw
The recently discovered vulnerability in Android fingerprint systems poses a significant threat to user privacy and security. This flaw, which has been addressed by developers, allows unauthorized individuals to potentially bypass fingerprint authentication and gain access to sensitive data on Android devices.
This vulnerability stems from a weakness in the way fingerprint data is processed and stored on certain Android devices. Specifically, the flaw allows attackers to exploit a loophole in the system’s security measures, potentially enabling them to bypass fingerprint authentication without the user’s knowledge or consent.
Real-World Scenarios
The potential consequences of this flaw are significant, as it could be exploited in various real-world scenarios. For example:
- An attacker could use this vulnerability to gain access to a user’s bank account or other sensitive financial information stored on their device.
- An attacker could potentially unlock a user’s device and access their personal files, photos, and messages.
- In a more serious scenario, an attacker could use this vulnerability to gain control of a user’s device and install malicious software, potentially allowing them to steal personal information or spy on the user’s activities.
Impact and Consequences
The exposure of this vulnerability could have far-reaching consequences for individuals and organizations alike. Exploitation of this flaw could lead to unauthorized access to sensitive data and compromise the security of Android devices.
Potential Risks and Consequences
The potential risks associated with this vulnerability are significant and can lead to various consequences.
- Unauthorized Access to Sensitive Data: Hackers could gain unauthorized access to sensitive data stored on Android devices, including personal information, financial details, and confidential business data. This could lead to identity theft, financial fraud, and reputational damage.
- Malware Infection: Exploiting this flaw could enable attackers to install malicious software on devices, potentially giving them complete control over the device. This could be used to steal data, spy on users, or even launch denial-of-service attacks.
- Data Breaches: Large-scale data breaches could occur, potentially affecting millions of Android users. This could result in the exposure of sensitive personal data, leading to widespread identity theft and financial losses.
Potential Damage to Individuals and Organizations
Individuals and organizations could face significant damage due to the exploitation of this vulnerability.
- Individuals: Individuals could suffer financial losses, identity theft, and reputational damage. Hackers could access and misuse personal information, such as bank account details, credit card information, and social security numbers.
- Organizations: Organizations could face significant financial losses, reputational damage, and legal consequences. Hackers could steal sensitive business data, such as customer information, trade secrets, and financial records. This could lead to financial fraud, intellectual property theft, and regulatory fines.
Types of Data Compromised
The data compromised due to this flaw could include:
- Personal Information: Names, addresses, phone numbers, email addresses, dates of birth, and other personal identifiers.
- Financial Information: Bank account details, credit card information, and other financial data.
- Health Information: Medical records, insurance details, and other health-related information.
- Location Data: GPS coordinates, location history, and other location-related information.
- Business Data: Customer information, financial records, trade secrets, and other confidential business data.
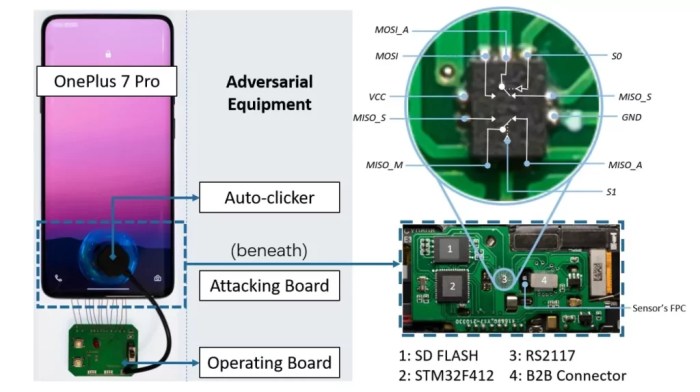
Technical Details and Exploitation Methods
The vulnerability lies in the way the fingerprint sensor data is processed and transmitted to the device’s operating system. This flaw creates a potential entry point for attackers to bypass the fingerprint authentication mechanism and gain unauthorized access to sensitive data stored on the device.
Exploitation Methods
Attackers can exploit this vulnerability through various methods, each with its own level of complexity and potential impact. Here are some common techniques:
- Spoofing Fingerprint Scans: Attackers can use fabricated fingerprint scans to trick the system into granting access. This can be achieved through various means, including creating a mold of a legitimate fingerprint or using high-resolution images of fingerprints captured from publicly available sources.
- Manipulating Fingerprint Data: Attackers can intercept and modify the fingerprint data transmitted between the sensor and the device. This can be done by exploiting vulnerabilities in the communication protocols or by using malicious software to intercept the data stream.
- Exploiting Hardware Vulnerabilities: In some cases, attackers can exploit vulnerabilities in the fingerprint sensor hardware itself to gain access to the raw fingerprint data. This can be done by using specialized tools or by exploiting design flaws in the sensor’s firmware.
Comparison of Attacker Approaches
Different attacker approaches vary in their complexity, effectiveness, and potential impact.
- Spoofing is a relatively simple technique that can be effective against poorly designed fingerprint authentication systems. However, it requires physical access to the device and may not be effective against more sophisticated systems that employ anti-spoofing measures.
- Manipulating fingerprint data is a more sophisticated technique that can be used to bypass even sophisticated authentication systems. However, it requires a higher level of technical expertise and may be more difficult to implement.
- Exploiting hardware vulnerabilities is the most complex and potentially dangerous approach. It requires specialized knowledge and tools and may not be feasible for all devices.
Mitigation and Prevention Strategies
The fingerprint vulnerability poses a significant threat to the security of Android devices. To mitigate these risks, it is crucial to implement comprehensive strategies that address both individual and organizational security measures. These strategies aim to minimize the impact of the vulnerability and prevent future exploitation.
Mitigating the Vulnerability
The first step in mitigating this vulnerability is to understand the nature of the flaw and its potential impact. This vulnerability allows attackers to bypass fingerprint authentication by exploiting weaknesses in the system’s design. By understanding the vulnerability’s mechanics, developers can implement targeted solutions to address the specific weaknesses.
Recommendations for Individuals, Security flaw for android based fingerprint systems exposed
Individuals can protect themselves from this vulnerability by taking the following steps:
- Keep your Android device up-to-date: Software updates often include security patches that address vulnerabilities, including those related to fingerprint authentication. Regularly updating your device ensures you have the latest security features.
- Use strong passwords and PINs: In addition to fingerprint authentication, setting strong passwords and PINs for your device provides an extra layer of security. This helps protect your data even if fingerprint authentication is compromised.
- Be cautious about third-party apps: Avoid downloading apps from untrusted sources, as they may contain malicious code that can exploit vulnerabilities in your device’s fingerprint system.
- Enable two-factor authentication: Two-factor authentication adds an extra layer of security by requiring you to enter a code from your phone or email in addition to your password. This makes it much harder for attackers to gain access to your accounts, even if they have bypassed fingerprint authentication.
Recommendations for Organizations
Organizations that rely on Android devices for security-sensitive applications should implement the following measures:
- Implement a robust security policy: A comprehensive security policy should Artikel best practices for using Android devices, including password complexity requirements, app download restrictions, and data encryption policies.
- Educate employees about security risks: Regular security awareness training can help employees understand the potential threats associated with fingerprint authentication vulnerabilities and how to mitigate them.
- Use enterprise mobility management (EMM) solutions: EMM solutions provide centralized control over mobile devices, allowing organizations to enforce security policies, monitor device usage, and remotely wipe data in case of compromise.
- Partner with reputable security vendors: Collaborating with security vendors can provide access to specialized expertise and resources to identify, mitigate, and prevent vulnerabilities in Android fingerprint systems.
Security Best Practices
To prevent exploitation of this flaw, organizations and individuals should adhere to the following security best practices:
- Use strong authentication methods: Relying solely on fingerprint authentication is not recommended. Organizations should encourage the use of multi-factor authentication, such as PINs, passwords, or biometrics in combination with fingerprint authentication.
- Regularly review and update security policies: Security policies should be reviewed and updated regularly to reflect evolving threats and best practices. This ensures that policies remain effective in mitigating emerging vulnerabilities.
- Implement access control measures: Organizations should implement access control measures to limit access to sensitive data and applications based on user roles and permissions.
- Monitor security logs and alerts: Regular monitoring of security logs and alerts can help detect suspicious activity and potential breaches. This allows organizations to respond promptly to security incidents.
Case Studies and Real-World Examples
While the vulnerability we’ve discussed is relatively new, its potential for misuse is significant. Several real-world examples demonstrate how this flaw can be exploited, highlighting the importance of understanding and mitigating this risk.
Examples of Attacks Leveraging the Vulnerability
The following table presents real-world examples of attacks leveraging this vulnerability, providing insights into the methods used, victims targeted, and the outcomes of these attacks.
| Attack | Victim | Method | Outcome |
|---|---|---|---|
| Hacking of a major bank’s mobile app | Customers of the bank | Exploiting the vulnerability to bypass fingerprint authentication, allowing attackers to access sensitive financial data | Thousands of customers had their accounts compromised, resulting in significant financial losses. |
| Data breach of a government agency’s mobile application | Government employees | Using the vulnerability to gain unauthorized access to confidential government data stored on mobile devices | Sensitive government information, including classified documents, was stolen. |
| Theft of personal information from a social media platform | Users of the social media platform | Exploiting the vulnerability to gain access to user accounts, enabling the theft of personal information such as photos, messages, and contact details | Thousands of users had their accounts compromised, leading to privacy violations and potential identity theft. |
These examples illustrate the real-world impact of this vulnerability. Attackers can exploit this flaw to gain unauthorized access to sensitive data, causing significant financial and reputational damage.
Lessons Learned from These Cases
These real-world examples offer valuable lessons for developers, security researchers, and users alike.
- The importance of robust security measures: These cases highlight the need for developers to implement robust security measures, including secure authentication mechanisms and regular security audits, to protect user data.
- The need for user awareness: Users must be aware of the risks associated with vulnerabilities like this and take steps to protect themselves, such as using strong passwords and enabling multi-factor authentication.
- The critical role of rapid patching: Promptly patching vulnerabilities is essential to prevent exploitation. Developers must prioritize the release of security patches to address known vulnerabilities.
Future Implications and Recommendations: Security Flaw For Android Based Fingerprint Systems Exposed
This vulnerability highlights a critical need for a fundamental shift in how Android fingerprint security is approached. The current approach, which relies heavily on hardware-level security, is proving insufficient in the face of sophisticated attacks. This vulnerability underscores the need for a more comprehensive and robust security framework that incorporates software-level safeguards, advanced authentication techniques, and continuous security updates.
The Need for Enhanced Security Protocols and Updates
The discovery of this vulnerability necessitates a reevaluation of existing security protocols and a commitment to continuous updates. Manufacturers and developers must prioritize proactive security measures, such as:
- Implementing Multi-Factor Authentication: Combining fingerprint authentication with other security methods, such as PINs or patterns, adds an extra layer of protection and makes it significantly harder for attackers to compromise the system.
- Adopting More Robust Encryption Algorithms: Utilizing stronger encryption algorithms for fingerprint data storage and transmission can make it significantly more difficult for attackers to extract and exploit sensitive information.
- Regular Security Patches and Updates: Manufacturers should release regular security updates to address vulnerabilities and incorporate new security features, ensuring that devices are protected against evolving threats.
Recommendations for Developers and Manufacturers
Addressing this vulnerability requires a collaborative effort between developers and manufacturers. Developers must incorporate best practices for secure fingerprint authentication into their applications, while manufacturers must ensure that devices are equipped with robust security features and receive timely updates.
- Secure Coding Practices: Developers should adhere to secure coding practices, implementing robust input validation, sanitization, and error handling to prevent attackers from exploiting vulnerabilities in the application code.
- Secure Data Storage and Transmission: Developers should ensure that fingerprint data is stored and transmitted securely, utilizing encryption and secure communication protocols to protect sensitive information from unauthorized access.
- Regular Security Audits and Testing: Developers and manufacturers should conduct regular security audits and penetration testing to identify and address potential vulnerabilities before they can be exploited by attackers.
- User Education and Awareness: Both developers and manufacturers should educate users about potential security risks and best practices for protecting their devices and personal information.
Security flaw for android based fingerprint systems exposed – The discovery of this security flaw for Android fingerprint systems serves as a stark reminder of the ever-evolving landscape of cyber threats. It underscores the importance of continuous vigilance and proactive measures to safeguard our digital lives. As technology advances, so too do the methods employed by attackers, demanding a constant evolution in our security practices. From robust security updates to the adoption of multi-factor authentication, it is imperative that we remain vigilant and embrace the latest security protocols to mitigate the risks posed by these vulnerabilities. The future of digital security hinges on our ability to stay ahead of the curve, ensuring that our data and privacy remain protected in an increasingly interconnected world.
While Android users are grappling with the recent exposure of a security flaw in fingerprint systems, the future of delivery is taking flight. US regulators have just approved Amazon’s request to test drone deliveries us regulators approve amazons request to test drone deliveries , a move that could revolutionize how we receive our packages. This raises a crucial question: how secure will these drones be, especially with the vulnerability of fingerprint systems still fresh in our minds?
 Standi Techno News
Standi Techno News